|
Getting your Trinity Audio player ready...
|
Some things in life are pretty obvious – nights are going to be dark, days are, by nature, bright and infostealers, well, steal information. No surprise there, right?
What may be less obvious and may actually come as a surprise is just how damaging this type of malware can be and the vast risks they can pose to organizations. In this blog, I’ll walk you through what infostealers are, how they work, how they get distributed, some examples of infostealers you may remember from the news and finally, how to protect your organization from them.
So let’s jump right in, shall we?
To start, let’s set some terms; infostealers are a type of malware that gathers and exfiltates sensitive information stored on devices. They can facilitate the initial foothold, allowing attackers to escalate privileges and gain access to critical assets. Functioning in a Malware-as-a-service (MaaS) model, criminals gather information and sell it as logs on dark web forums, Telegram channels, or via specialized sites like Russian Market or Genesis Market.
On these sites, logs can be sold for as low as $1, with prices reaching up to $150. Logs are a commodity for cybercriminals and the fact that they can be bought for a relative pittance is a sure fire reason why they are so common and thus, so dangerous.
Types of Information Infostealers go After
- Credentials stored in browsers like Google Chrome (from auto-fill, password cache etc.).
- Cookies that allow actors to access a user’s session and bypass 2FA.
- Files that contain financial information, secret keys (including cloud keys), 2FA backup codes, server passwords, crypto private keys and wallet data, etc.
- Personal data, like ID numbers, addresses, medical records, credit card numbers, DOB, etc.
The use of infostealers as a preferred method has been popular for many years and it continues to grow in popularity. And appallingly, the average credential has a 1 in 5 chance of already being stolen as part of an infostealer malware campaign. So in short, they pose a big – but like really big – problem.
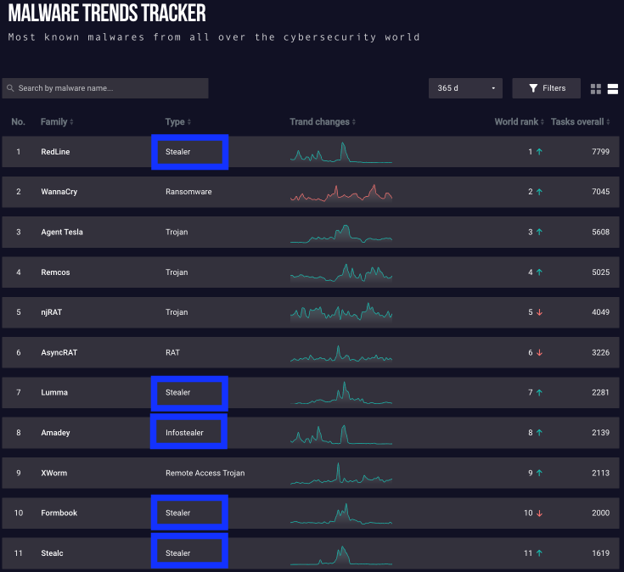
By looking at Any.run (sandbox) malware trends for the last year, you can see that the use of infostealers continues to rise and accounts for 46% of the malware available today.
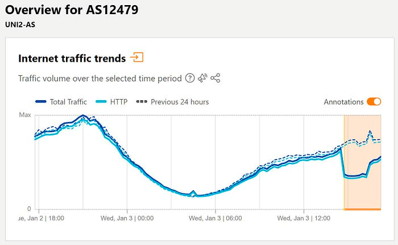
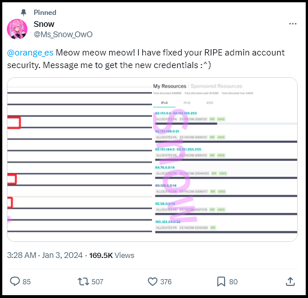
Spanish telecom giant Orange learned this the (very) hard way in early January when their credentials were stolen via an infostealer malware, leading to internet outages at customers. A hacker going by the name Snow exploited their RIPE (Regional Internet Registries) account, leading to a major internet outage. They then modified the AS number associated with the company’s IP addresses, and enabled an invalid RPKI configuration on them. Announcing the IP addresses on someone else’s AS number and then enabling RPKI effectively caused these IP addresses to no longer be announced properly on the internet.
The Infostealer Lifecycle
It all starts with malware developers writing and maintaining the code which is then packaged and sold on underground forums, typically to IABs – or initial access brokers – in a MaaS (Malware-as-a-Service) model. IABs are individuals or groups that rent access to tools from MaaS operators on underground forums and marketplaces. They then deploy these infostealers to infect systems. Infostealers steal data from the compromised system and exfiltrate it to a C2 server. The information is stored as Logs, which are available to buy in Telegram groups using subscriptions.
Common Infection Methods include:
- Infected Websites, Malicious Ads/Malvertising
- Phishing
- Downloaders, Droppers
Some common variants of infostealers you may have encountered include:
- Raccoon – Malware sold on a subscription basis. Steals data including browser autofill passwords, history, and cookies, usernames, passwords, credit cards, and cryptocurrency wallets.
- RedLine – Collects browser information like saved credentials, autocomplete data, and credit card information. Can upload and download files, execute commands, and send back information regarding the infected computer.
- Vidar – Gathers sensitive data from browsers and digital wallets and is used as a downloader for ransomware.
- Taurus – Sold on Russian forums with many capabilities, including stealing social media, VPN, and cryptocurrency credentials. Can take screenshots of the desktop and gather info on software installation and configuration information.
How to Block Infostealers
The question is this: what can be done to prevent infostealers from getting their grubby hands on your credentials?
- Use a Password Manager, but don’t keep its password in your browser
- Update your browser regularly to protect against:
– Java scripts in vulnerable browsers (malvertising) and 0-click infections
– Unofficial/fake/malicious browser extensions
- Inspect incoming emails for malware and file macros
- Do not download pirated app versions
- Do not open suspicious files or click suspicious links
- Only download software from trusted sources
Moreover, one of the best ways to block infostealers is with threat intel and exposed credential identification. These tools help identify compromised credentials with real-time dark web monitoring to prevent unauthorized access and data breaches. Threat Intel is an important component of the discovery stage of the Continuous Threat Exposure Management (CTEM) framework, something we’re big fans of here at XM Cyber.
Discovery in CTEM goes beyond mere identification of assets and vulnerabilities, encompassing a broad spectrum, including the detection of misconfigurations in assets and security controls, as well as exposures to identity and access threats such as exposed credentials and over permissions.
Identifying compromised credentials is a key part of Discovery, and therefore, a key element to comprehensively meeting CTEM. To learn more about how a CTEM program will help your organization reduce risk and improve security posture the continuous 5 stage framework, read our whitepaper here, XM Cyber on Operationalizing CTEM.


