Corrigez ce qui est important
Priorisez et corrigez
les expositions à haut risque plus rapidement
Expositions contextuellisées dans l’ensemble de votre surface d’attaque, pour savoir ce qu’il faut corriger en premier.
15,000 Exposition
Il s’agit du nombre moyen d’expositions qui requièrent votre attention chaque mois.
Que corrigez-vous en premier ?
IL EST TEMPS D’ADOPTER UNE NOUVELLE APPROCHE
Découvrez toutes les expositions, corrigez ce qui est vital
La plateforme de gestion continue des expositions de XM Cyber permet de s’affranchir des listes interminables, en fournissant un contexte graphique pour hiérarchiser les expositions qui mettent en danger les actifs critiques de votre entreprise. Obtenez une vue unifiée de l’ensemble de votre surface d’attaque, révélant comment les diverses expositions assemblées entre elles forment des chemins d’attaque. Grâce à un contexte basé sur les risques, vous pouvez identifier et corriger les expositions avec le meilleur retour sur investissement pour optimiser la posture de sécurité et améliorer l’efficacité des ressources.
Prévenez les attaques à fort impact
Sécurisez en permanence vos actifs critiques contre une combinaison de techniques d’attaque.
Gagnez en efficacité en matière de remédiation
Ne gaspillez plus de ressources sur des correctifs qui n’ont pas d’impact sur le risque. Remédiez à ce qui est le plus important.
Rapportez les
risques avérés
Répondez en toute confiance aux questions des dirigeants grâce à une compréhension commune des risques critiques pour l’entreprise.
XM Attack Graph Analysis™
Corrigez ce qui compte avec le contexte métier
XM Attack Graph Analysis™ vous fournit une vision claire et contextuelle de l’ensemble des expositions de votre surface d’attaque, qu’elle soit externe ou interne, à travers votre infrastructure hybride jusqu’à vos actifs métier critiques. Cette approche permet aux équipes Sécurité et IT de s’aligner sur un nombre minimal d’expositions prioritaires à traiter, garantissant ainsi une réduction optimale des risques et des résultats de sécurité maximisés.
Oser Changer D’approche
XM Cyber nommé Challenger dans le tout premier Gartner® Magic Quadrant™ 2025 pour les plateformes d’évaluation de l’exposition
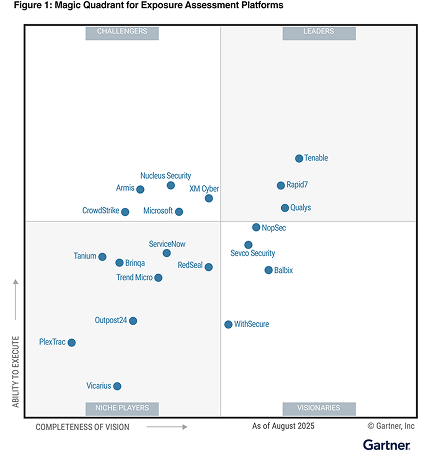
CAS D’USAGE
Sécurisez vos initiatives métier
Éliminez les risques sur l’ensemble de la surface d’attaque grâce à la gestion continue des expositions
Reporting des risques cyber
Risques liés à la chaîne d'approvisionnement et aux tiers
Audit et conformité
Sécurité du Cloud
Sécurité de l'Active Directory
Sécuriser l'OT
Évaluation des vulnérabilités
Validation automatisée de la sécurité
Gestion de la surface d'attaque externe
La solution la plus complète pour l’adoption du programme Continuous Threat Exposure Management (CTEM).
Adoptez et maintenez ce cadre de gestion continue de l’exposition aux menaces en fournissant l’évaluation et la validation de l’exposition dans une plate-forme unique.
Découvrez les cinq étapes du CTEM :
Ce que disent nos clients
-
“
The product is easy to deploy, easy to handle and configure, and gives great and important insights from the attacker׳s point of view.
IT Security and Risk Management – Manufacturing
-
“
This tool allows you to define quick-win remediation but, more importantly, focuses on compromising paths to its most critical assets.
IT Security and Risk Management –
Banking -
“
Best CTEM feature solution currently on the market. The usability and product features are innovative to me and work well.
IT Security & Risk management-
IT Services
Total Economic Impact Study™ of XM Cyber
394%
Return on investment, with payback in under 6 months
$12.4M
Reduction in remediation, fines, lost revenue, and brand reputation costs
$1.4M
Reduction in costs associated with penetration testing
90%
Reduction in the likelihood of experiencing severe breach
Êtes-vous prêt à vous attaquer aux bons enjeux