|
Getting your Trinity Audio player ready...
|
Last year, we introduced External Attack Surface Management (EASM) into the XM Continuous Exposure Management (CEM) platform. We knew then that identifying external risks was only the first step. Modern breaches are not isolated events; they are chains of interconnected exposures that cross boundaries, spanning from external internet-facing assets to on-premises workstations, through Active Directory, and deep into cloud workloads.
Recently, the market has become crowded with claims of end-to-end exposure management. While it is encouraging to see the industry acknowledge the need for convergence, there is a profound difference between visualizing a potential connection and truly validating an exploitable exposure.
This is exactly why today, we are delivering on our vision with enhanced capabilities for XM EASM, bridging the ‘outside-in’ perspective with your ‘inside-out’ reality, and moving beyond disjointed visibility to deliver a unified view of true risk. This integration makes XM Cyber the first vendor to provide a seamless, end-to-end approach to exposure management, using validated exploitable attack paths.
What’s New?
The XM Cyber Continuous Exposure Management (CEM) Platform now links the external attack surface directly to internal assets. Unlike other solutions that rely on static mapping and metadata matching, we achieve this by leveraging a proprietary, attacker-centric two-step validation process:
Agentic Validation of External Exposures:
First, the platform utilizes agentic AI to mimic real-world attacker behavior, actively verifying if an external exposure is truly exploitable in your specific environment. This instantly filters out false positives with the precision of an experienced pentester, ensuring you are looking at a confirmed breach point rather than a theoretical vulnerability.
End-to-End Kill Chain and Blast Radius Validation:
Second, the platform maps the consequences of a potential breach originating from an external exposure by combining two proprietary technical innovations: Digital Twin Modeling and Attack Graph Analysis™.
- Safe, Non-Intrusive Validation: The platform creates a Digital Twin, which is a virtual model of your interconnected systems, configurations, and identities that replicates your live production environment. This enables the platform to safely visualize and validate risks to business-critical assets without impact to your actual infrastructure.
- Verified Graph, Not Predictions: On top of the digital twin, Attack Graph Analysis™ continuously simulates attacker behavior to provide a unified view of risk relationships. It models exactly how attackers leverage exposures to perform privilege escalation, moving laterally through your environment to achieve their objectives.
- Contextualized Prioritization: While some solutions rely on attack prediction algorithms to estimate risk, XM Cyber delivers verified attack paths tested against your specific environment. The platform transforms isolated exposure data into visual graphs that show complex risk relationships, ensuring your team prioritizes remediation based on proven business impact rather than theoretical severity.
This attacker-centric two-step validation process delivers actionable, proof-backed insights, enabling security teams to focus remediation efforts solely on validated exploitable exposures that compromise the business.
What Customers Are Saying
“XM Cyber gives us a clear connection between external exposures and the systems running our production environment. Instead of chasing long lists of alerts, we can immediately see which issues pose real risk to the business and fix what actually matters.”
-Thomas S, Head of IT Infrastructure, Privatmolkerei Bechtel
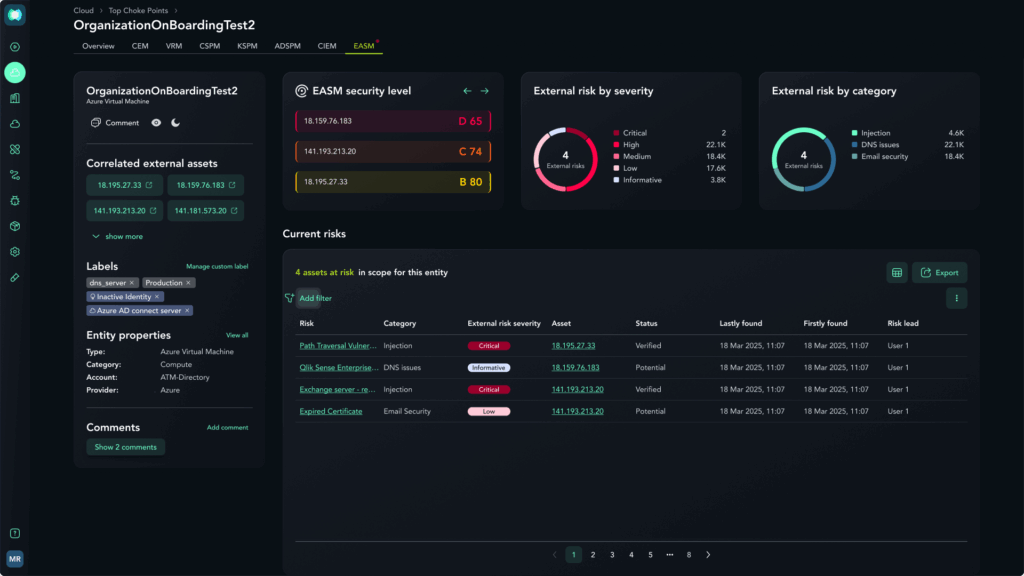
The Workflow: From Discovery to Validation
We have streamlined the process into an easy, three-step workflow:
- Enrich: The platform scans the external surface and automatically applies context-rich labels to matching internal assets.
- Review: Use these labels to identify which internal assets are confirmed as exposed.
- Validate: Set the asset as a breach point and run an attack scenario to confirm if the exposure results in a critical business impact.
Attackers Don’t Work in Silos. Neither Should You.
External Attack Surface Management (EASM) has been an important step forward for security. For the first time, it gave us eyes on the outside: a way to discover the unknown internet-facing assets, shadow IT, and forgotten subdomains that attackers see first. It’s a crucial component of the exposure management puzzle.
But on its own, it’s just that: one piece.
And this is exactly the challenge with standalone EASM solutions: they’re siloed from your internal reality. Many platforms claim to solve this by simply stitching an external scan to a cloud inventory. While this creates a comprehensive map, it remains a siloed view built on static probability.
These tools generate massive lists of potential risks, such as shadow IT, forgotten cloud instances, and third-party connections, but they lack the context to answer the most critical question: “So what?” Does that exposed port on a server you just discovered actually matter? Or does it lead to a dead end? Does that vulnerable application on an old marketing domain have any path to your production database?
A static map can tell you that an asset is exposed, but it cannot tell you if that exposure actually matters to your business. It forces teams to guess which external findings pose a true threat based on theoretical severity scores rather than environmental reality.
Furthermore, attackers don’t respect the artificial boundaries between cloud and on-prem. A breach might start on a legacy VPN concentrator, pivot to an on-prem workstation, scrape credentials, and ride a legitimate identity into the cloud. Solutions that rely on cloud-native scanning or disjointed connectors for on-prem visibility create dangerous blind spots.
XM Cyber takes a different approach. The platform doesn’t just visualize the network. It validates the risk across your entire hybrid attack surface. By autonomously detecting unknown assets and connecting them to internal assets, it ensures no blind spots remain, treating signals from legacy infrastructure with the same fidelity as cloud-native findings. XM Cyber enables organizations to move beyond the list-based approach of other solutions and gain a unified, risk-aware inventory where Security and IT teams share a single source of truth.
See It in Action
Reading about it is one thing. Seeing your own attack surface connected end-to-end is another. See this workflow in action. Book a demo now.