Fix less. Prevent more.
Continuous Exposure Management
XM Cyber automatically discovers how attackers can exploit your environment. It creates a graph of all attack paths to critical assets, so you can stop wasting time on fixes that don’t reduce risk, and instead focus on the 2% of fixes that shut down nearly all attack paths to critical assets.
75% of Exposures Aren’t on Attack Paths to Critical Assets
Despite teams’ best efforts, attacks continue to go undetected. Attackers bypass security controls and exploit a combination of vulnerabilities, misconfigurations, and identities to move laterally towards critical assets. Without understanding how exposures create attack paths, remediation teams waste time fixing the wrong things.
Overwhelming and growing lists of vulnerabilities, misconfigs and identity issues
IT teams get remediation tasks, that lack clarity into the risk to critical assets
Lack of attacker perspective leads to inaccurate, ineffective prioritization, and frustration
XM Attack Graph Analysis™
Stop Attackers by Uncovering and Blocking Their Paths
Change the way You Work
The Most Comprehensive Continuous Exposure Management Solution
Discovery of CVEs and non-CVEs
Use XM Cyber's Proprietary Attack Graph Analysis™ to see how CVEs, misconfigurations, and over-privileges chain together into attack paths to target critical assets. Then make informed decisions based on exploitability and risk impact.
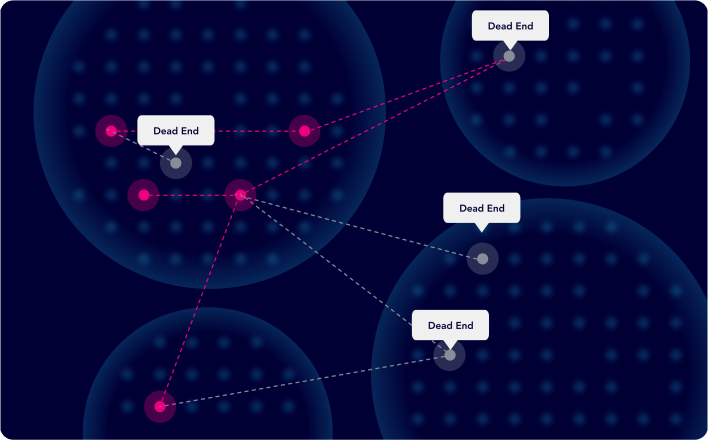
Dead End Identification
XM Cyber maps out all the potential attack paths to your critical assets so you can deprioritize exposures that are worthless to an attacker — the dead ends that can be safely ignored.
Choke Point Identification
XM Cyber Attack Graph Analysis™ uniquely identifies choke points where many attack paths converge. Remediate these spots to stop attackers from advancing to your critical assets.
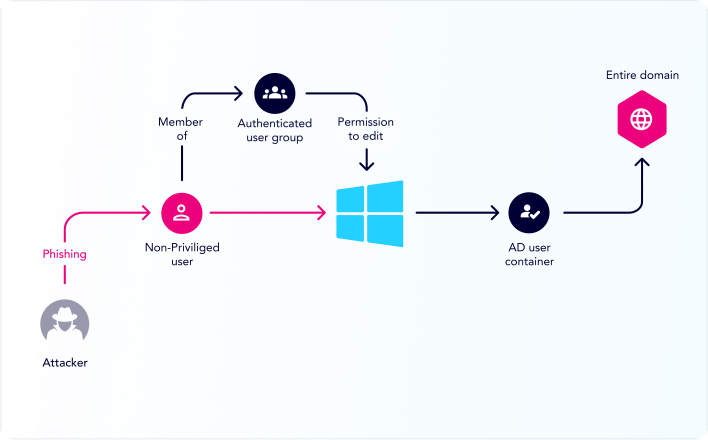
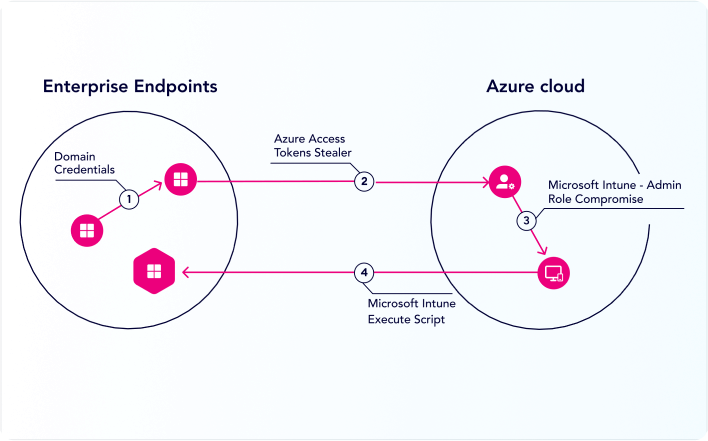
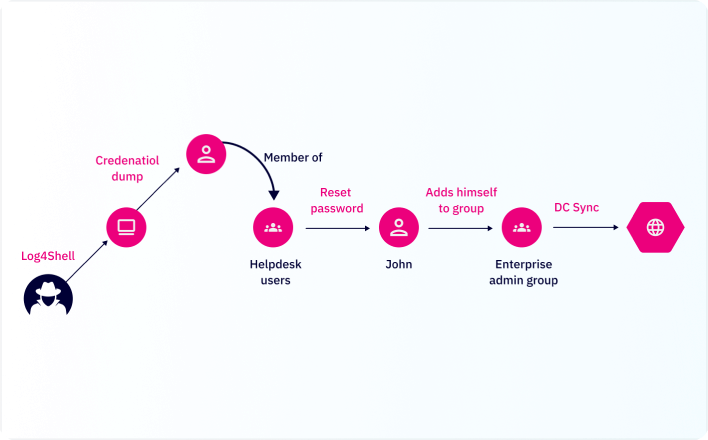
Active Directory & Identity Security
Attackers leverage identities in attacks, and the complexity and pervasive nature of Active Directory makes it a prime target. XM Cyber zeros-in on identity issues and cached credentials.
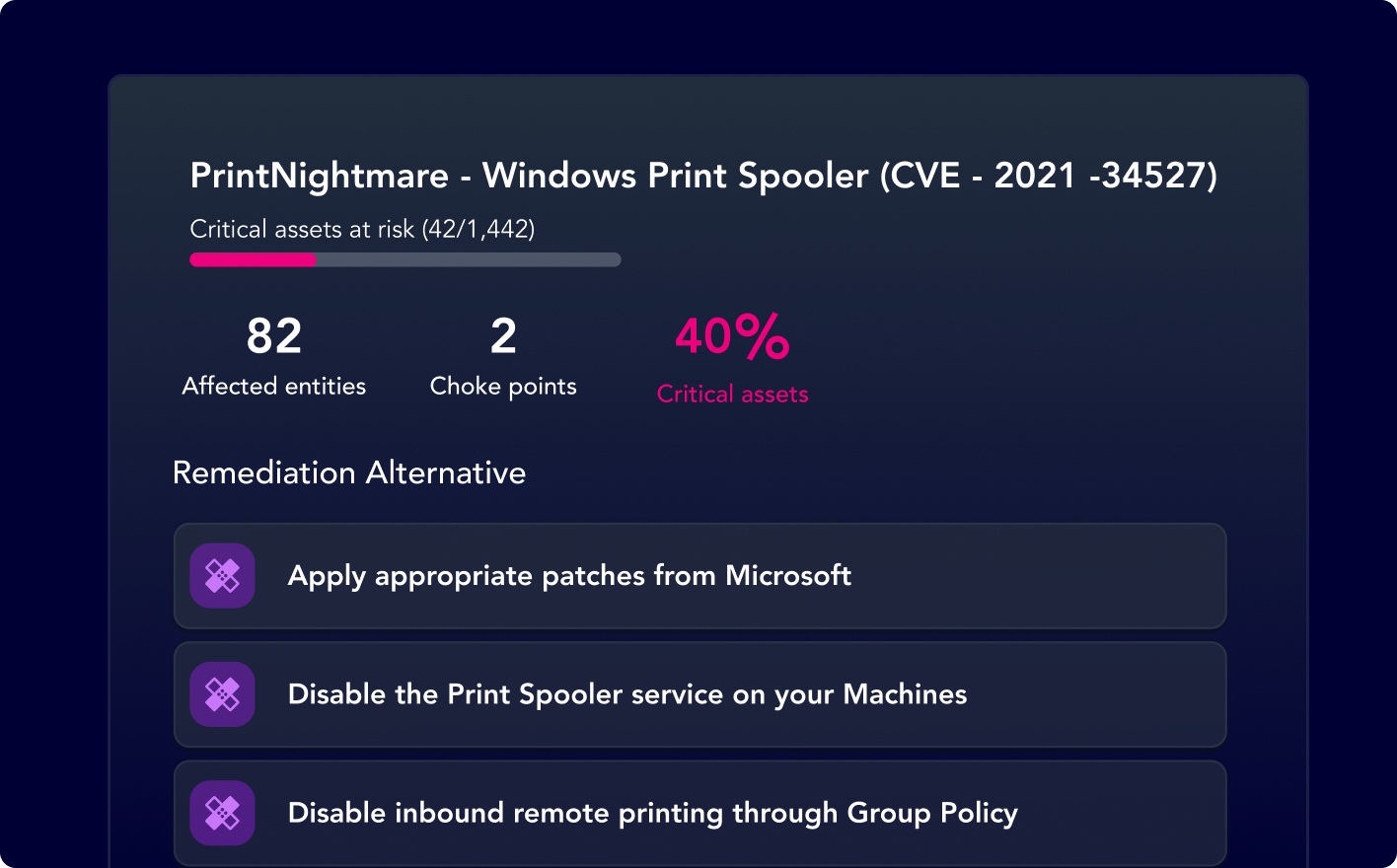
Context-based Remediation Guidance
With XM Cyber, you get context-based guidance on all the different remediation options available, to accelerate the remediation process and improve process consistency.
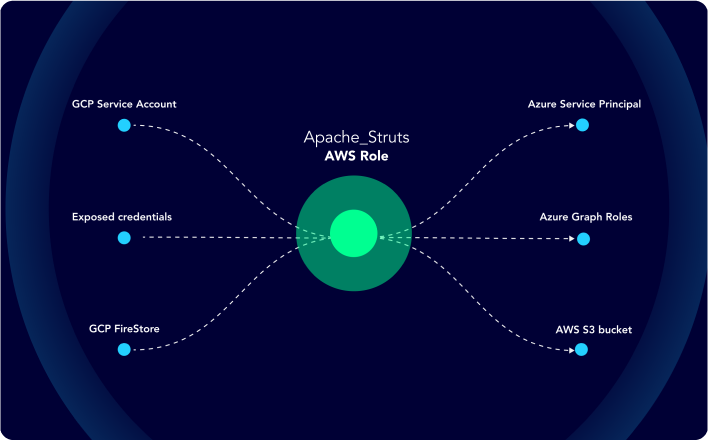
Hybrid Cloud Posture Management
With a holistic, attacker-oriented perspective, XM Cyber grants insights you need, regardless of the environment - cloud, on-prem or hybrid.
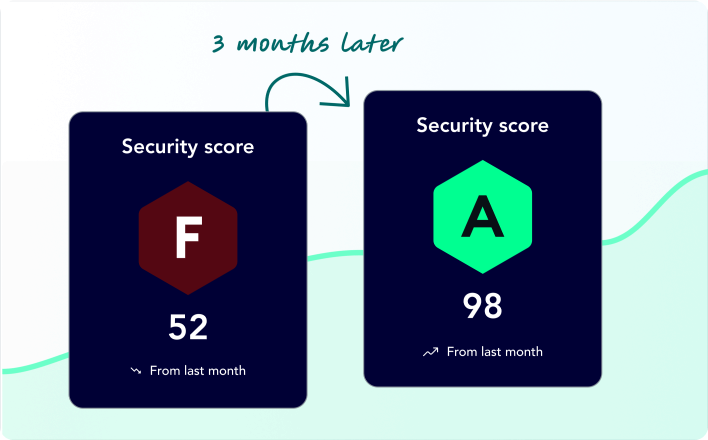
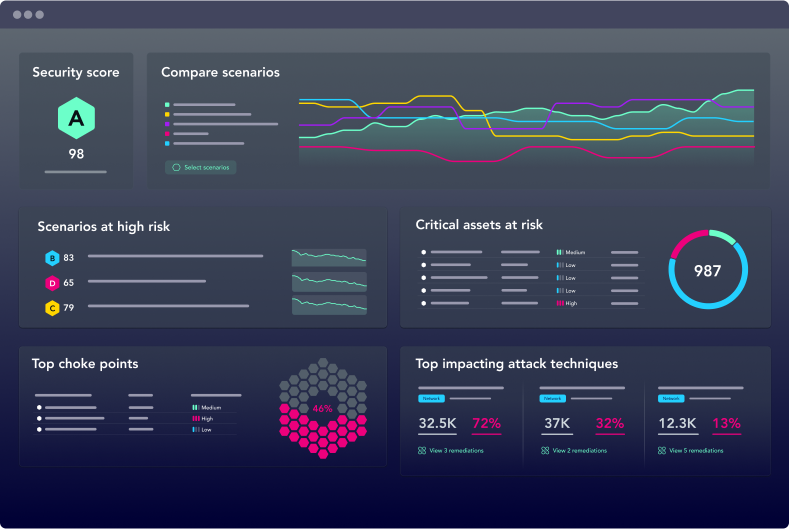
Security Posture Scoring & Trends
Demonstrating improvement in your security posture over time is essential. XM Cyber helps you share continuously updated metrics of security posture and trending that shows the impact of remediation efforts.
The most comprehensive exposure management platform
More Coverage, Smarter Prioritization, Fewer Fixes
Fix less, prevent more
Answer “Where are we most vulnerable?”
Scalable critical asset protection
Hybrid cloud attack surface reduction
Security posture score and trends
Continuous Exposure Management
Fast Track Your CEM Program Maturity
XM Cyber is the most comprehensive way to meet and maintain a continuous Exposure Management program – and now teams can easily operationalize it with our EMS Managed Service. Extend your existing security team with the power and expertise of a designated remediation expert.