|
Getting your Trinity Audio player ready...
|
Most security leaders I’ve worked with completely get the theory of exposure management. The challenge lies in turning that theory into practice. Many EM programs lose momentum after the first assessment or report because teams struggle to connect findings to business priorities. And without structure, exposure management becomes another list – visible but not actionable.
Attackers, meanwhile, are not resting. In fact, they’re staying a step ahead by linking small gaps into complete attack paths. A weak configuration, a shared credential, an unused account – any of these can become the first step into one of your critical systems.
Exposure management works when it’s a repeatable process – not a tool or report. In this blog, I’ll explain how to build an exposure management plan that replaces chaos with clarity and turns visibility into control – one step at a time.
The Foundation: Defining Exposure and Setting the Stage
Exposure management is a continuous cycle that identifies, prioritizes, and mitigates the gaps that create organizational risk. Each exposure is an entry point an attacker could use to reach valuable assets. The objective is to reveal those paths and close them in a way that reflects their actual business impact.
This approach introduces a different way of thinking. Vulnerability programs traditionally rely on numerical scores such as CVSS. Exposure management focuses on exploitability and consequence. It combines all types of exposures to show how a single weak configuration or identity can be used together to weave through defensive layers and connect to a critical process or system. The result is a clear view of risk that links technical findings to business value and a clear model for prioritizing what to fix first.
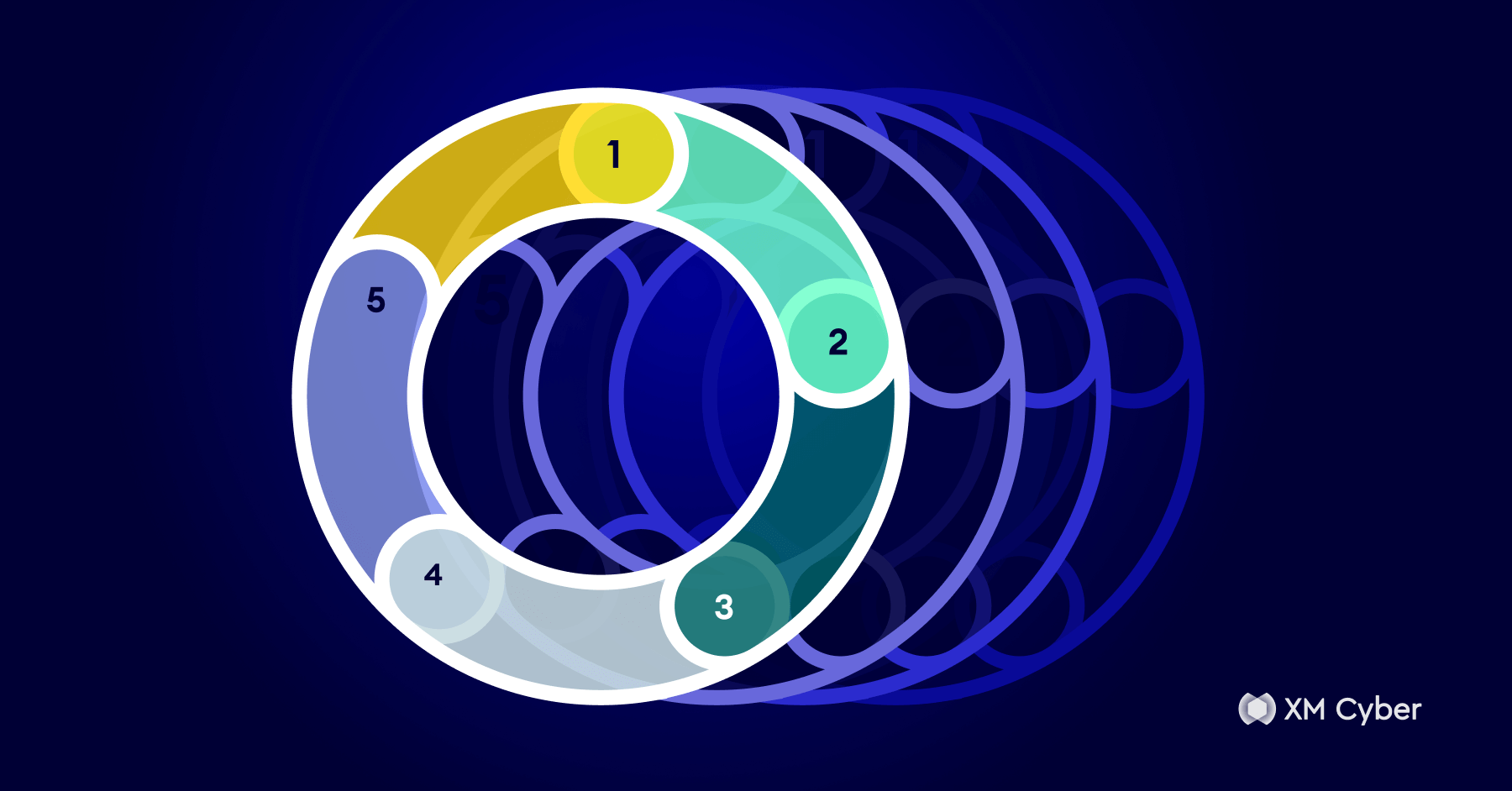
To make exposure management a structured, repeatable process, Gartner created their Continuous Threat Exposure Management (CTEM) framework with the following five phases. Each one reflects how XM Cyber’s platform brings these principles to life – from defining scope and mapping attack paths to validating controls and guiding remediation.
The 5-Step Exposure Management Lifecycle
Step 1: Scoping – Aligning Security to Business Priorities
Scoping sets the focus. It defines the systems, data, and processes that keep the organization running and determines which of them would cause real damage if breached. Once that list exists, leadership decides how much risk is tolerable and where exposure management begins and ends. Scoping prevents wasted effort by linking every security decision to what drives the business.
XM Cyber’s Secret Sauce
XM Cyber’s digital twin brings greater precision to the scoping process. It models the organization’s entire environment and identifies which assets serve as the true “crown jewels.” By tracing every possible attack path to those assets, it helps teams define boundaries, clarify dependencies, and set meaningful risk thresholds. This clarity turns scoping from an abstract discussion into a concrete, data-driven starting point for the exposure management plan.
Step 2: Discovery – Mapping the Full Attack Surface
Discovery turns unknowns into facts. It identifies every endpoint, cloud workload, and forgotten account that could become an entry point. This step builds a single, accurate inventory that goes beyond vulnerability scans and includes privilege excess, open services, and misconfigurations. Discovery gives security teams the first complete picture of their environment. With that foundation, they can see how each weakness links to another and where attackers might start moving through the network.
XM Cyber’s Secret Sauce
XM Cyber automates discovery across every environment, connecting asset data with identity, privilege, and configuration insights. Its correlation engine filters noise and highlights the exposures that actually matter. Continuous data feeds keep the inventory fresh, so teams always see the latest changes and know which assets, users, or connections create real risk.
Step 3: Prioritization – Focusing on What Matters Most
Prioritization turns data into direction. Every vulnerability, configuration gap, or privilege issue must be ranked by its business impact. Teams look at how easy it is to exploit, which assets it touches, and how close it sits to critical systems. This approach moves security away from patch counts and toward outcomes. Prioritization makes risk visible to both technical and business leaders, helping them agree on which problems to solve first and why.
XM Cyber’s Secret Sauce
XM Cyber strengthens prioritization by linking exposures directly to business impact. The platform identifies choke points – issues that, when fixed, block multiple attack paths – and sets aside exposures that lead nowhere. XM Cyber weighs exploitability, asset value, and attack reach to rank risks by real consequence rather than score. This precision helps teams focus resources where they achieve the greatest and fastest exposure reduction.
Step 4: Validation – Testing Effectiveness
Validation proves what works. Once exposures are identified and ranked, teams test whether defenses hold up. They simulate attacks or review controls to confirm that existing tools block real-world threats. Validation exposes blind spots that automated alerts might miss and confirms where risk has genuinely decreased. This process creates confidence that each fix achieves its purpose and that resources are being used where they make a measurable difference.
XM Cyber’s Secret Sauce
XM Cyber turns validation into a continuous feedback loop. The platform automatically tests live attack paths to confirm whether existing controls stop real threats. It exposes gaps that traditional testing overlooks and shows exactly where security measures succeed or fail. Each validation cycle feeds real data back into prioritization, keeping defenses current and aligned with how attackers actually operate.
Step 5: Mobilization and Remediation – Fixing the Right Things
Mobilization turns insight into action. Each exposure gets an owner, a timeline, and a resolution plan that matches its risk level. Some fixes involve patching, while others may include configuration changes or access adjustments. The goal is continuous progress rather than one-time cleanups. Tracking progress through simple, consistent metrics keeps leadership informed and holds the process accountable.
XM Cyber’s Secret Sauce
XM Cyber streamlines mobilization by turning validated insights into clear, guided actions. The platform assigns ownership, sets priorities, and links each task to measurable impact. It highlights where one fix can eliminate multiple attack paths, helping teams act faster and with confidence. Real-time tracking shows how every change reduces exposure, giving both security and IT a shared, data-driven view of progress.
Taking Control of Your Risk
Exposure management succeeds when it becomes part of everyday work. The five steps – scoping, discovery, prioritization, validation, and remediation – create a rhythm that links technical action to business value.
XM Cyber brings that rhythm to life. The platform’s continuous modeling, contextual analytics, and guided remediation help teams move from isolated fixes to measurable risk reduction. The outcome is a living process that keeps pace with change and proves its impact.
To make your exposure management process work, start by defining what matters most. Then keep refining. The more consistently your EM process runs, the clearer the picture becomes – and the more resilient your organization becomes.