|
Getting your Trinity Audio player ready...
|
Cybersecurity can seem like a game of cat and mouse.
Defenders try to anticipate attackers’ moves; attackers try to sneak through gaps in security coverage. Organizations most frequently fall victim to breaches not because they lack security measures, but because they couldn’t see the full picture and didn’t anticipate the attacker’s next move. The reason is simple: too many moving parts. Attackers rarely exploit a single vulnerability in isolation. Instead, they chain multiple weaknesses together – skipping lightly over misconfigurations, credential leaks, network gaps and more to reach critical assets.
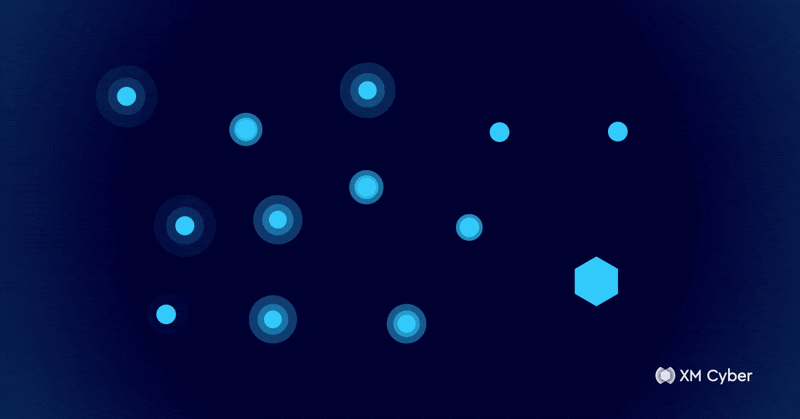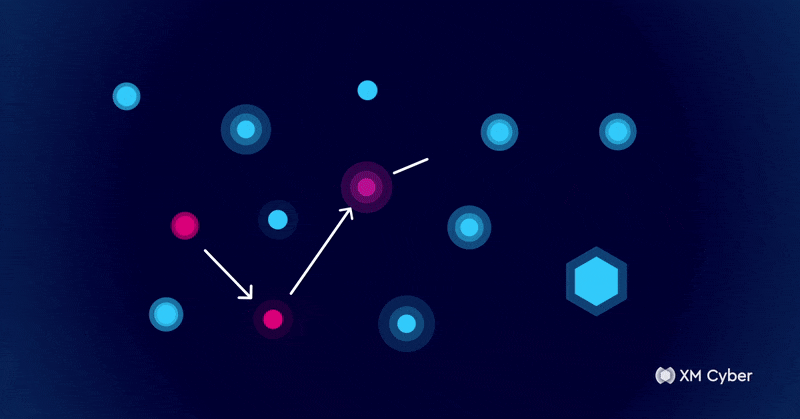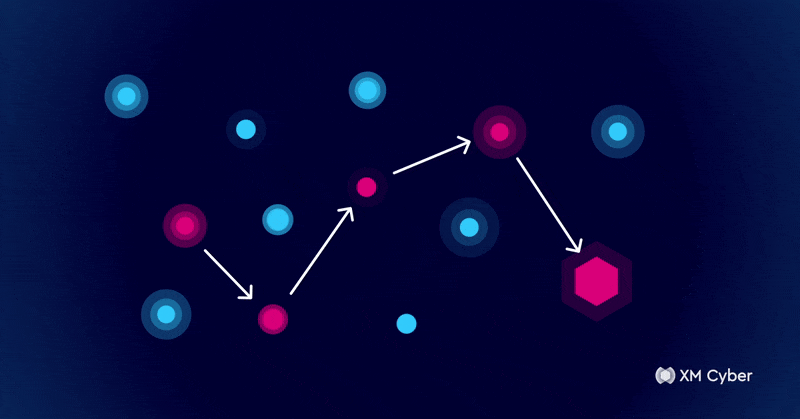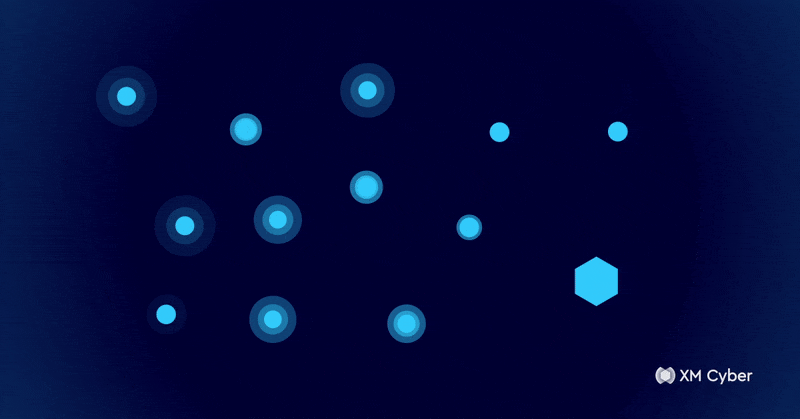
This is where attack graphs come in. Traditional security tools focus on identifying individual vulnerabilities, but attack graphs show how those weaknesses connect – creating actual paths that an attacker could take. This allows organizations to anticipate threats rather than react to them.
In this blog, I’ll take a deep dive into how attack graphs provide a powerful advantage in cybersecurity – enabling defenders to see what an attacker sees and disrupt attack paths before they are exploited.
What are Attack Graphs?
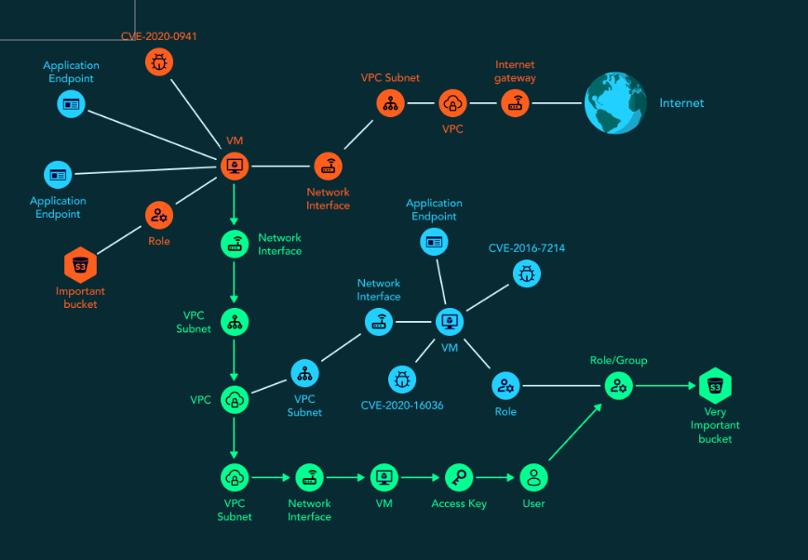
Attack graphs are visual representations of possible attack paths in a system or network. They map how an attacker could navigate through a range of security weaknesses to reach critical assets. Unlike traditional vulnerability management, which prioritizes flaws largely based on severity scores, attack graphs add context by incorporating exploitability and business impact.
For example, a high-severity vulnerability may seem like an urgent issue, but if it isn’t accessible to an attacker, it poses little actual risk. Conversely, a lower-severity flaw might become critical if it can be chained with other weaknesses. Attack graphs provide this essential context, helping security teams focus on the risks that truly matter.
Another key feature of attack graphs is the ability to provide continuous assessment. Traditional approaches, like penetration testing and red teaming, provide valuable insights, but they offer only a snapshot in time – which is quickly outdated. Attack graphs, on the other hand, update dynamically as environments change. They continuously analyze all possible attack paths, allowing security teams to proactively address weak points before attackers exploit them.
The Different Types of Attack Graphs
There are multiple types of attack graphs, each with varying levels of sophistication and effectiveness.
- Security graphs are the most basic form of attack graph. They map relationships between user permissions, network configurations, vulnerabilities and more. While they provide valuable visibility, they don’t necessarily show how an attacker could exploit these connections. Security graphs often require manual queries to analyze risks, meaning security teams must already know what they’re looking for – an approach that can leave blind spots.
- Aggregated graphs take security a step further by combining data from multiple tools like vulnerability scanners, identity management systems, and cloud security solutions. These graphs provide a more complete view of risk across different environments. However, they depend on the quality and completeness of the data being fed into them. If critical gaps exist in the underlying security tools, those gaps will persist in the graph.
- Holistic attack graphs are the most advanced type. They go beyond just mapping relationships or aggregating data – they model real-world attacker behavior. These graphs don’t rely on predefined queries but instead analyze all possible attack paths, dynamically updating as environments shift. By incorporating continuous monitoring, real exploitability context, and risk prioritization, holistic attack graphs give security teams the most actionable intelligence.
What Attack Graphs Do Best
The real power of attack graphs lies in their ability to dramatically improve cybersecurity decision-making via better risk prioritization. Rather than blindly patching vulnerabilities based on severity scores, attack graphs help security teams focus on the weaknesses that attackers are most likely to exploit. This targeted approach ensures that remediation efforts have the greatest impact.
Attack graphs also enhance cross-team communication. Cybersecurity risks can be complex, which makes it difficult for CISOs to explain threats to executives and boards. Attack graphs provide clear visual representations, so it’s easier to communicate risk in a way that non-technical stakeholders can understand.
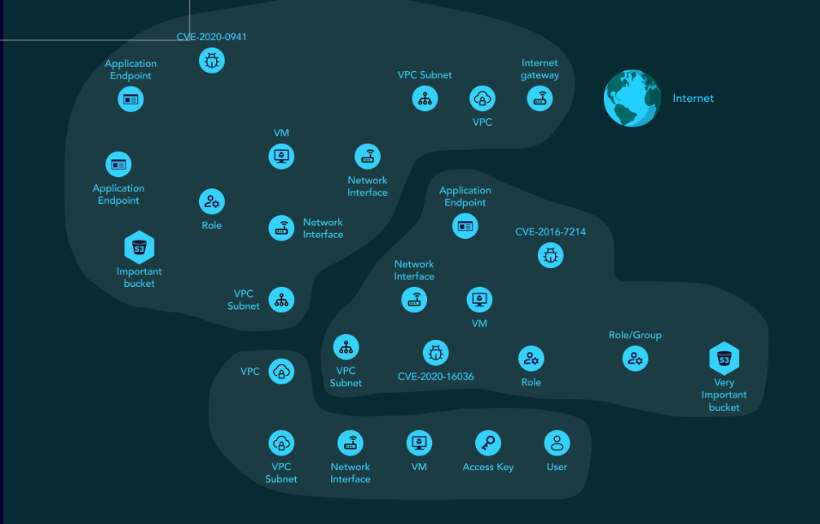
Another key benefit is the efficiency they bring to security operations. Many organizations struggle with resource constraints that make it literally impossible to fix every security issue. By identifying critical “choke points” – key weaknesses that, if fixed, significantly reduce risk across multiple attack paths – attack graphs help security teams allocate limited resources more effectively.
Moving from Reactive to Proactive Security
One of the biggest challenges in cybersecurity is staying ahead of threats rather than reacting to them after an incident occurs. Attack graphs help organizations shift from a reactive to a proactive security strategy by enabling continuous assessment and integrating threat intelligence.
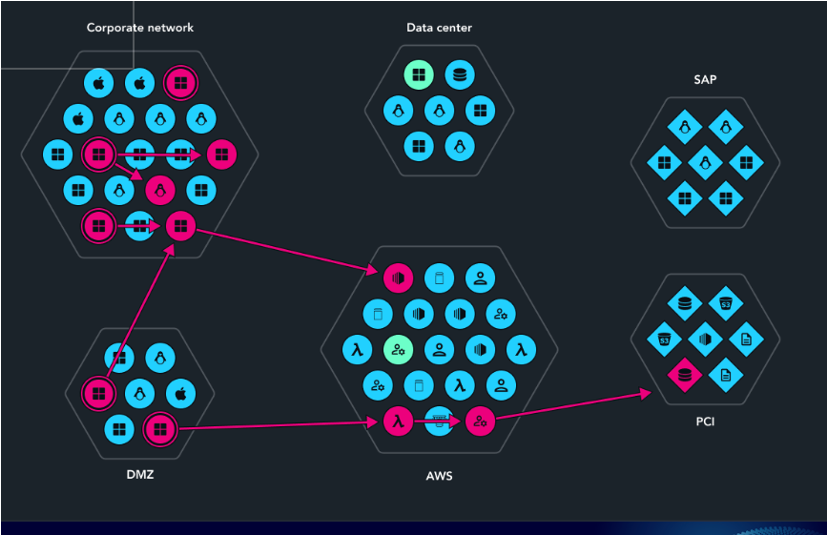
Taking into account real-time data on emerging vulnerabilities, exploit techniques, attacker behavior and more – attack graphs allow organizations to anticipate threats before they materialize. This is especially important in modern IT environments, where cloud resources, user identities, and attack surfaces are in constant flux. Static security assessments quickly become outdated, but attack graphs provide ongoing visibility.
Additionally, attack graphs make security operations more strategic. Instead of reacting to security alerts in isolation, security teams can see how different risks connect and understand the bigger picture. This broader perspective enables smarter decision-making and reduces the likelihood that critical security gaps will be overlooked.
Why Attack Graphs Are the Future of Cybersecurity
As cyber threats become more sophisticated, security teams need tools that provide deeper visibility and smarter risk prioritization. Attack graphs are a major leap forward in how organizations approach security. They allow defenders to see what attackers see, identify the most critical vulnerabilities, and focus on fixing the issues that matter most.
Instead of relying on periodic security assessments that quickly become outdated, organizations can use attack graphs to maintain continuous visibility into attack paths. This shift from reactive patching to strategic risk reduction not only strengthens defenses but also makes security teams more efficient.
Cybersecurity is not (and has never been) just about fixing vulnerabilities – it’s about understanding how attackers move through an environment and cutting off their access before they can reach critical assets. Attack graphs make this possible, helping organizations stay ahead of threats and outsmart attackers.