|
Getting your Trinity Audio player ready...
|
The cybersecurity industry has been driven by volume for years. More alerts, more scanners, and more “critical” vulnerabilities to patch. In 2025, this approach proved its operational inefficiency. Legacy vendors continued to sell this idea of “more”, while security teams continued to drown in alerts and never-ending noise. The “speculation” model, where organizations assume every high-score CVE should be prioritized, has failed for lack of business context. Organizations were always told to “patch everything”, but now, we’ve seen that’s mathematically impossible.
Proving What Actually Matters
In 2025, while other vendors offered more ways to find problems, XM Cyber focused on the elimination of noise. Our data from thousands of environments showed that 74% of identified exposures are “dead ends”, i.e., they exist on entities that don’t have paths leading to critical assets. Fixing these is nothing more than “security theater”. Sure, it looks like work, but it doesn’t actually reduce risk.
Building the “Validation Engine”
To move the industry from speculation to certainty, we spent 2025 introducing features that provide Exposure Intelligence, i.e., the ability to know which exposures, in reality, create the most risk. This helps organizations zero-in on their “Choke Points”, or, the small fraction of exposures that actually matter. By focusing on these validated paths, we helped organizations get their time and resources back. This security team from a “scanner of lists” into an “efficiency engine”.
2025’s Most Impactful Milestones
So here’s a look at the most important features that debuted last year. All were designed with one goal in mind; to help teams focus on what matters most and prevent high-impact attacks.
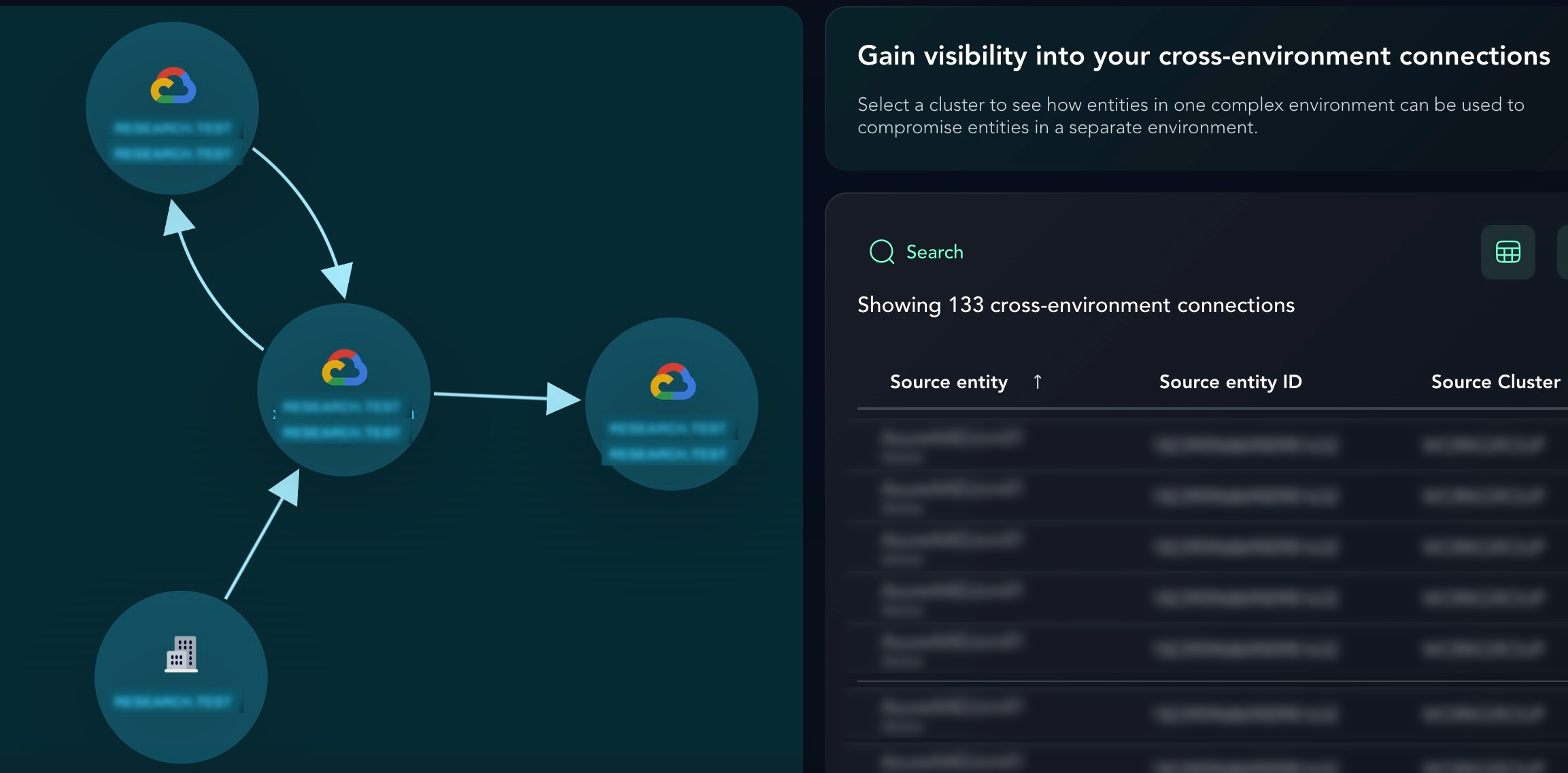
The Cross Graph
Security teams often assume an environment is isolated, but attacker movement proves otherwise. The Cross Graph removes this speculation by mapping cross-environment connections between multi-cloud and Active Directory environments. As part of the XM Cyber CEM Reports module, Cross Graph scans and identifies your organization’s most at-risk complex environments. Based on these findings, the report maps out cross-environment connections between Source entities and Target entities in separate environments. This perspective enables you to remediate against each Exposure, putting those entities at risk, thereby continuously improving your security posture.
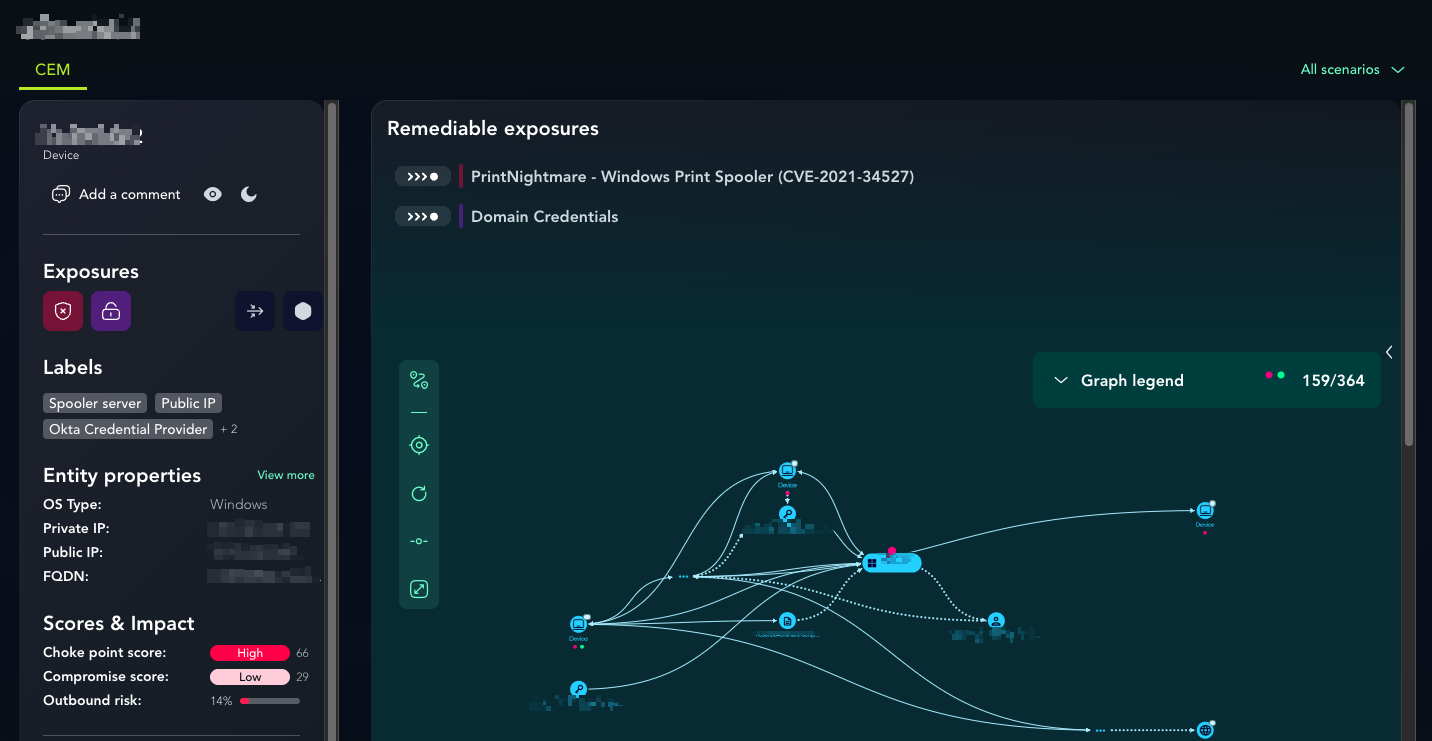
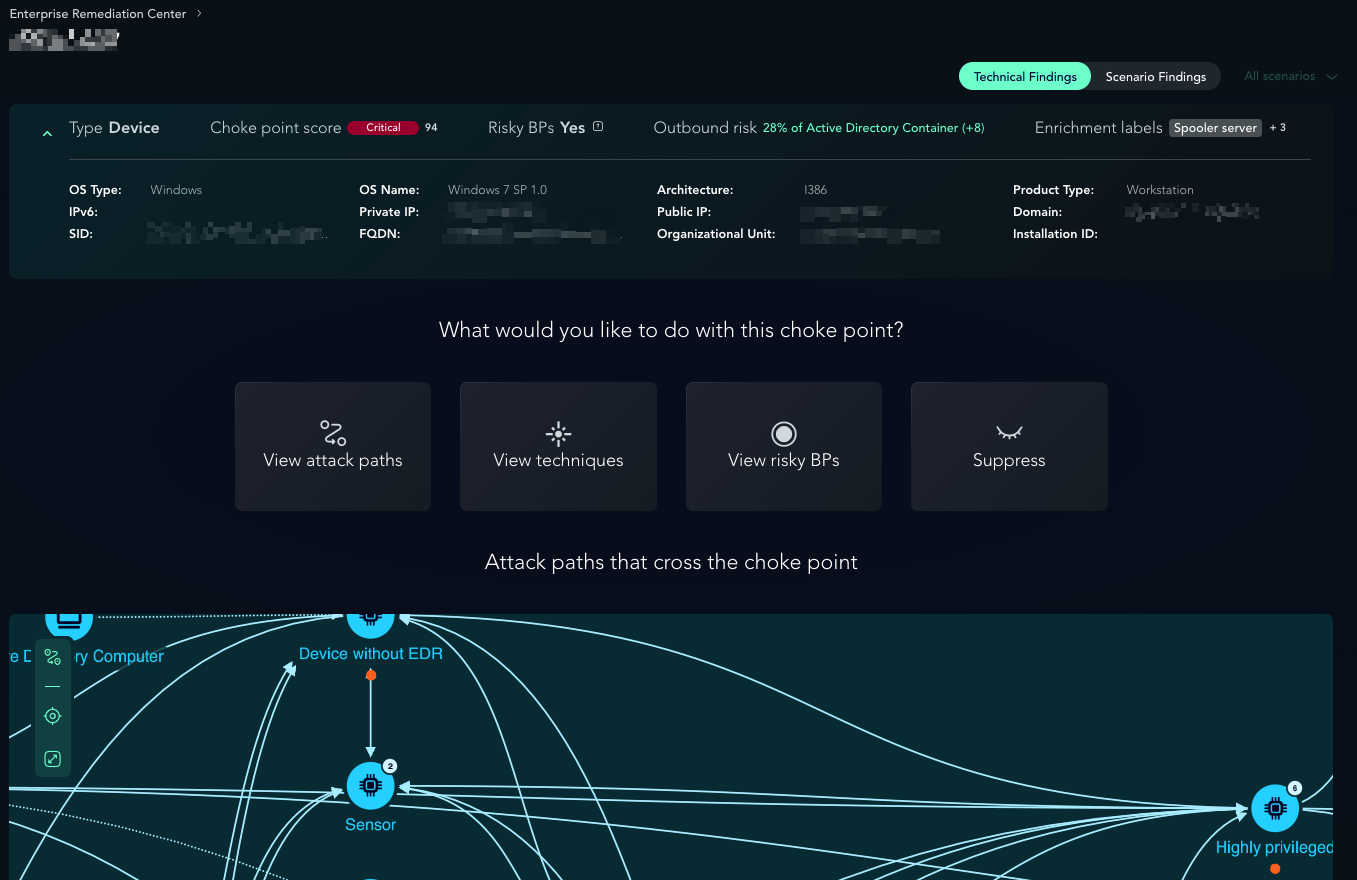
Entity Cards
Traditional investigation requires manual correlation across multiple dashboards, which is where important context is lost. Entity Cards consolidate all investigation data for a single entity, showing you how it behaves in your environment, how it can be compromised, and how it puts your critical assets at risk. By providing both scenario cards, which highlight an entity’s role as a breach point, choke point, or critical asset in a scenario, and technical cards for environment-wide analysis, the platform removes the need to alternate between reports. This centralized intelligence allows security teams to understand complex interactions and prioritize the remediations that actually remove risk, rather than wasting time on data mining.
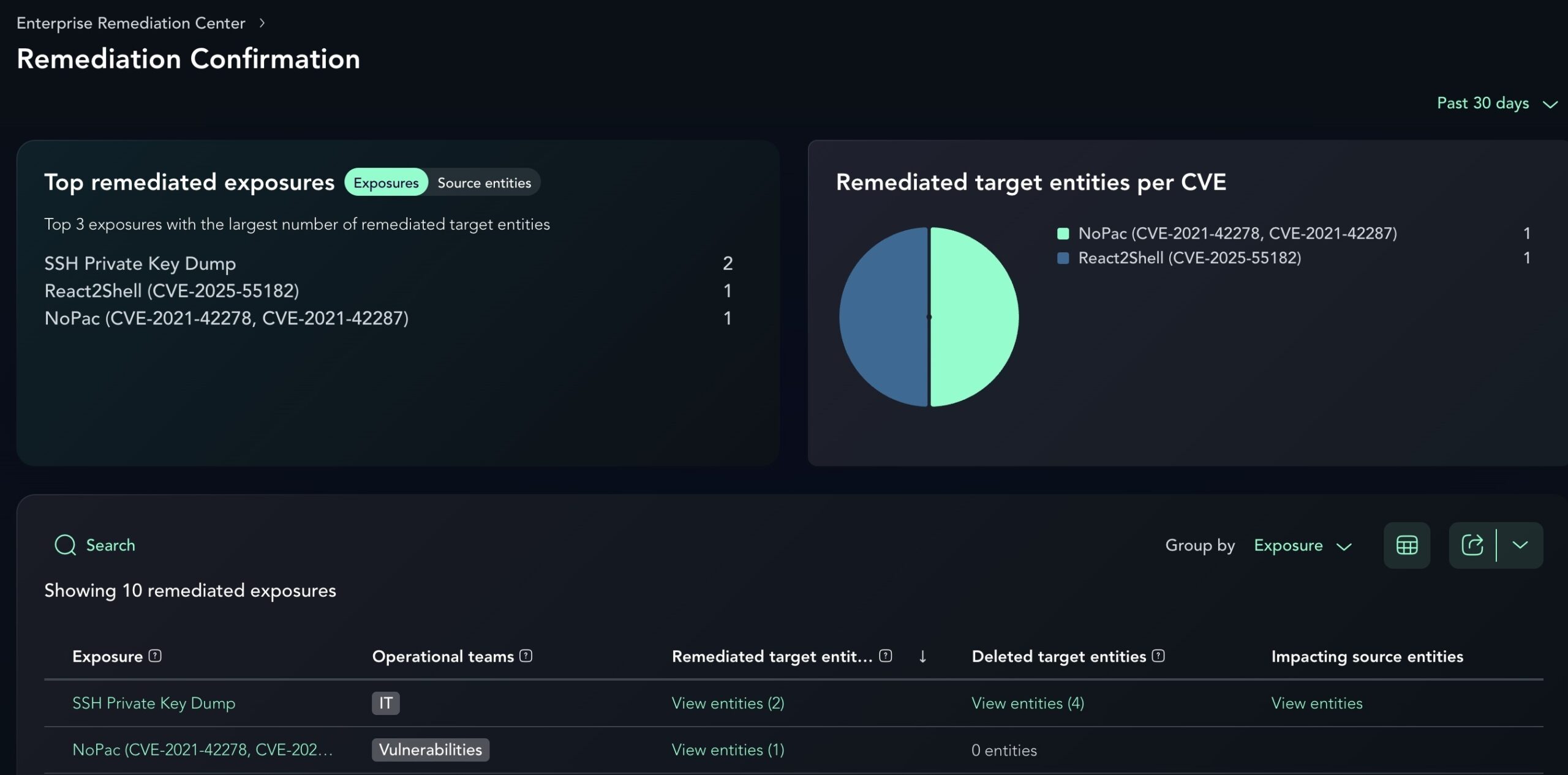
Remediation Confirmation
A “closed” ticket does not equate to a removed risk, and manual verification is a constant resource drain. To solve this, our Remediation Confirmation feature tracks progress across enterprise and cloud environments to provide defensible proof that an attacker’s path has been successfully blocked. The system monitors remediated and deleted entities and automatically confirms they are no longer able to be compromised once they have not appeared in reports for two full days.
While certain user-behavior exposures, such as SSH Session Hijackers or External Drive Injectors, require manual oversight due to their unpredictable nature, the platform provides clear tracking for the vast majority of exposures. By allowing users to group remediation data by Exposure, Target, or Source entity, the report replaces speculation with a validated audit trail of actual risk reduction.
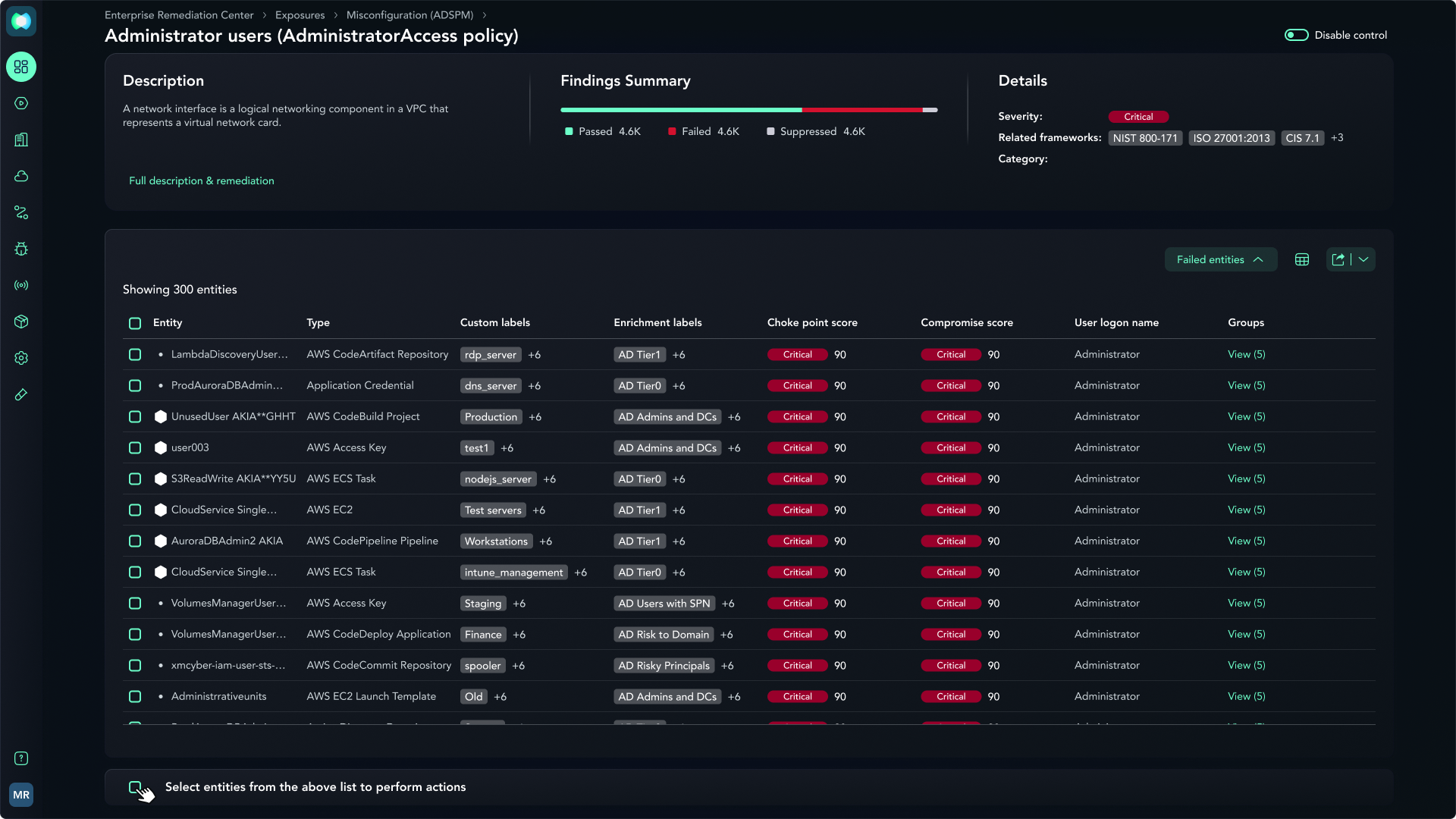
Active Directory Excessive Permissions
Identity misconfigurations are often more dangerous than software bugs, yet they are rarely prioritized. To address this, our Active Directory Excessive Permissions feature monitors Active Directory to identify permissions that have remained unused for significant periods, such as 90 days or more, flagging them for safe removal.
Integrated directly into exposure reports, the feature provides annotated remediation instructions that allow security teams to implement a ‘least privilege’ policy with total confidence that business continuity will not be disrupted. By aggregating all excessive permissions for a given entity into a dedicated report, the report helps users prioritize low-risk, high-impact fixes. This moves the focus away from speculative patching and toward validated removal of the “hidden” paths attackers use to pivot through an Active Directory environment.
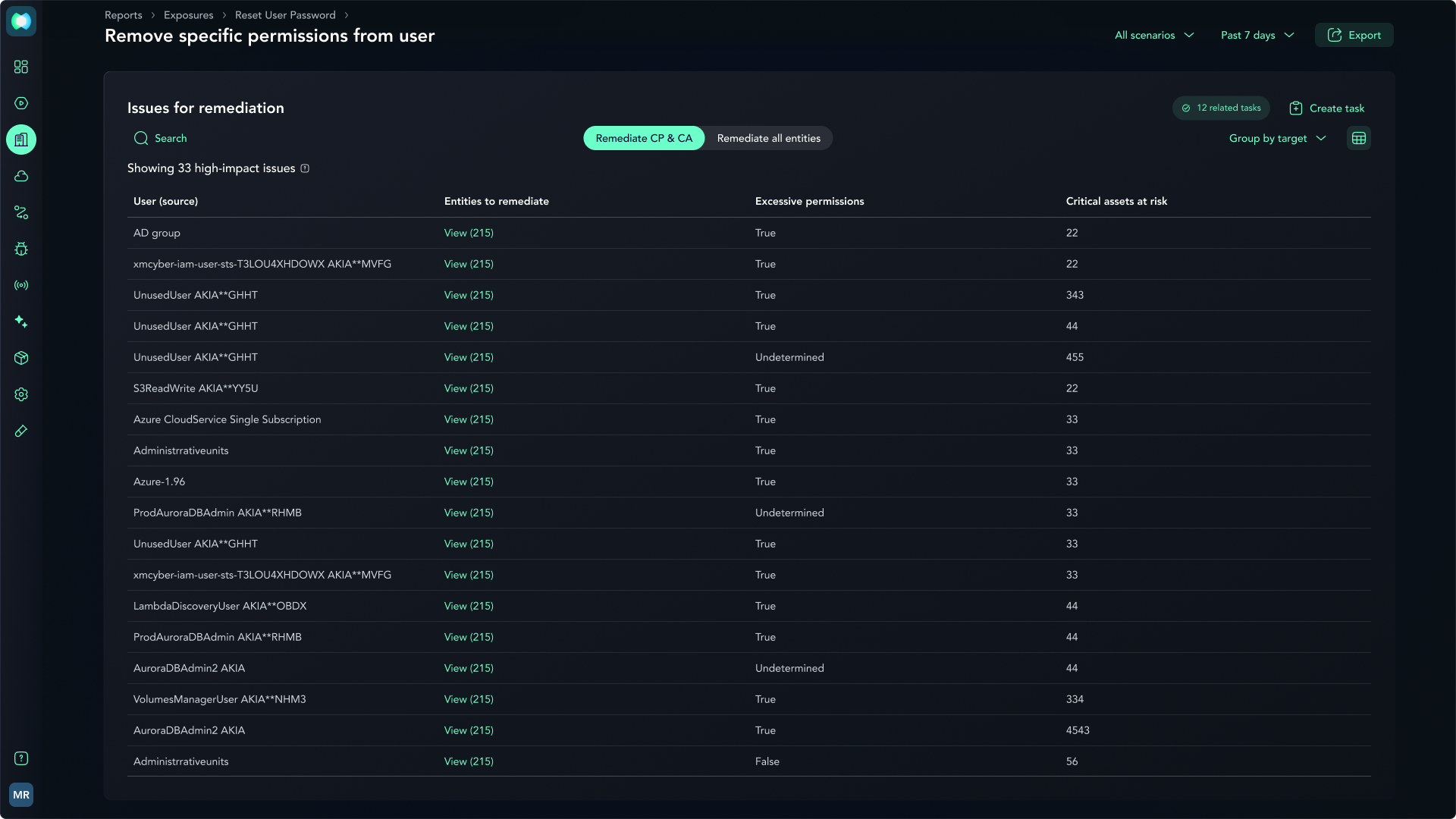
XM EASM
Knowing that you have an external vulnerability is useless if you don’t know where it leads to. XM EASM enables you to identify potential vulnerabilities and security gaps in your organization’s public-facing digital attack surface through automated discovery, removing blind spots and avoiding consequential oversights. XM EASM then communicates with XM CEM to identify and validate entities on your internal network that are paired with, or connected to, the risky devices detected on your external network.
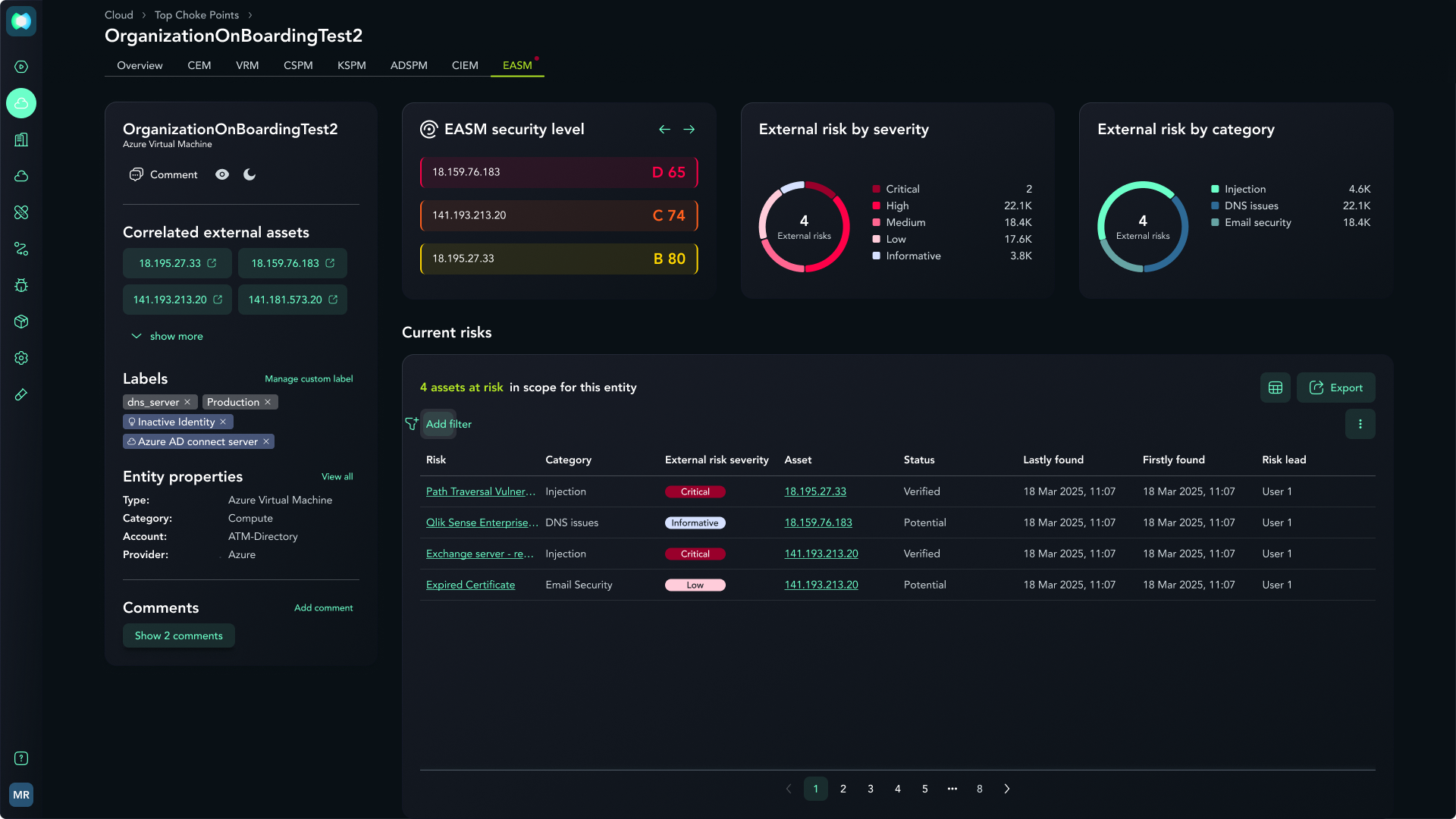
Executive Summary Report
The Summary Report gives you a single, clear story about your cyber risk and progress. In one place, you can see the environment you’re protecting, how your overall security score and scenarios are doing over time, and which areas are most at risk. You choose which areas to include so the report matches the questions your leadership is actually asking: where you’re exposed, what has improved, and where to focus next. This makes it easier to communicate with executives, align teams around a shared view of risk, and show the impact of your security efforts over time.
Security Posture Management
Credential hygiene metrics are often subjective, making it difficult to demonstrate tangible security improvements to the board. Our Security Posture Management framework addresses this by replacing speculation with a data-driven score out of 100, calculated every four hours based on real-time harvests of misconfigurations and security best practices.
By measuring different hygiene and security metrics across your accounts, the system categorizes controls by status and severity, allowing you to prioritize remediations that minimize operational disruptions and breach risks. This approach moves beyond simple compliance checkboxes, providing a continuous, objective rating of your cyber defense that excludes disabled controls to ensure your “defense score” reflects the actual hardened state of your infrastructure.
Integration with ServiceNow
While ServiceNow Vulnerability Response (VR) is a powerful tool, its effectiveness is often impacted by a CMDB that lacks business context, leaving teams to prioritize remediation based on incomplete data. XM Cyber bridges this gap by injecting Attack Graph Analysis™ into your workflow, showing exactly how attackers interconnect vulnerabilities and misconfigurations to reach your critical assets. By enriching ServiceNow VR with this ‘Exposure Intelligence,’ you can stop chasing dead ends and focus remediation on the 2% of exposures that actually pose a threat to your business continuity.
Integration with Google SecOps
While Google Security Operations (SecOps) delivers a unified experience for detection and response, teams often find themselves buried under alerts that lack business context. By integrating XM Cyber’s Continuous Exposure Management (CEM), teams can use Google’s advanced detection to identify real-world breach points and XM’s Attack Graph Analysis™ to filter out the noise. This partnership transforms your SOC from a ‘detection engine’ into an ‘efficiency engine’ by enriching SIEM and SOAR workflows with entity data that highlights the 2% of exposures that actually threaten your critical assets.
Integration with SentinelOne
While SentinelOne provides world-class AI-driven detection, the missing link for many security teams is understanding the blast radius of an alert. By integrating XM Cyber with SentinelOne, you can bridge the gap between active threats and potential attack paths. XM Cyber enriches SentinelOne by labeling Choke Points directly within your EDR console, so when an alert hits a critical asset, your team knows the stakes instantly.
Conversely, SentinelOne feeds live threat data back into XM Cyber, allowing you to run exposure scenarios on the devices actually being targeted. This creates a continuous loop where real-world attacks inform your proactive defenses, ensuring you prioritize the remediations that break the most dangerous attack paths.
Conclusion
While a lot of vendors spent 2025 promising the moon, we spent the year rolling out capabilities that truly move the needle and help organizations fix what matters most. But that was just the beginning. 2026 will be the year of helping you drop the volume mindset to ensure less noise, greater resilience, and total clarity on your security posture.







