|
Getting your Trinity Audio player ready...
|
Connect the Dots. Eliminate Risk From External Exposures.
Bridge the gap between your external attack surface and your internal environment. Move beyond simple discovery to validate which external exposures pose a true threat to your business-critical assets.
Digital sprawl is accelerating. As organizations adopt cloud services and SaaS applications, the attack surface expands beyond the traditional perimeter. “Unknown unknowns” create dangerous blind spots, leaving businesses exposed to attacks that traditional tools often miss.
However, the solution doesn’t lie in discovery alone. Traditional tools, even if focused on the external attack surface, operate in a silo. They generate massive lists of potential risks but lack the context to answer the most critical question: So what?
XM Cyber continuously scans the open web to uncover known, unknown, and rogue assets, utilizing AI-driven pattern matching to identify exposures. It then validates these findings through automated, agentless pen-testing, filtering out non-exploitable noise. Then, the platform connects these external findings directly to your internal environment, enriching your asset inventory with exposure context and mapping the full attack path from the perimeter to your critical assets.
Eliminate Blind Spots:
Gain continuous, real-time awareness into every asset and exposure across your external attack surface, eliminating blind spots.
Validate Don’t Just Prioritize:
Leverage agentic AI to prove which exposures are truly exploitable, filtering out noise with the precision of an experienced pentester.
Fix What Matters:
Map external exposures to the XM Attack Graph™ to pinpoints the critical choke points where one fix severs multiple attack paths.
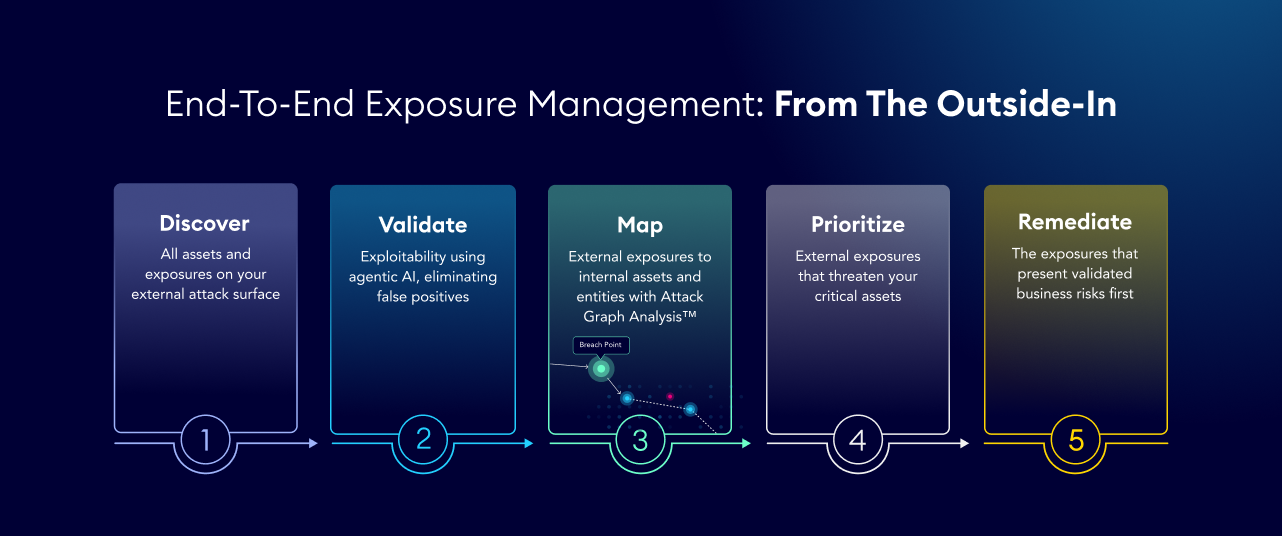
Discover
Continuously uncover your entire external attack surface, including shadow IT, forgotten cloud instances, and third-party connections, using the same reconnaissance techniques attackers do. Autonomously detect unknown assets, ensuring no blind spots remain.
Validate
Move beyond theoretical risk with agentic validation. EASM mimics attacker behavior to actively verify if an exposure is truly exploitable, instantly filtering out the noise of false positives. This ensures your team stops chasing list-based alerts and focuses only on confirmed entry points.
Map
Eliminate silos with automated external-to-internal asset enrichment. When a risky asset is found externally, the platform automatically cross-references it with your internal network, labeling the corresponding internal device with its exposure context. This creates a single, risk-aware inventory where Security and IT teams share one source of truth.
Prioritize
Understand the true business impact of every external finding. XM Cyber maps external assets to internal systems using Attack Graph Analysis™ to reveal whether an exposure leads to a dead end or a critical system. This enables teams to focus on fixing exposures that pose validated business risk first.
Remediate
Drive action with maximum impact. Instead of patching every vulnerability, identify the critical choke points where one fix severs multiple attack paths. Provide IT teams with the precise context and guidance needed to shut down validated risks before an attacker can exploit them.
About XM Cyber
As the pioneer of exposure management, XM Cyber delivers a continuous and actionable understanding of cyber risk across the entire attack surface, including external, cloud, and on-premise environments. Powered by proprietary Attack Graph Analysis™, the platform continuously validates exploitable exposures against a digital twin of your production environment, applying nearly a decade of offensive security expertise.
This approach provides a comprehensive and contextual view of risk by mapping relationships across systems, configurations, and identities. By revealing the critical choke points where multiple attack scenarios converge, XM Cyber directs security teams to the remediation actions that eliminate the most risk with the least effort. The result is measurable improvement in security posture through prioritized, high-impact remediation, along with clear, business-contextual reporting that enables leaders to communicate risk effectively and demonstrate security ROI.