|
Getting your Trinity Audio player ready...
|
As someone coming from an application security background, stepping into the world of Exposure Management has been both exciting and a bit overwhelming. Since writing has always been my best way to learn, I decided to turn some of my early lessons and insights into a blog series. I hope it will be as insightful for you as it has been for me.
We live in an era of cybersecurity hypervisibility, characterized by a paradox: organizations are drowning in vulnerability data, yet they remain fundamentally exposed to critical breaches. This crisis of volume has security teams worldwide grappling with an overwhelming surge of constantly published vulnerabilities, resulting in an endless stream of alerts. In fact, in 2024 alone, that number reached an all-time high of over 40,000 new vulnerabilities discovered.
The influx of information has turned visibility into a flood, leaving security teams struggling to transform this data into actionable, meaningful insights. This crisis is rooted in the failure to effectively prioritize risks amidst the continuous explosion of new exposures. This failure leads to alert fatigue, overwhelmed staff, and high rates of burnout among SOC analysts.
This blog explores why traditional vulnerability management often fails to deliver meaningful risk reduction and how adopting an attacker’s perspective, which is at the core of modern Exposure Management, helps security teams regain focus, efficiency, and control.
When Critical Means Everything and Nothing
The root of the problem lies in how risk is prioritized. For years, security teams relied on the Common Vulnerability Scoring System (CVSS). This score was only designed to measure a flaw’s technical severity, not its actual contextual risk.
A significant limitation is the static scoring model. CVSS scores are calculated at the time of publication and do not dynamically reflect evolving threat intelligence, real-time exploit development, or shifting attack complexity. Additionally, the scores do not account for the specific context or reality within any particular organization’s environment, such as asset criticality, existing mitigations, or exposure levels.
This severity-based approach lacks context, directing security resources to theoretically critical, but often irrelevant “dead ends”. A “dead end” refers to a security exposure that cannot be exploited by an attacker to reach critical assets and, therefore, poses no actual threat to the organization’s sensitive data or systems.
This is the core of the exposure management challenge: risk is not about how severe a vulnerability appears in isolation, but whether it can realistically be used to compromise something that matters when put in a business context.
The Attacker’s Playbook: Chaining Exposures, Not Scanning CVEs
The shift from vulnerability management to exposure management begins with seeing the environment through an attacker’s eyes. Attackers are not driven by high CVSS scores; they are driven by the path of least resistance. They rarely ever use flashy zero-days; they often just need an “open door” from simple entry points like unpatched systems, misconfigurations, or harvested credentials.
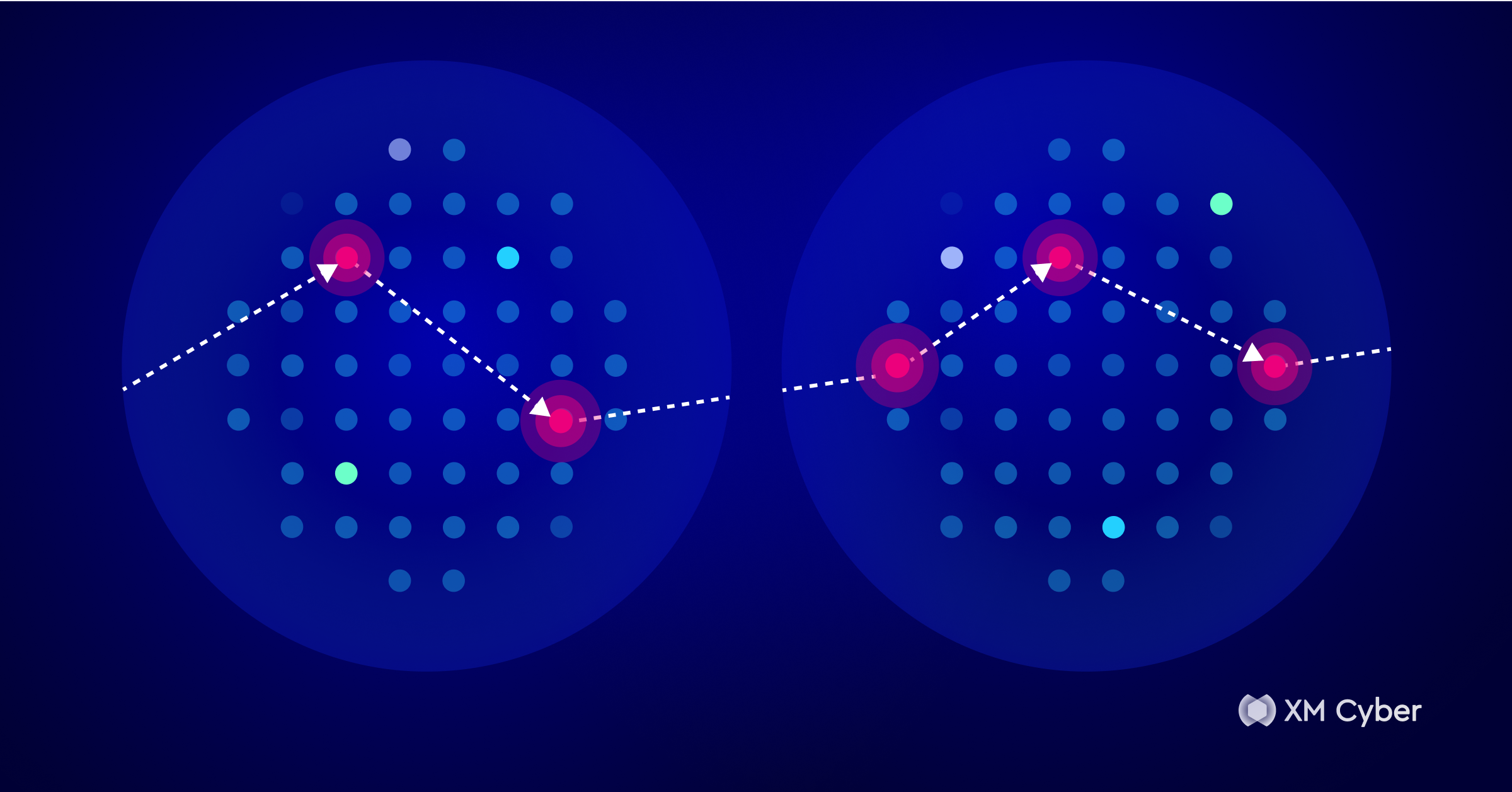
The most damaging breaches rarely involve a single high-severity exploit. Instead, they unfold through a calculated chain of exploitation. Attackers often interconnect multiple low and medium-level exposures: an unpatched server, a misconfigured identity, a forgotten external port, or a reused credential. Each of these might seem minor, but together they create a path to escalation, persistence, and impact.
This focus on the complete attack chain represents a more holistic approach, where we now focus on exposures, not just vulnerabilities. While a single vulnerability might not pose a significant risk, an exposure chain represents the real, uninterrupted path an attacker can take. This path begins with low-privileged initial access and escalates through the exploitation of over-privileged accounts and trust relationships, ultimately leading to substantial business consequences such as data exfiltration or ransomware.
Exposure management focuses on these connections and the context between them. Understanding how exposures interact and which ones enable lateral movement toward critical assets transforms raw visibility into actionable intelligence.
Moving From Risk-on-Asset to Risk-to-Critical-Asset
Organizations can fundamentally flip the script by shifting focus away from a Risk-on-Asset (e.g., this server has a vulnerability) to a Risk-to-Critical-Asset (e.g., how an attacker can get to your sensitive database) approach.
This “Risk-to-Critical-Asset” approach reframes security priorities:
- Instead of asking, “What is vulnerable?” teams ask, “What is exploitable in a way that threatens critical systems?”
- Instead of fixing everything, they focus on the attack paths that pose the highest risk to the organization.
By modeling the relationships between vulnerabilities, configurations, credentials, and identities, defenders can identify where attack paths converge. These convergence points are often the most powerful opportunities to reduce risk efficiently.
Finding Choke Points: Doing More with Less
Fixing every exposure is impossible, but attackers do not use every exposure either. They focus on the ones that connect multiple routes toward valuable targets.
These convergence points, or choke points, are strategic locations in the environment where multiple attack paths intersect. By addressing exposures at these intersections, such as a misconfigured admin account, a weak identity provider, or an overly permissive network segment, organizations can disrupt dozens or even hundreds of potential attack routes at once.
This approach transforms remediation efficiency. By focusing on the small fraction of exposures that block the majority of attack paths, security teams can achieve significant risk reduction while minimizing effort and burnout.
This is where Continuous Exposure Management comes in, and where adopting a platform that leverages an attacker-centric prioritization can help organizations stop attackers before they reach their critical assets.
Continuous Exposure Management: A New Operating Model
Exposure Management is not a one-time project or a quarterly report. It is a continuous practice. The attack surface changes daily as new assets appear, identities shift, and configurations evolve.
To stay ahead, organizations need ongoing visibility into their entire environment, across external, internal, cloud, and identity layers, and a dynamic understanding of how exposures interact.
A mature Exposure Management program integrates several key elements:
- Continuous discovery of all assets and exposures
- Contextual analysis of how exposures connect to critical assets
- Attacker-centric prioritization to guide remediation efforts
- Validation to confirm that remediation actions truly reduce risk
This ongoing cycle ensures that defenders focus their energy where it has the most impact, aligning their actions with real-world attacker behavior and measurable business outcomes.
My Takeaway
Flipping the script on exposure management means replacing volume with context and visibility with understanding.
Organizations that think like attackers, mapping how exposures chain together, identifying choke points in their environments, and focusing on the paths to critical assets, are the ones that achieve lasting, measurable security posture improvements and risk reduction.
Exposure Management is not just about finding everything. It is about prioritizing exposure the way an attacker would.