|
Getting your Trinity Audio player ready...
|
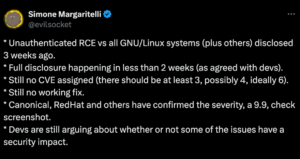
On Sept 26th, security researcher Simone Margeritelli (@evilsocket) disclosed the discovery of 4 zero-day vulnerabilities in the Common UNIX Printing System (CUPS). CUPS is a popular open-source printer support package used by Linux and Unix-like operating systems. These vulnerabilities are being tracked as CVE-2024-47176, CVE-2024-47076, CVE-2024-47175, and CVE-2024-47177 and can be leveraged by attackers to achieve code execution on Linux and certain Unix systems.
How do the CUPS RCE Vulnerabilities Work?
The vulnerabilities impact cups-browsed, libscupsfilters, cups-filter and libppd components of the CUPS printing system, and affect versions <= 2.0.1.When chained together, the vulnerabilities can form an exploit chain that would allow an attacker to create a fake printer on a network-exposed Linux system (such as GNU/Linux, BSDs, ChromeOS, and Solaris) running CUPS and trigger remote code execution upon sending a print request.
According to Margereritelli:
- CVE-2024-47176 | cups-browsed <= 2.0.1 binds on UDP INADDR_ANY:631 trusting any packet from any source to trigger a Get-Printer-Attributes IPP request to an attacker controlled URL.
- CVE-2024-47076 | libcupsfilters <= 2.1b1 cfGetPrinterAttributes5 does not validate or sanitize the IPP attributes returned from an IPP server, providing attacker controlled data to the rest of the CUPS system.
- CVE-2024-47175 | libppd <= 2.1b1 ppdCreatePPDFromIPP2 does not validate or sanitize the IPP attributes when writing them to a temporary PPD file, allowing the injection of attacker controlled data in the resulting PPD.
- CVE-2024-47177 | cups-filters <= 2.0.1 foomatic-rip allows arbitrary command execution via the FoomaticRIPCommandLine PPD parameter.
“A remote unauthenticated attacker can silently replace existing printers’ (or install new ones) IPP urls with a malicious one, resulting in arbitrary command execution (on the computer) when a print job is started (from that computer),” said Margeritelli in his writeup.
According to Security Firm Red Hat (which has disclosed that all versions of their Red Hat Enterprise Linux (RHEL) are vulnerable to this chain of exploits), exploitation would occur as follows:
- The cups-browsed service has manually been enabled or started
- An attacker has access to a vulnerable server, which :
- Allows unrestricted access, such as the public internet, or
- Gains access to an internal network where local connections are trusted
- Attacker advertises a malicious IPP server, thereby provisioning a malicious printer
- A potential victim attempts to print from the malicious device
- Attacker executes arbitrary code on victim’s machine
As of this writing, there was no evidence of these vulnerabilities being leveraged in the wild and no patches have been released yet.
What to do if Your Machines are Vulnerable to CUPS RCE:
- Disable the CUPS-browsed service.
- Update the vulnerable packages listed above, note that for some distributions, patches are still not available.
- If you can’t update the packages or disable the cups-browsed service for some reason, block the traffic to port 631.
This is a developing story and we will update this advisory post as more information becomes available.