|
Getting your Trinity Audio player ready...
|
An age-old cybersecurity cliché is that “you can’t protect what you can’t see.” But in today’s landscape, what you can’t see isn’t just unprotected, it’s likely costing you millions.
Shadow IT is a great example: the hardware, software, and cloud services deployed without IT approval. It’s no longer just a hygiene issue; it is a dominant fiscal and security reality. Gartner estimates that Shadow IT now accounts for 30-40% of large enterprise IT expenditures.
According to IBM, 60% of organizations fail to include Shadow IT in their threat assessments, leaving them vulnerable to potential security breaches. More alarmingly, nearly one in two cyberattacks stems from these unmanaged assets, with the average remediation cost of such breaches exceeding $4.2 million.
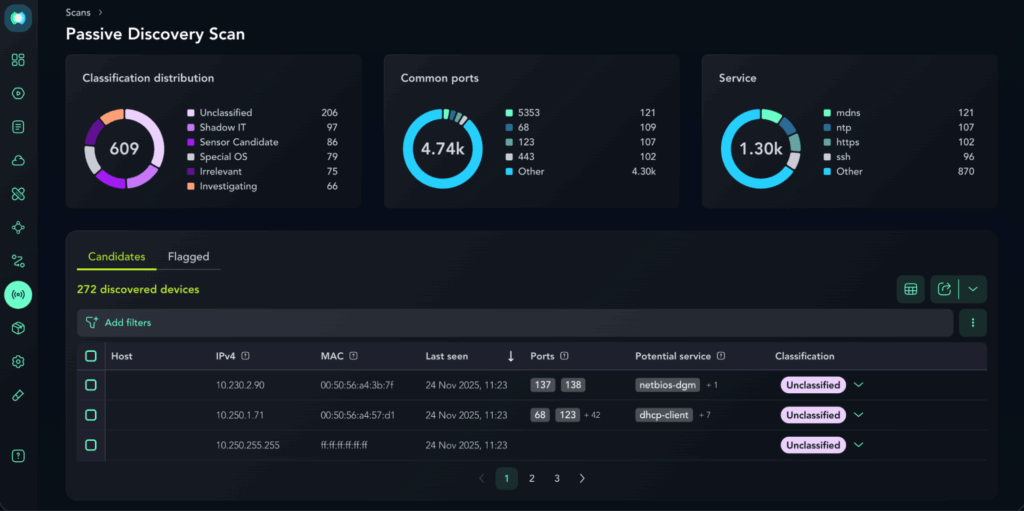
Today, we are introducing Passive Discovery Scanning. This zero-friction discovery capability utilizes the sensors already deployed in customer environments to ensure complete network coverage and identify unmanaged devices, from overlooked VMs to hidden Shadow IT, without requiring new hardware, probes, or workflow disruptions.
Shadow IT is a Bigger Problem Than You Think
Let’s take a step back and discuss the problem first. Shadow IT is more than a collection of unapproved apps, devices, or entities. These assets often operate completely outside the organization’s standard security guardrails. Unmanaged devices are typically not running EDR, are not enrolled in MDM, are not behind NAC enforcement, and do not report telemetry to SIEM or asset inventory systems.
With no visibility, no automated patching, and no policy enforcement, devices that bypass onboarding, such as personal laptops, contractor systems, IoT, or untracked cloud VMs, become blind spots that traditional endpoint tools cannot detect or defend.
These unmanaged assets also frequently use unsupported operating systems, unapproved software, or SaaS without SSO, MFA, or CASB controls. As a result, standard policies around permitted OS versions, patch cycles, and approved applications simply do not apply. These gaps materially increase the likelihood of attackers finding easy entry points, spending more time inside the environment, and moving or extracting data undetected
This is why Shadow IT has become both a financial drain and a security multiplier, driving higher breach frequency and remediation costs. Continuous discovery, strong identity and network-level policy enforcement, and rapid remediation are now essential to reduce the growing risk created by unmanaged assets.
What is Zero-Friction Discovery?
Traditional network discovery often requires expensive appliances, VLAN rearchitecture, SPAN ports, or network taps. These approaches take time, create friction between IT and security, and can be difficult to deploy at scale.
Passive Discovery Scanning takes a different approach. Instead of scanning devices directly, we leverage your existing sensor grid as passive listening points. These sensors observe ARP, broadcast, DHCP, DNS, and other traffic that devices naturally emit on the broadcast domain. The result is continuous discovery without sending a single probing packet to the target.
This approach allows organizations to expand discovery coverage quickly and with significantly lower operational overhead.
Safe for OT, Legacy Systems, and Fragile Devices
Because Passive Discovery Scanning is observational and does not transmit traffic to endpoints, it offers a low-risk method to gain visibility into devices that have historically been difficult or unsafe to scan.
This includes:
- IoT devices such as cameras, printers, and meeting room hardware
- Legacy systems, including AIX, Solaris, or mainframes, that cannot support modern agents
- OT and ICS environments where active probing is restricted or discouraged
Passive Discovery Scanning adds visibility where it was previously unsafe or impossible, allowing teams to account for every asset without creating operational disruption.
Complete Visibility is at the Core of Exposure Management
Without knowing what devices exist, no organization can reliably measure or prioritize exposure. The discovery capability helps security teams close visibility gaps and build a complete picture of the attack surface.
With the new release, organizations can:
- Remove Unauthorized Devices: Identify and remove Shadow IT for stronger hygiene and a reduced attack surface.
- Expand Security Coverage: Identify “Sensor Candidates” across on-prem and cloud environments that need to be brought under management.
- Monitor the Unmanageable: Tag critical legacy or OT systems as “Special OS.” Once classified, these assets can be monitored to trace potential attack paths and prevent exposures, even without a sensor installed.
By discovering both managed and unmanaged assets, teams gain a more accurate representation of their environment and can prioritize risk with greater confidence.
Turning Discovery into Remediation
Discovery is valuable only when it leads to action. Passive Discovery Scanning integrates directly into the existing remediation workflow so that discovered devices can be triaged, classified, and addressed in the platform without manual copying or external correlation.
- Discover
The Scans dashboard automatically populates with assets detected by sensors.
Each entry includes enrichment such as IP, MAC address, hostname, VLAN,
and last seen time. - Classify
Assets can be assigned to actionable categories such as:- Shadow IT: Unauthorized or unmanaged devices requiring takedown.
- Sensor candidate: Standard IT assets needing security sensor installation.
- Irrelevant
- Investigating
- Monitor without Sensor (Special OS): Known, critical devices (like OT or AIX servers)
where sensor deployment is impossible. These can be tagged to trace attack paths.
- Remediate
Users can export findings for IT or procurement teams, or mark risks as accepted
based on policy. This creates a consistent workflow from discovery to action,
ensuring that visibility leads to a measurable reduction in exposure.
About the XM Cyber Continuous Exposure Management Platform
The XM Cyber Continuous Exposure Management Platform cuts through the noise of endless alerts to show you exactly how vulnerabilities, misconfigurations, and identity issues combine to threaten your business. We don’t just guess at risk; we validate it. The platform pinpoints the critical choke points in your environment, allowing you to sever dangerous attack paths with a fraction of the effort. Instead of chasing theoretical risks, XM Cyber helps you focus remediation on the exploitable exposures that directly impact your critical assets and provide data-driven certainty to prove security posture improvements.