Automated Security Validation
Reduce the likelihood of breaches and improve cyber resilience by continuously verifying the effectiveness of your security program and security controls in blocking real-world attacks.
XM Cyber Named Leader 2nd Time in a Row for Automated Security Validation.
“… an interconnected, attacker-centric view of the full attack surface—all modeled in a digital twin to safely simulate attack paths without impacting production.”

Security Validation is an Integral Part of Continuous Exposure Management
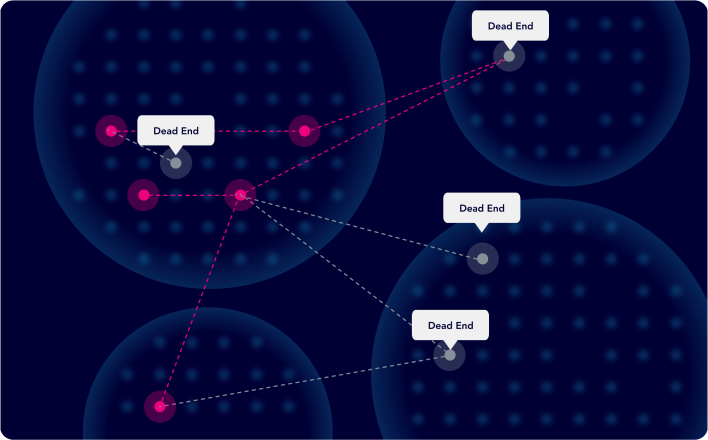
Leverage the XM Attack Graph for Exposure Validation
Identify the exposures that are exploitable in your environment based on XM Attack Graph Analysis™ and focus on fixing them first to increase security and efficiency
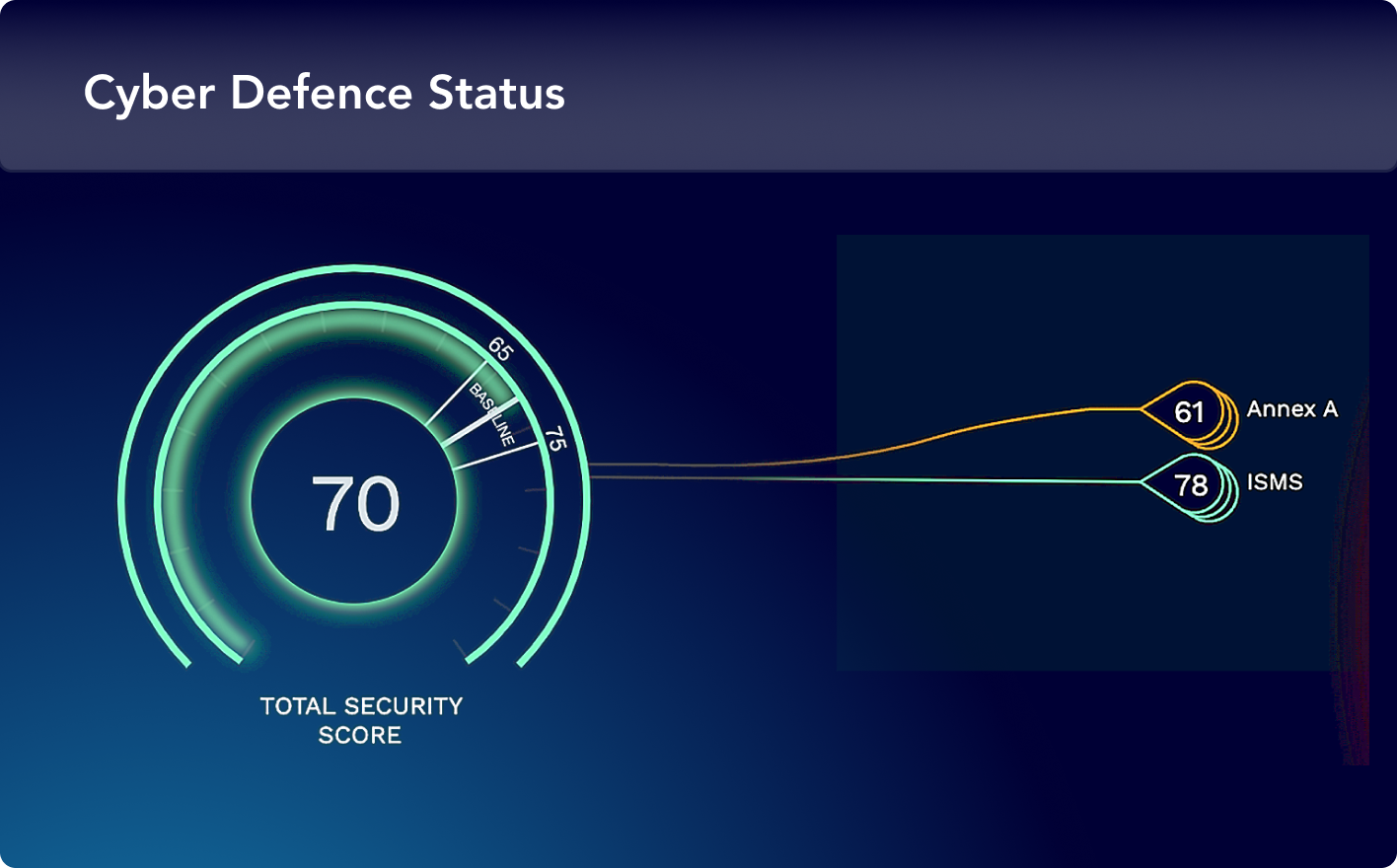
Verify the Effectiveness of Security Controls
Monitor security controls for misconfigurations to reduce risk, ensure compliance with policies and regulations, and integrate results into the attack path
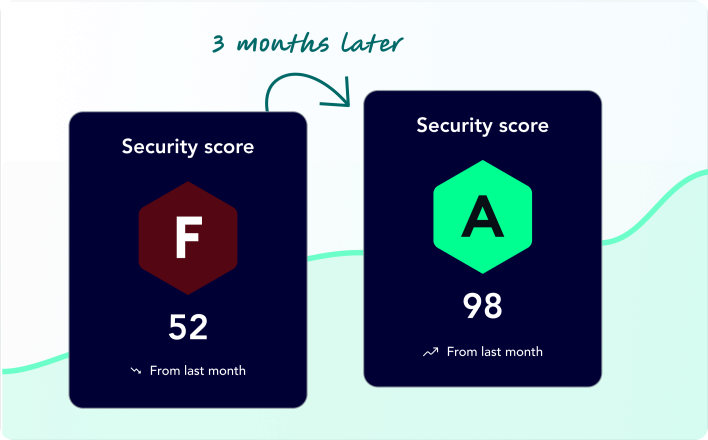
Confirm Remediation Reduces Risk
Validate applied fixes block attack scenarios and improve security posture in order to gain confidence and improve reporting to management
FAQS
What is Automated Security Validation?
Automated Security Validation (ASV) ensures continuous and comprehensive validation of your security posture, identifying exposures before they can be exploited by attackers. ASV adds the adversary’s perspective of exposures and helps security teams prioritize high impact exposures and reduce the remediation workload.
Why Do You Need Automated Security Validation?
By automating the validation process, Security teams reduce the reliance on manual testing, saving time and resources while increasing accuracy and coverage. This proactive approach allows organizations to detect and remediate security gaps, maintaining protection against emerging threats.
Security validation is more valuable and reliable when integrated with comprehensive discovery, assessment, and prioritization of vulnerabilities and exposures across the hybrid environment.
Why Do You Need XM Cyber for Automated Security Validation?
ASV as part of the XM Cyber Continuous Exposure Management platform is essential for staying ahead of attackers. Combine the leading ASV with XM Cyber unique capabilities of Exposure Assessment to block high-impact attacks and gain remediation efficiency with the most comprehensive platform for adopting Continuous Threat Exposure Management (CTEM).
See XM Cyber in action