Protect Your Business from the External Attack Surface
Proactively discover, validate, prioritize, and remediate external-facing exposures and stolen credentials that actually compromise your business before they are exploited.
All About Infostealers and How to Block Them
End-to-End Exposure Management:
From the Outside In
Proactively discover and mitigate breach points, starting from the external attack surface, all the way to on-prem or cloud based critical assets to focus prioritization and remediation efforts on actual exploitability and impact on your business.
Eliminate Blind Spots and Filter Noise to Fix What Matters
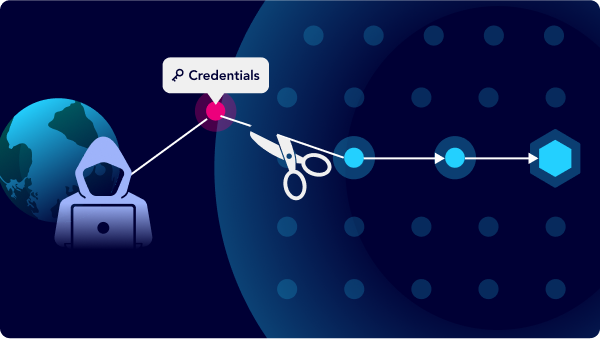
Continuous Infostealer Monitoring to Stay Ahead of Attackers
Proactively find compromised credentials and stop threats before they are exploited. Map stolen credentials to human and non-human identities to visualize how they compromise critical assets.
Ongoing Discovery of Holistic External Attack Surfaces
Get real-time discovery and monitoring of internet-facing assets and investigative agentless scans to continuously prevent attacks. AI-based pattern matching protects your organization from phishing attempts.

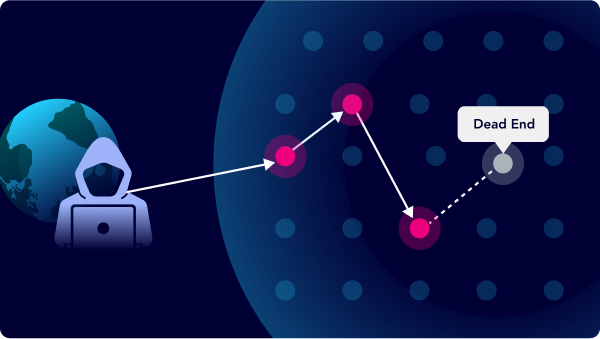
Proactive Validation with Autonomous Pentesting and End-to-End Attack Paths
Eliminate false positives by emulating real-world multi-dimensional attacks and filter out non-exploitable exposures in your environment by leveraging threat intelligence and end-to-end attack graph analysis™.
Prioritization and Remediation Based on Context of Risk to the Business
Map external assets to internal systems while tracking compromised credentials linked to users and machines, to show which exposures pose the greatest risk to critical assets, so you can prioritize the most important fixes first.

FAQS
What is External Attack Surface Management (EASM)?
EASM is a comprehensive cybersecurity practice that involves the continuous discovery, classification, validation and monitoring of all an organization’s internet-facing digital assets and exposures. It aims to provide visibility into your digital footprint from an attacker’s perspective, including known, unknown, and rogue assets.
Why is EASM critical for modern organizations?
EASM is critical because the modern enterprise has an ever-expanding digital footprint (due to cloud, remote work, M&A, shadow IT), and most cyberattacks target this external exposure. EASM helps proactively identify and remediate exposures before they can be exploited, reducing the likelihood of a successful breach and protecting reputation.
What are common challenges organizations face with EASM?
Common challenges include asset sprawl (managing rapidly growing and changing assets), shadow IT (discovering unauthorized systems), resource constraints, alert fatigue, integration complexity with existing tools, and organizational silos.
How does EASM provide actionable insights that go beyond traditional vendor assessments to genuinely protect organizations from Third-Party Risk Management?
The digital supply chain has become one of the most significant attack vectors. Traditional Third-Party Risk Management (TPRM) often relies on static questionnaires and certifications, which provide a ‘snapshot in time’ and can miss critical, real-world exposures. XM Cyber EASM revolutionizes this by offering continuous, attacker-centric visibility into your third-party ecosystem.
What is XM Cyber’s approach to External Attack Surface Management (EASM)?
XM Cyber goes beyond traditional EASM by interconnecting external exposures into the holistic attack graph. This empowers security leaders to prioritize and remediate exposures across the full attack surface based on exploitability and risk to the business. It doesn’t just identify assets, but reveals how attackers can chain together seemingly minor exposures across attack surfaces to compromise critical business assets, providing a holistic, contextualized view of risk.
What are the key benefits of implementing XM Cyber’s EASM solution?
Key benefits include eliminating blind spots by discovering unknown assets, reducing cyber risk by proactively identifying and remediating the external exposures that compromise critical business assets, enhancing compliance, improving threat prioritization, protecting brand and reputation, and gaining insight into how adversaries view your organization.
Who specifically benefits from XM Cyber’s EASM solution?
Various stakeholders benefit, including CISOs & Security Leaders (for executive visibility and quantifiable improvements), Security Operations Teams (for focusing on high-impact vulnerabilities), Risk & Compliance Officers, Cloud Security Teams (for securing sprawling cloud environments), IT Operations Teams (for prescriptive remediation guidance and verification) and M&A Teams (for quickly assessing acquired entities’ security posture).
How does EASM complement XM Cyber’s Continuous Exposure Management platform?
The EASM module extends the coverage of XM Cyber’s Continuous Exposure Management platform to the full attack surface by adding external-facing assets and certificates, as well as compromised credentials. With EASM XM Cyber’s platform proactively discovers, validates, prioritizes, and triggers remediation for exposures from the external attack surface to the internal network, across on-prem and multi-cloud environments, for all exposures types and interconnected attack paths.
What technologies or processes make up a comprehensive EASM solution?
A comprehensive EASM solution typically includes automated asset discovery, asset classification, vulnerability assessment, exposure validation, risk prioritization that incorporates threat intelligence as well as business context, continuous monitoring, remediation guidance, integration capabilities with other security tools (SIEM, SOAR), and robust reporting/analytics.
How does EASM help address risks from third-party integrations or cloud environments?
EASM extends visibility beyond an organization’s direct control. It helps manage risks associated with third-party integrations by identifying potential vulnerabilities in connected systems. For cloud environments, it discovers sprawling cloud assets and identifies misconfigurations or unmanaged resources that are exposed to the internet, providing essential multi-cloud visibility.
Get a Demo









