|
Getting your Trinity Audio player ready...
|
The attack surface of organizations keeps expanding to support digitization and business initiatives. As organizations expand their digital presence, forces such as continued cloud adoption, the use of SaaS platforms, and ever-increasing reliance on third-party vendors add up to an attack surface full of potential exposures and vulnerabilities, leaving organizations to confront an array of challenges.
EASM to Help Complete the CTEM Picture
In this light, it’s understandable why organizations look to solutions that can help them understand the growing complexity of their attack surface. Here on these pages we tend to talk a lot about the deep and wide value of establishing a holistic Continuous Threat Exposure Management (CTEM) program to reduce risk and increase security posture. Broken down into 5 stages – Scoping, Discovery, Prioritization, Validation and Mobilization – the first two stages deal with understanding your attack surfaces and how important each asset is to your business, both of which will change over time. It includes identifying key attack surfaces and assessing each asset for potential exposures and analyzing how the exposures correlate particular risks.
External Attack Surface Management (EASM) solutions have emerged as a beneficial way to meet Scoping and Discovery stages of CTEM. These tools can discover internet-facing enterprise assets and systems and associated exposures. Examples include exposed servers, public cloud service misconfigurations and third-party partner software code vulnerabilities that could be exploited by adversaries.
The attacker’s view of your organization:
But There Are Still Too Many Issues to Address….
But the high volume of public-facing entities (you wouldn’t believe all the assets that you have that are internet facing…) and of exposures (including false positives) is often unmanageable. Therefore EASM is only as effective as its ability to also provide validation and prioritization of the identified exposures. Validation is often addressed by running an active scan. Prioritization can be done in several ways:
- CVSS – Common Vulnerability Severity Score – We’re all (too) familiar with CVSS scoring. This open framework is used by organizations to determine the severity of cybersecurity vulnerabilities. These scores provide a valuable common benchmark for cybersecurity teams, who use CVSS scoring as part of their vulnerability management programs. But the CVSS base scores only represent the severity of a vulnerability. They do not consider the risk that severity poses to your specific environment. Without that key risk context, it is impossible to prioritize vulnerability remediation effectively.
- EPSS – Exploit Prediction Scoring System Exploitability – This metric looks at the likelihood of an exposure being exploited in the wild. According to FirstOrg.com, the group responsible for EPSS “This metric looks at how many breaches and threat actors are using this exposure for a successful attack.” EPSS score is dynamic and changes with new exploits of the vulnerability in each breach, but it doesn’t tell you how exposures can affect your environment.
- Exploitability and Impact in YOUR Environment – This level of prioritization connects your attack surface with powerful attack path management to find the attacker’s view of how to exploit an exposed external-facing asset to compromise your critical assets. This enables you to find out which exposed public-facing assets actually compromise critical assets, and how to remediate exposures efficiently by identifying choke points and mobilizing IT with the appropriate justification, guidance, and alternatives.
Using these 3 levels of prioritization enables organizations to effectively prevent high-impact attacks from the external attack surface to critical assets. With accurate and relevant context, plus the power of seeing how exposures lead to attack paths, organizations can build out truly holistic and comprehensive CTEM programs that fulfill the promise of reducing risk and increasing security posture.
XM Cyber’s New EASM Extension
That’s why we are excited to launch our new EASM capabilities. This new extension, in response to the evolving cyber threat landscape, empowers organizations to proactively manage and defend against cyber threats by providing unparalleled visibility into the attacker’s journey – from the initial planning to compromising critical assets.
Key capabilities of XM Cyber’s EASM extension:
- Discovery of Exposed Public-Facing Assets: Identifying internet-facing assets and monitoring them for vulnerabilities and risks allows customers to prioritize and remediate exposures that provide attackers an initial foothold and lead to a breach.
- Exposed Credentials Discovery and Prioritization: Monitoring Infostealers for stolen and leaked credentials identifies employees and customer accounts that are at risk, and enables customers to force password change, revoke active sessions, and enforce stronger authentication to block the use of these credentials.
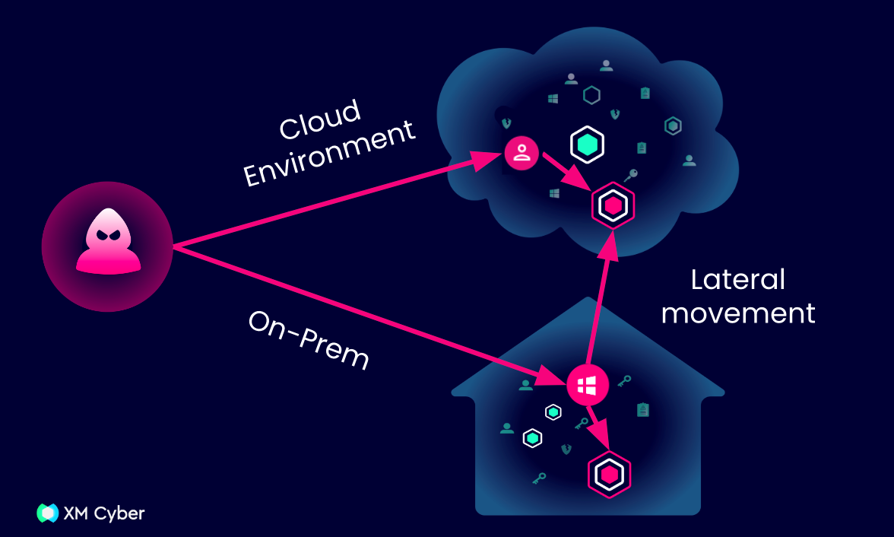
- Impactful Remediation Prioritization: As mentioned above, identifying exposed assets and credentials, and then flagging them as breach points, offers a strategic advantage in visualizing the complete attack path, from the external attack surface, across on-prem and cloud environments, to the critical assets. This allows organizations to prioritize remediation efforts based on exploitability and impact, ensuring a more effective cybersecurity posture.
Conclusion
Regardless of whether an attacker breaches the on-prem or cloud environments, they can leverage lateral movement and reach critical assets anywhere in your environment. To remain one step ahead, you need to be able to discover, visualize, and prioritize all exposures across the attack path end-to-end. In order to be able to reduce risk with an actionable remediation plan, organizations integrate their attack surface management into their CTEM program.
Learn more about how XM Cyber can help you reduce risk and improve security posture across your organization.


