What is Continuous Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management (CTEM) is a proactive and continuous five-stage program, or framework, that reduces exposure to cyber attacks. It helps organizations identify vulnerabilities and exposures, correlate them to potential attack paths, prioritize them based upon their risk to critical assets, and monitor progress as they implement remediation activities. Organizations worldwide are leveraging CTEM to efficiently address exposures and improve their security posture.
CTEM continually assesses an organization’s entire ecosystem – including networks, systems, assets, and more – to identify exposures and weaknesses. Having a CTEM program enables continuous improvement of security posture by identifying and remediating potentially problematic areas before attackers can exploit them.
What Traditional Approaches Get Wrong
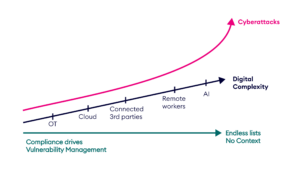
Security programs rely on outputs from vulnerability scanners, misconfiguration checkers, and identity systems. These tools flag issues, but they do not explain how those issues create exposure. Each list exists in isolation, with no connection to attacker movement or asset impact.
CTEM closes this gap. It links findings into full paths that show how attackers reach critical assets. Security teams can then work from a complete map, focusing on exposure that creates access, movement, or privilege escalation. This produces clearer decisions and more reliable outcomes.
What Problem Does CTEM Solve?
Today, security teams collect exposure data from multiple tools, each focused on a different domain. Vulnerabilities, identity risks, and misconfigurations appear in separate lists, often without shared context or clear starting point.
Some exposures can be remediated. Others remain in place due to system constraints or lack of ownership. Teams frequently can’t determine which fixes actually reduce exposure. They lack a way to trace remediation efforts back to specific attack paths or confirm whether those paths have been closed.
CTEM provides a framework that helps organizations bring structure to this process. It connects exposures to attacker movement, surfaces the paths that reach critical assets, and defines a sequence of actions that move posture forward.
Why is CTEM Valuable?
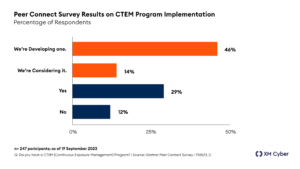
CTEM is valuable because it helps organizations reduce a large, unmanageable exposure problem into clear, measurable improvements. In XM Cyber’s own research, we found that:
- Larger enterprises can have over 250,000 open vulnerabilities.
- Firms only fix about 10% of those open vulnerabilities, leaving the rest in place.
- 75% of exposures don’t lead to another asset – they are “dead ends” to attackers. Only 2% lead to critical assets.
Forrester’s Total Economic Impact Study found a 90% reduction in likelihood of a severe breach for those organizations with a proper solution in place, and an ROI of up to 400%. Moreover, Gartner claims that “By 2026, organizations prioritizing their security investments, based on a continuous threat exposure management program, will realize a two-third reduction in breaches.”
Why is CTEM the Right Solution?
CTEM addresses the core limitations of traditional security programs. It replaces fragmented findings with a connected view of exposure and provides a structured process for acting on it. Gartner notes that “CTEM programs expand traditional cybersecurity assessment” and help “align the scopes of exposure assessment cycles with specific business projects and critical threat vectors.” They also “validate the enterprise’s exposure and remediation priorities by including the attacker’s perspective, and testing the effectiveness of security controls and incident response processes.”
This makes CTEM the right solution – a practical and repeatable framework for reducing real risk across the organization.
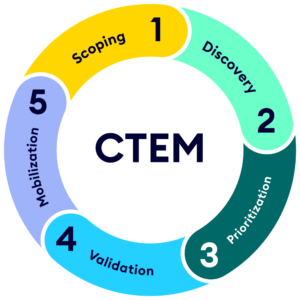
What are the 5 Stages of CTEM?
CTEM is a framework for exposure reduction. Although it isn’t a product or service, the right product or platform can help implement it in your organization.
The five stages of CTEM are:
Stage 1 – Scoping
Scoping defines which parts of your environment are evaluated and how exposure is measured. CTEM treats scoping as a deliberate alignment of business-critical assets, identity systems, and access paths based on how attackers can realistically move. This stage helps you understand your attack surfaces and how important each asset is to your business. It requires input from various decision-makers, such as leaders from IT, Legal, GRC, Dev, R&D, Product, and Business Ops teams.
Stage 2 – Discovery
Discovery in CTEM focuses on reachability. Assets, identities, and configurations only represent exposure when they can be combined into paths that an attacker can use. That’s why the discovery stage assesses each asset for potential exposures and analyzes how the exposures correlate to particular risks. This includes all types of exposures – such as Active Directory, identity and configuration risks.
Stage 3 – Prioritization
In the prioritization stage, exposures are analyzed to weigh the level of known threat they’ve posed in the wild and the importance of the assets directly impacted. Since CTEM prioritizes exposure based on attack paths, issues grow in priority when they enable lateral movement, privilege escalation, or access to critical assets. This step is crucial, because large organizations often have far more exposures than they’ll ever be able to fix. Prioritization aligns remediation with how attackers progress through real environments rather than relying on severity scores alone.
Stage 4 – Validation
Validation confirms whether remediation actions will actually eliminate attack paths. This stage evaluates the environment after changes are made to verify that access routes are broken and exposure is reduced as intended. Without validation, fixes remain assumptions – and configuration drift, partial remediation, or changes elsewhere in the environment can reopen the same paths. CTEM treats validation as proof that exposure has been closed and that risk reduction persists over time.
Stage 5 – Mobilization
This stage ensures shared understanding of roles within the CTEM program. Mobilization succeeds when security and IT teams share clarity on priorities, ownership, and decision paths. Each remediation action ties to a defined risk reduction outcome. This helps teams focus on work that matters most. Clear expectations speed execution and reduce handoffs. Standard reporting shows progress across assets and controls, supports leadership review, builds accountability, and demonstrates steady improvement in security posture through consistent, coordinated action over time.
CTEM vs. RBVM
Risk-based Vulnerability Management (RBVM) ranks CVEs using threat data and asset value. It helps teams decide which vulnerabilities to fix and in what order. This model works well for known risks but doesn’t address exposures that fall outside traditional scoring.
Many environments include identity flaws, misconfigurations, and permission gaps that never appear in RBVM dashboards. These exposures can be chained together by attackers and used to reach critical assets, even when CVEs are fully patched.
CTEM-based products include those overlooked conditions. They evaluate all exposures based on how they create access, enable movement, or escalate privileges. This approach helps teams decide what to fix by showing how attackers would move through the environment, not just what vulnerabilities exist.
The framework supports a shift from list-based cleanup to targeted risk reduction. It gives teams a structure for deciding where effort matters most and how to measure the effect of each fix.
CTEM vs. Red Team Exercises
Red Team exercises simulate how an attacker might reach sensitive systems. They test how security controls respond, how alerts flow, and how quickly teams detect activity. Each exercise has an objective and runs with a defined scope.
The process shows what’s possible, but not what’s probable. It reveals gaps in response but doesn’t provide full visibility into exposure. Moreover, these exercises are often complex to run and limited by schedule, budget, and internal access.
CTEM-based platforms support broader coverage. They map how attackers could reach assets using conditions that already exist, taking into account chained exposures, lateral paths, and structural weak points that don’t show up during one-off tests.
CTEM vs. Penetration Testing
Penetration tests check whether a system or application can be breached. The tests usually target a specific area and focus on known vulnerabilities. The results are often used for audits, compliance, or project sign-off.
The value of pentests depends on timing and scope. These tests run on a schedule, assess a slice of the environment – but lose their relevance once configurations shift. They rarely show how issues connect or how risk spreads across systems.
CTEM-based platforms take a broader view. They connect exposures across all environments – cloud, on-prem, hybrid – and show how attackers could use them together. The process includes more than CVEs. It covers misconfigurations, credential issues, and overlooked access paths.
CTEM vs. Breach and Attack Simulation (BAS)
Breach and Attack Simulation (BAS) tools test how well defenses perform under known conditions. Some simulate attacks. Others validate whether controls respond as expected. These tools are often used during policy reviews or system upgrades.
The tests are automated, but the coverage is limited. Each run touches a subset of the environment and depends on preloaded attack techniques. Live testing can also pose operational risks and is often restricted to avoid disruption.
CTEM works from actual exposure, not staged inputs. It analyzes the environment continuously, tracking which conditions are in place and how attackers could use them. The results reflect how risk accumulates and where movement is possible. That’s why teams can use CTEM-based findings to focus on the exposures that shape actual access—not just test results.
CTEM vs. IAM and ITDR Solutions
Identity and Access Management (IAM) and Identity Threat Detection and Response (ITDR) tools monitor who has access and how identities behave. They help teams contain misuse, enforce policy, and detect suspicious changes.
These platforms focus on identity alone. They do not assess how identities interact with infrastructure, applications, or configuration gaps. They also do not map how attackers use multiple exposures – identity-related or otherwise – to reach critical systems.
CTEM-based products view identity conditions as part of a larger threat model. They evaluate how identity posture combines with other weak points to form lateral movement paths. This helps teams understand how access is gained and how attackers move once inside. The result is a view that reflects how environments are structured, not just how identity is managed.
CTEM vs. External Attack Surface Management (EASM)
External Attack Surface Management (EASM) scans the internet-facing perimeter. It catalogs assets, monitors for changes, and highlights exposed services. This view is helpful for understanding what attackers can see from outside the network, but the analysis ends at the edge. EASM does not show what happens after initial access or whether exposures lead to deeper compromise. It surfaces visibility, not movement.
CTEM connects the outside to the inside. It traces whether entry points link to misconfigurations, permissions, or overlooked systems that enable attacker movement. It identifies paths that connect access to impact.
CTEM vs. Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) tools monitor for cloud misconfigurations and compliance issues. They flag settings that break policy and report on changes across infrastructure-as-code, services, and user roles.
The scope stays within the cloud. CSPM helps protect cloud assets but does not account for hybrid environments or show how risk spreads between systems. It also does not rank which exposures matter most.
They also don’t map cloud posture as one part of the larger picture. They connect cloud conditions to identity gaps, network paths, and adjacent systems. That integration allows teams to see how attackers use cross-environment exposure to reach high-value assets. The framework creates a process for managing exposure across cloud, on-prem, and everything in between.
What to Look for in a CTEM-Based Product
Evaluating CTEM-based products starts with a clear set of questions. The goal is to understand what the platform detects, how it maps exposure to risk, and how it supports remediation. Each capability should reflect real conditions in the environment and help teams act with focus, consistency, and shared understanding. Look for:
- Exposure coverage
Look at which types of exposures the solution can detect. That includes CVEs, misconfigurations, identity issues, cloud posture gaps, and unused permissions. Broader coverage gives a clearer view of how conditions build toward risk. - Environment coverage
Check how much of your environment the platform can analyze. That includes endpoints, cloud services, containers, user behavior, and configuration layers. Full visibility across systems supports more accurate attack path analysis. - Risk mapping
Evaluate how the tool connects exposures to assets and how it models attacker movement. A strong platform shows how risks form – not just where they sit – and presents that view in ways both security and IT teams can use. - Remediation logic
Review how the solution ranks what to fix. Stronger platforms show which exposures create access to critical assets and which ones do not. That helps focus action where it prevents the most damage. - Remediation support
See whether the product offers guidance for how to fix what it finds. Clear, specific recommendations help reduce delay, especially when security and IT teams work from the same data. - Ongoing analysis
Ask how often the system evaluates new exposures. Continuous assessment helps track change and catch newly formed paths before they become active risk. That includes new vulnerabilities, new users, and updates across environments. - Reporting output
Review how the platform presents posture trends and risk summaries at the executive level. Teams need to answer basic questions clearly: where risk sits, what’s been fixed, and how posture is shifting over time. - Deployment impact
Assess the operational footprint. That includes how easily the product installs, how it scales, and whether it introduces performance concerns in production systems. Low-risk deployment supports faster adoption.
Another way to evaluate vendors is to consider these questions, and how different vendors answer them.
✔️ Which of my critical assets are at risk today?
✔️ What paths would allow an attacker to reach them?
✔️ Where are all the exposures in my environment?
✔️ Which ones are most important to remediate to protect my critical assets (i.e. choke points)? Which are least important (i.e. dead ends)?
✔️ How can you show me an overall score or assessment of my posture in protecting my critical assets? Can you help me demonstrate improvement over time?
Does CTEM Cover Both On-prem and Cloud Environments?
Most organizations operate across cloud, on-prem, and remote infrastructure. These environments are managed through different systems but remain tightly connected. Identities span platforms, configurations interact, and access moves between them without friction.
CTEM-based products assess how exposures develop across this full landscape. The goal is not to treat each layer in isolation, but to understand how conditions across domains create real attack paths. That includes misconfigured cloud policies, exposed on-prem assets, and accounts that bridge the two.
For more information on how XM Cyber incorporates your cloud environment into a CTEM solution, check out The Power of Attack Paths in the Cloud.
To understand attack surfaces, attack paths to critical assets, and overall risk, all these environments must be considered in a holistic way – the way an attacker will view them.
Why Should I Choose XM Cyber for CTEM?
XM Cyber provides the full set of capabilities needed to operationalize CTEM. The platform supports every stage of the framework, from mapping assets to tracking remediation. It helps teams focus on the exposures that matter, measure the impact of their efforts, and improve posture across connected environments.
Scoping – XM Cyber maps business processes to the underlying assets they depend on. This helps teams prioritize based on the potential impact of exposure to the business.
Discovery – The platform detects both CVEs and non-CVE exposures, including misconfigurations, identity risks, and over-permissioned accounts. Discovery spans internal, external, on-prem, and cloud environments.
Prioritization – Attack Graph Analysis ranks exposures based on threat intelligence, path complexity, asset importance, and the role of choke points. This helps teams understand which fixes interrupt attacker movement.
Validation – XM Cyber validates whether exposures are exploitable and whether controls are configured to block movement. This confirms that remediation efforts reduce actual risk.
Mobilization – Remediation is guided by context, supported by alternative fix paths, and tracked across integrated systems. The platform connects to ticketing, SIEM, and SOAR tools to maintain visibility as posture shifts.
FAQ
What is CTEM and how does it work?
CTEM is a five-stage framework for identifying, prioritizing, and reducing exposure across your environment. It helps organizations understand how attackers move through systems and focus on the conditions that enable access.
How is CTEM different from vulnerability management?
CTEM evaluates all exposure types, not just CVEs. It maps how those exposures connect to real attack paths and shows which ones actually lead to risk.
Does CTEM require a specific product?
CTEM is a framework, not a product category. CTEM-based platforms help implement the process by providing detection, analysis, validation, and tracking capabilities.
What types of exposures does CTEM-based technology detect?
CTEM-based products detect vulnerabilities, misconfigurations, identity gaps, and permission issues. The goal is to capture the full set of conditions that shape attacker movement.
Can CTEM be used across hybrid environments?
Yes. CTEM-based platforms analyze cloud, on-prem, and remote systems together, showing how exposures form across connected environments.
How does CTEM help with remediation?
The framework connects each fix to attacker movement and critical assets. This helps teams focus on actions that disrupt real attack paths.
What makes CTEM different from Red Teaming or pen testing?
Red Teaming and pen tests provide point-in-time assessments with narrow scope. CTEM supports continuous visibility and broader coverage across the full environment.
How can I tell if a CTEM-based platform is effective?
Look at what it detects, how it maps exposure to risk, and how it supports action across teams. It should help track posture over time with clear, operational outputs.
Who benefits most from CTEM?
Any organization with a formal security program can benefit. The framework supports better prioritization, clearer reporting, and stronger alignment between security and IT.
What results can CTEM help deliver?
CTEM helps reduce the number of exposures that lead to critical assets. Organizations use it to improve efficiency, track posture, and lower breach risk.