XM Cyber Delivers Innovative Security Solutions for Digital Resilience with Google Cloud
XM Cyber Delivers Threat Exposure Insights and Context with Google Cloud
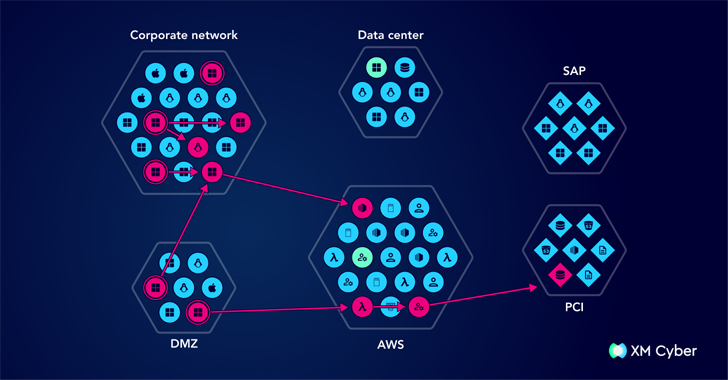
Five exposure gaps that can get past PAMs
Redefining Cyber Value: Why Business Impact Should Lead the Security Conversation
Netpoleon Partners with XM Cyber to Continuously Reduce Risk
Security Tools Alone Don’t Protect You — Control Effectiveness Does
SB Technology Partners with XM Cyber to Bring Continuous Exposure Management to Leading Enterprises in Japan
Make the move to more meaningful metrics
Trinity partners with XM Cyber to bring CTEM to leading enterprises in the UK
SiS Technologies Announces Strategic Distribution Agreement with XM Cyber to Enhance Cybersecurity Resilience in Asia
AWS EKS Security Best Practices Security Theater: Vanity Metrics Keep You Busy – and Exposed
Outsmarting Cyber Threats with Attack Graphs
Request a demo