Vulnerability Assessment
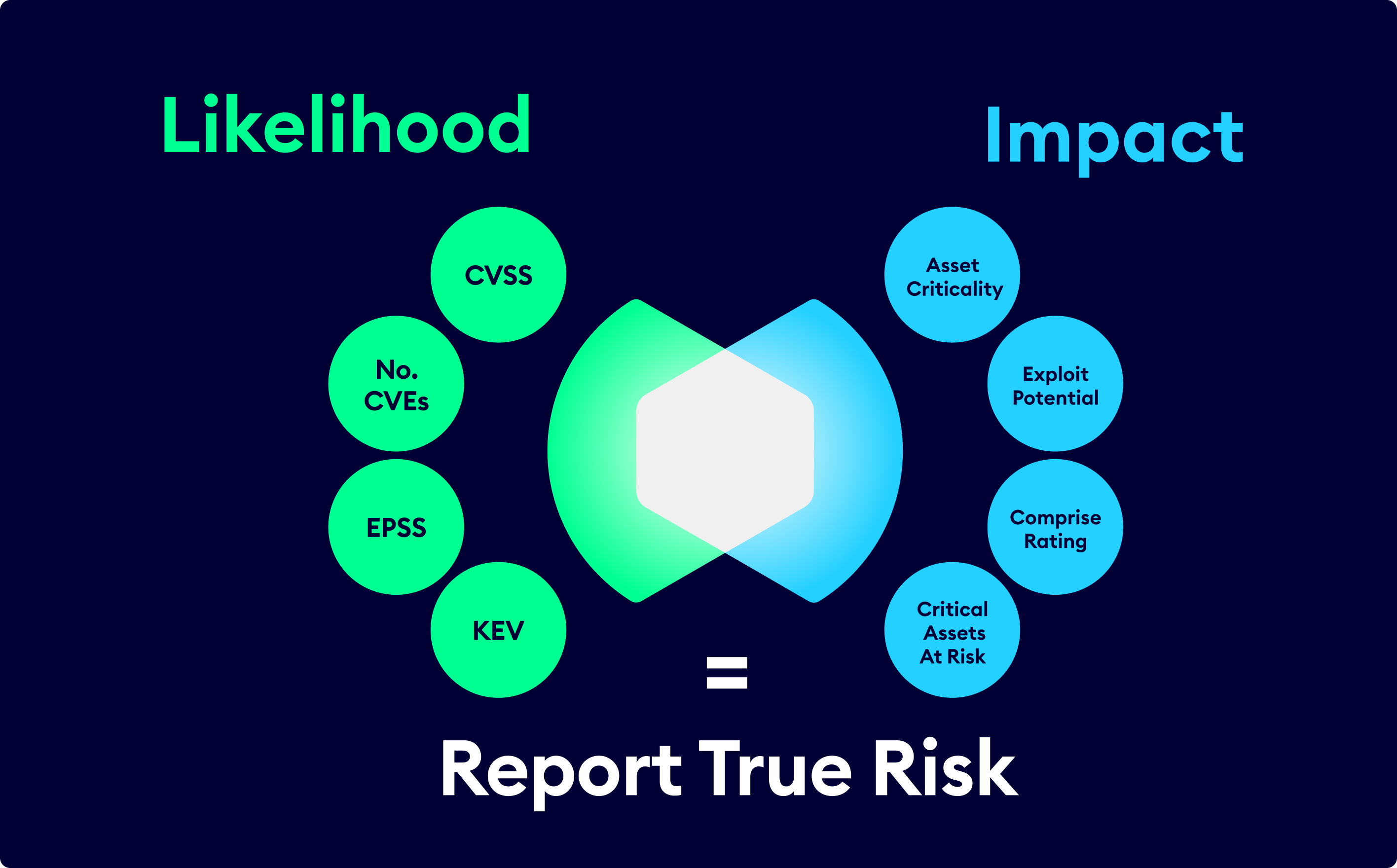
Contextual Vulnerability Risk from Intrusion Likelihood to Business Impact.
Focus Remediation and Patching Efforts on
High-Impact Vulnerabilities
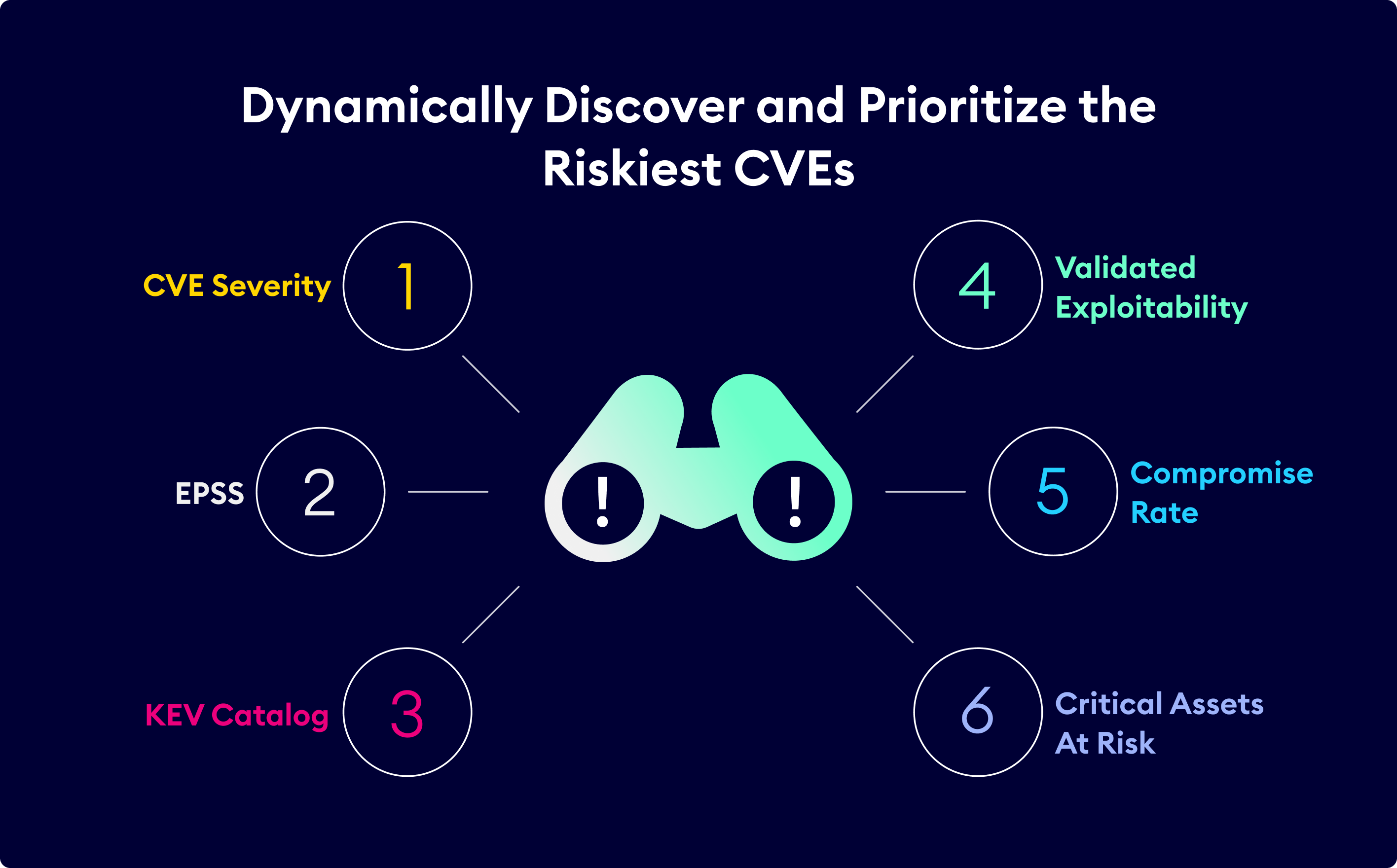
Dynamically Discover and Prioritize the Riskiest CVEs
Continuous discovery and dynamic mapping of vulnerabilities across hybrid infrastructure.
Identify the most likely breach points and quantify their intrusion risk.
Accurate validation of the exploitability of high-risk remote-code executable CVEs, with integrated attack path logic for enhanced prioritization.
Identify the most likely breach points and quantify their intrusion risk.
Accurate validation of the exploitability of high-risk remote-code executable CVEs, with integrated attack path logic for enhanced prioritization.
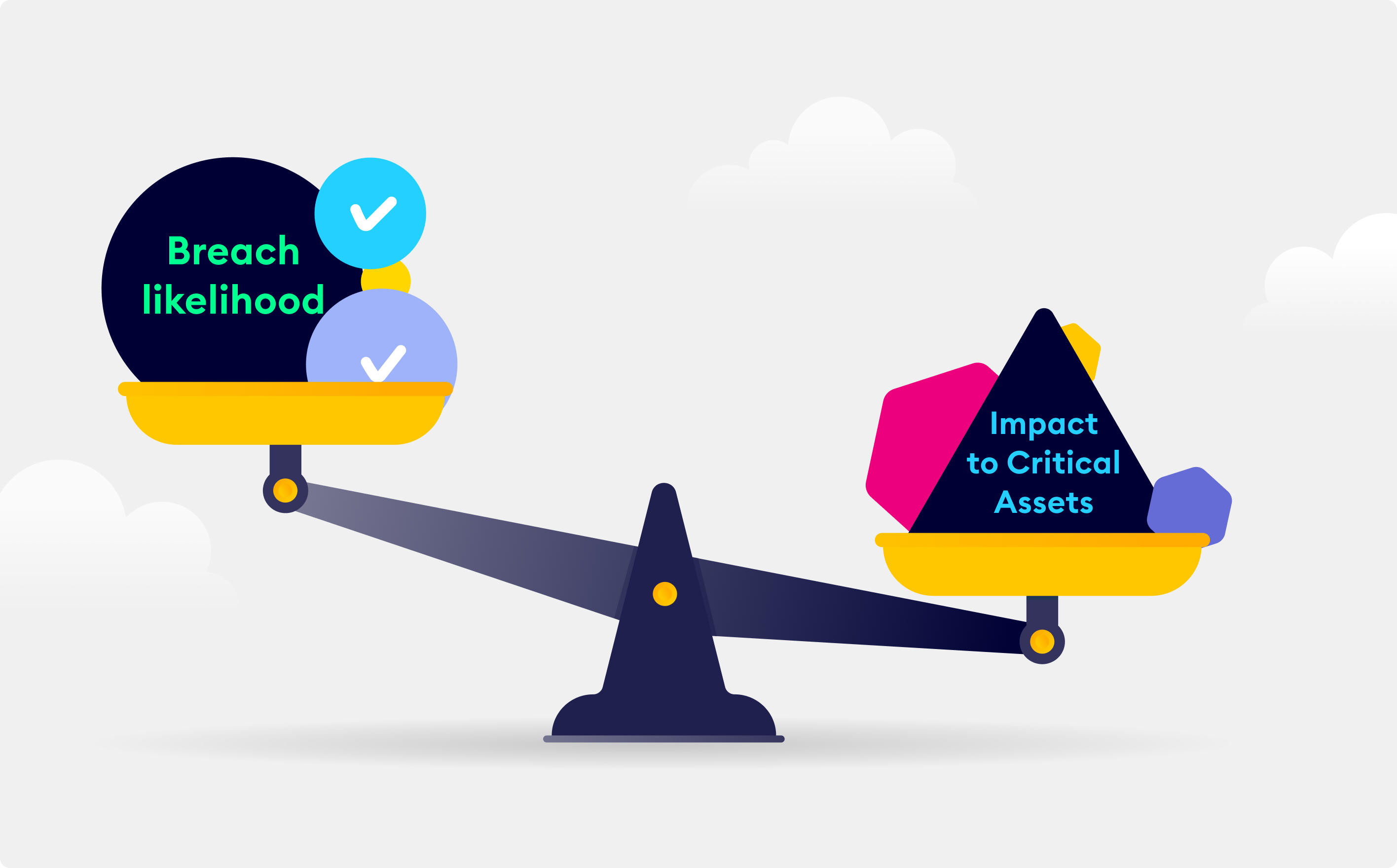
Report True Risk of Vulnerabilities
Comprehensive dashboards and reporting of CVEs by device, software or products, with holistic risk logic.
Seamlessly Pivot security context from intrusion risk to business impact risk, based on CVE exploitability.
Validate which vulnerabilities present the greatest risk to the business, and track remediation efforts to ensure the effectiveness of defensive strategies
Seamlessly Pivot security context from intrusion risk to business impact risk, based on CVE exploitability.
Validate which vulnerabilities present the greatest risk to the business, and track remediation efforts to ensure the effectiveness of defensive strategies
Accelerate the Mobilization of Vulnerability Management
Streamline Security operations through the mobilization of risk remediation and vulnerability management.
Justification, prioritization and remediation guidance to accelerate closed-loop vulnerability management.
Disrupt multiple attack paths and future-proof the security posture of your most critical assets.
Justification, prioritization and remediation guidance to accelerate closed-loop vulnerability management.
Disrupt multiple attack paths and future-proof the security posture of your most critical assets.
Comprehensive Vulnerability Prioritization for the Hybrid World
The next generation of risk-based vulnerability management is here, with dynamic and continuous CVE mapping that allows you to seamlessly pivot security context from a traditional to a transformative RBVM construct.
Prioritize your viewpoint of vulnerabilities from exploit likelihood to business impact risk and streamline the mobilization of remediation efforts, with rich contextual guidance, to justify action and proactively accelerate security operations.
Prioritize your viewpoint of vulnerabilities from exploit likelihood to business impact risk and streamline the mobilization of remediation efforts, with rich contextual guidance, to justify action and proactively accelerate security operations.