Continuous Exposure Management in the Cloud
Focus on High Impact Risks Across Multi-Cloud and Hybrid Environments
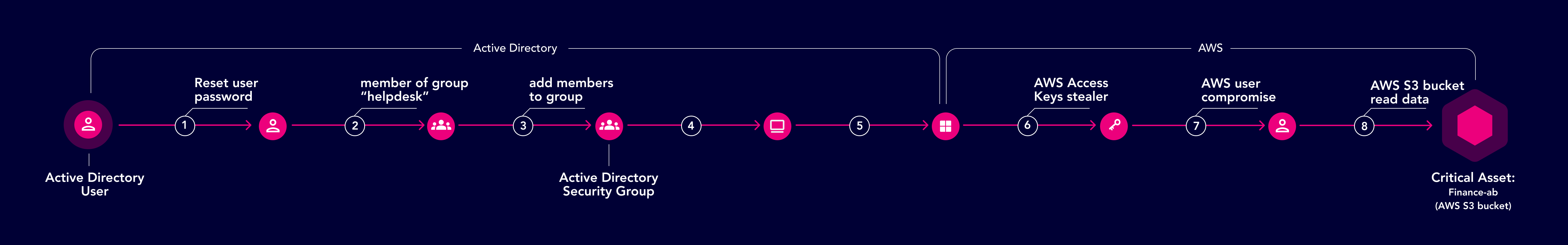
Escalating Privileges in the Cloud in 3 Simple Steps
Focus on Fixing What Matters Most in Multi-Cloud Environments
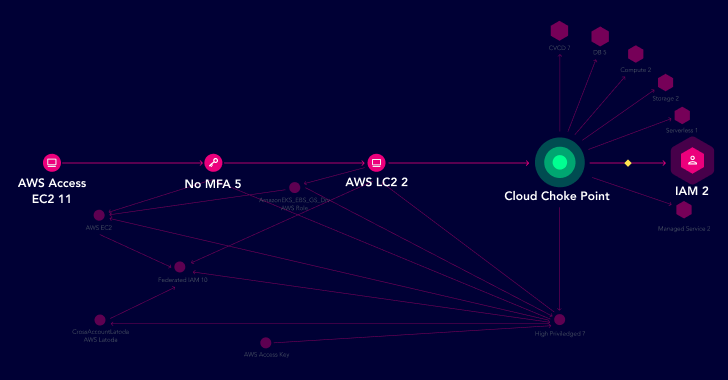
Highlight Top Choke Points in Multi-Cloud and Kubernetes
• Instantly identify potential breach points and targeted cloud resources
• Map all attack paths to focus on entities that can be compromised by multiple cloud breach points
• Identify exposed Kubernetes containers that can be easily compromised
• Map all attack paths to focus on entities that can be compromised by multiple cloud breach points
• Identify exposed Kubernetes containers that can be easily compromised
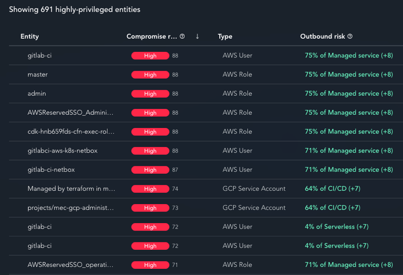
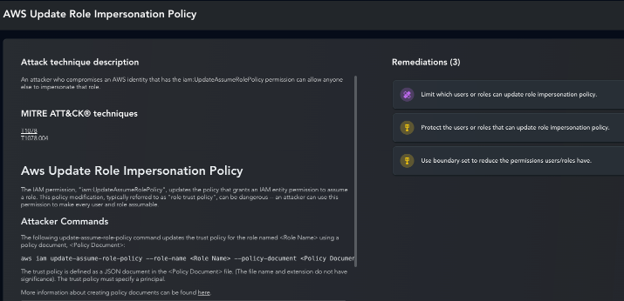
Uncover Exploitable Highly Privileged Access
• Identify top privileged roles and accounts that if compromised could lead to “Game-Over
• Highlight privileged access that can easily be compromised by attackers
• Provide actionable remediation to secure high privileged access
• Highlight privileged access that can easily be compromised by attackers
• Provide actionable remediation to secure high privileged access
Gain Remediation Efficiency
• Focus on the high impact cloud exposures and communicate justification
• Accelerate remediation by providing guidance and alternatives
• Save time on analysis and remediation of exposures that are by design
• Accelerate remediation by providing guidance and alternatives
• Save time on analysis and remediation of exposures that are by design
End-to-end Exposure Management Across the Hybrid Enterprise
Gain a holistic visibility and analysis of attack paths that span across on-prem and multi-cloud environments to fix the most critical exposures and stop attacks before they happen.