|
Getting your Trinity Audio player ready...
|
On Friday, March 29th, a Microsoft researcher disclosed that he had found malicious code embedded in XZ Utils versions 5.6.0 and 5.6.1. This vulnerability is being tracked as CVE-2024-3094 and at present has a 10 out of 10 CVSS severity warning.
XZ Utils is a format compression utility that comes with the majority of Linux distributions. XZ Utils is widely used in packages and therefore this vulnerability is especially concerning and according to security firm Red Hat, this vulnerability may “enable a malicious actor to break sshd authentication and gain unauthorized access to the entire system remotely,”
When Did This Vulnerability First Appear?
Back in February, an attacker with the GitHub account JiaT75 committed code to the XZ Utils Github repository which contained obfuscated code that was able to change the build process. While it’s still unknown how the attackers managed to place the malicious code, on March 29th, developer Andres Freund from Microsoft announced on the Open Source Security Mailing List the discovery of the malicious code:
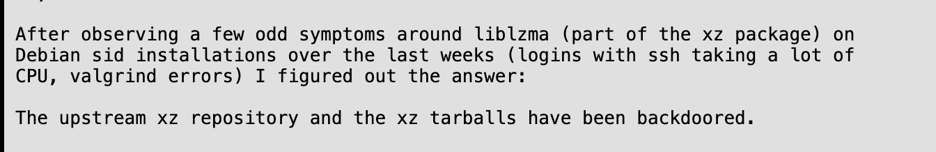
This vulnerability can allow for remote backdoor access and may be on instances of Fedora Linux 40 and 41 and Fedora Rawhide, as some users have already received system updates that would have had the malicious code. It may also be present on Kali, Debian unstable, Alpine Edge Arch Linux and openSUSE.
| OS name | Notes |
| Fedora 40 and 41 | |
| Fedora Rawhide | |
| Debian unstable | No stable versions affected |
| Alpine edge | |
| Arch Linux | |
| openSUSE | |
| Kali | Versions updated between 3.26-3.29 are impacted |
Each distribution has alerted users via email and or advisory posts and recommendations to revert systems to previous unaffected versions. Meanwhile the GitHub user has now been suspended.
Thankfully, there’s a very good chance that the infected version may not be on many users’ deployments as of yet. Said Fruend in his post, “Luckily xz 5.6.0 and 5.6.1 have not yet widely been integrated by Linux distributions, and where they have, mostly in pre-release versions.”
It doesn’t seem that other Linux distributions contain the malicious code.
As the CVSS score implies, CVE-2024-3094 can have very serious implications if left unaddressed, potentially enabling unauthorized access which could affect the integrity and security of the system. Moreover, this attack can bypass typical security measures, leading to the compromising of the system and data breaches. As most is currently no evidence that the code had been exploited in the wild as of yet but this is a rapidly developing situation and more time and information is needed to be better aware of the potential for impact.
What Does This Mean for Your Environment?
At the moment, this vulnerability is only present in pre-release versions, so there is no patch. Nonetheless, users who did update are urged to treat this as a potential security risk and revert to previous, unaffected versions.
As of now, very few users are impacted. If you suspect you may be using an impacted version, you should:
- Check if you are indeed using the impacted version of XZ. To do this, see if the output says xz (XZ UTils) 5.6.1 or liblzma 5.6.1, then either apply the update for your distribution (if and when available), downgrade xz, or disable ssh for the time being.
To be on the safe side, you can also:
- Check logs for unauthorized access
- Check for sensitive information and or keys on the affected machines
- Rotate credentials
As this is an emerging threat, we will update this advisory if and when more information becomes available.


