Announcing Enhanced EASM Capabilities for Validating End-to-End Risk
JUMPSHOT: XM Cyber Uncovers Critical Local Privilege Escalation (CVE-2025-34352) in JumpCloud Agent
CRITICAL ALERT: React2Shell CVE-2025-55182 is Under Active Exploitation!
Patching Can’t Save You: How Agentic AI Broke Vulnerability Management
How to Accelerate Zero Trust with Exposure Management
Challenge Accepted!
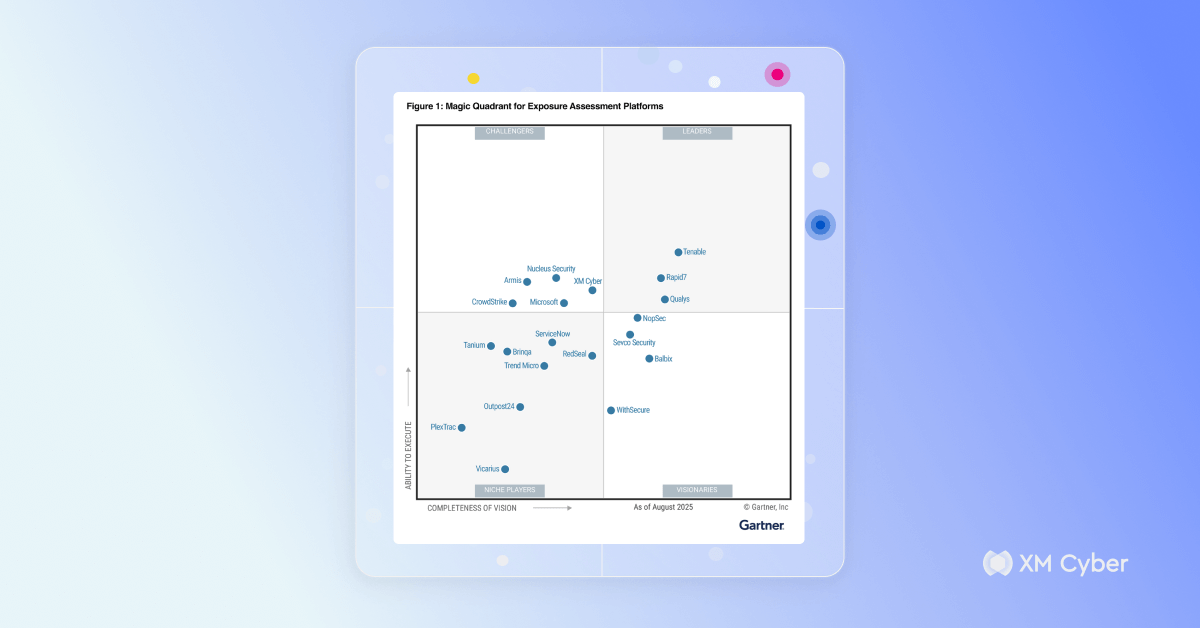
XM Cyber Named a Challenger in the 2025 Gartner® Magic Quadrant™ for Exposure Assessment Platforms
How to Build a Continuous Exposure Management Plan from Scratch
From Alerts to Action: Streamlining Remediation Operations with Continuous Exposure Management
Flipping the Script: Seeing Risk the Way Attackers Do
Windows Server Update Service (WSUS) Critical Vulnerability: CVE-2025-59287 Under Active Exploitation
Cracking the Boardroom Code: A New Path for CISOs
CRITICAL ALERT: Oracle E-Business Suite Zero-Day Vulnerability, CVE-2025-61882, Under Active Exploitation!
Request a demo