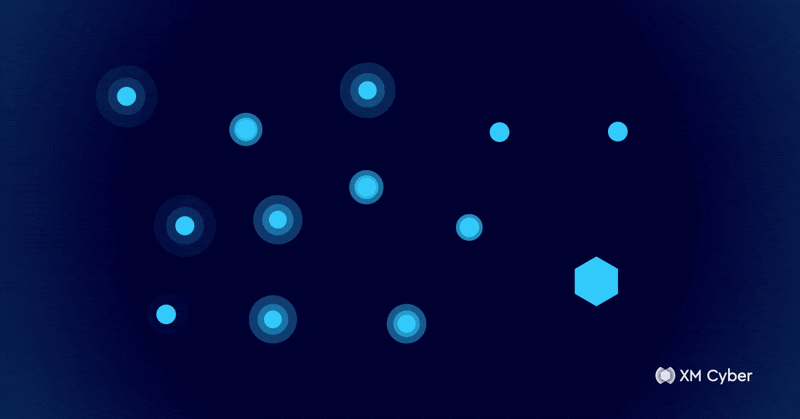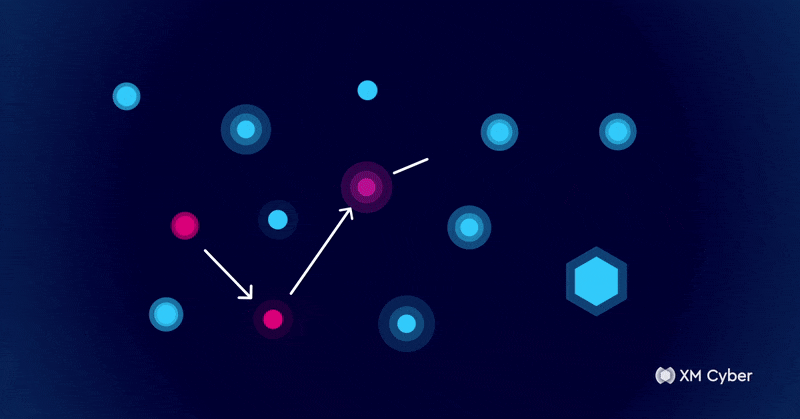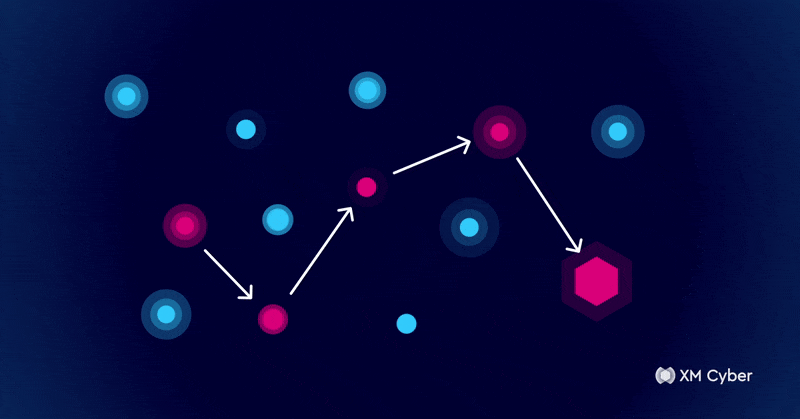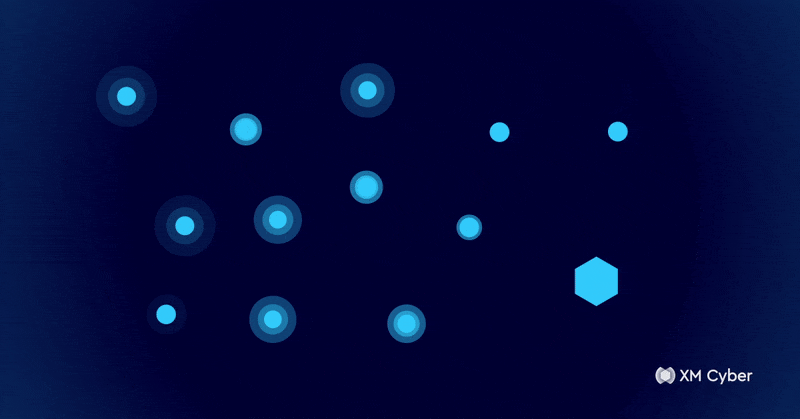
Seeing What Attackers See: How Attack Graphs Help You Stay Ahead of Cyber Threats
CVE-2025-24813: Critical Apache Tomcat Vulnerability Already Being Exploited – Patch Now!
Four Real-Life Financial Service Attacks Paths and How we Blocked Them
Exposure Management in Finance: A Proactive Approach to Cyber Resilience
The Artificial Intelligence Threat: Are You Losing Sleep Yet?
From ArgoCD To Azure Hybrid Attacks Part 2 – Leveraging Workload Identity for AKS to Move Laterally Across Tenants
From ArgoCD To Azure Hybrid Attacks Part 1 – Leveraging Kubernetes ArgoCD RBAC Permissions to Escalate Cluster Privileges
Exposure Management: Healthcare’s Preventive Medicine
From Risk to Resilience: XM Cyber’s 2024 Wrapup
OT vs. IT Cybersecurity – Differences, Similarities and Everything in Between
10 Cybersecurity Trends to Watch in 2025 and How to Prepare
How to Build a Hybrid Cloud Data Security Strategy
Request a demo