XM Cyber is Recognized as a Strong Performer in the 2025 Gartner Peer Insights™ Voice of the Customer for Vulnerability Assessment
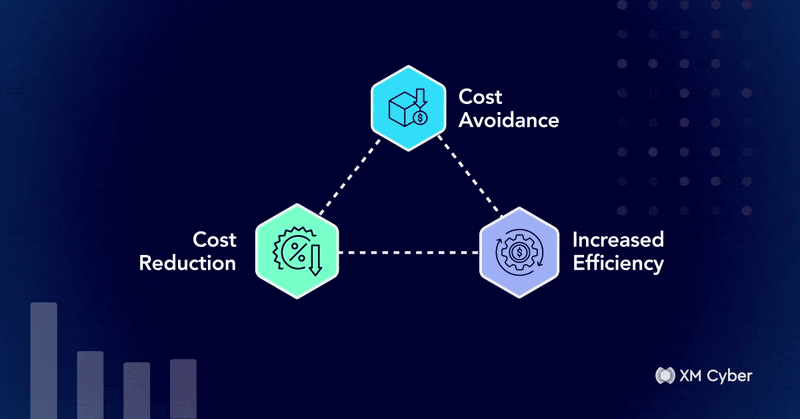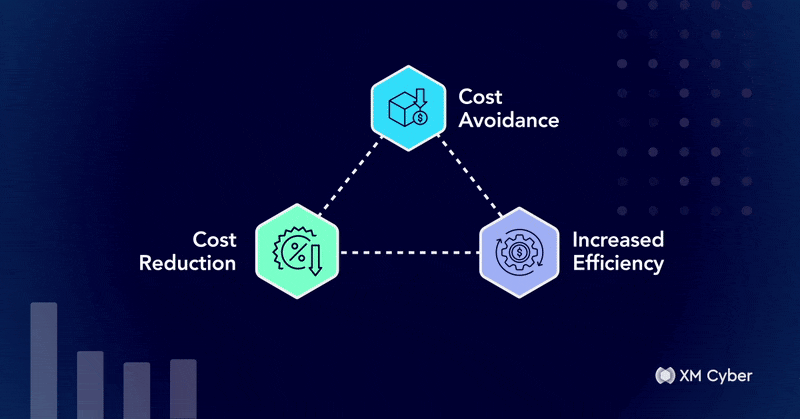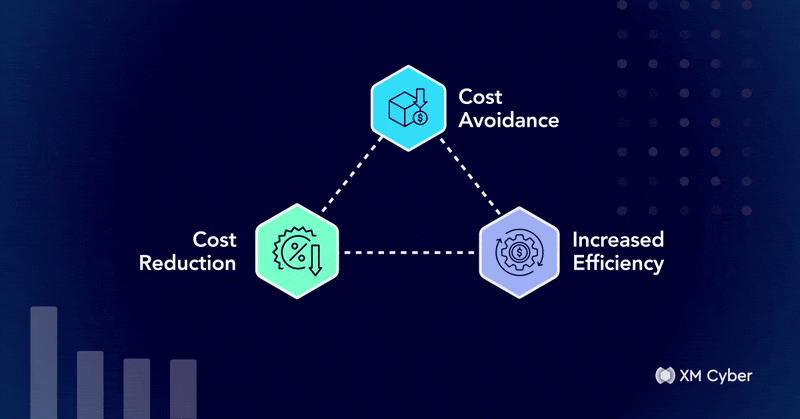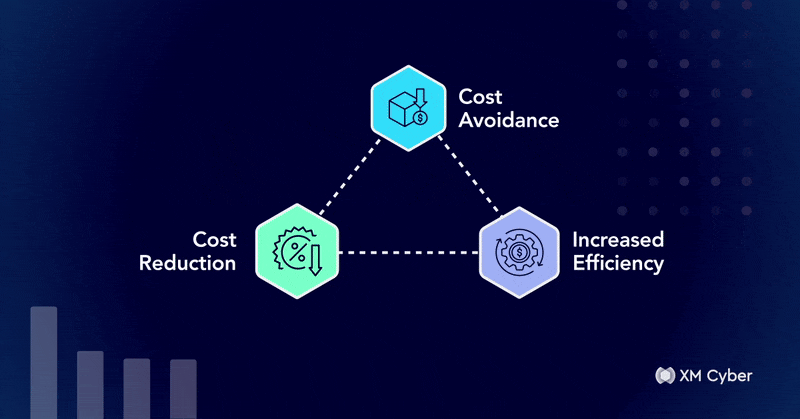
One Year Later: The Tangible ROI of Exposure Management After Year One
Urgent Alert: Microsoft SharePoint Zero-Day Vulnerability “ToolShell” Under Active Attack
The M&A Security Playbook: 11 Questions to Master Cybersecurity in Mergers and Acquisitions
Unifying Cybersecurity Posture: Why A Digital Twin Approach Outperforms Traditional Data Aggregation
How Attackers Really Move – And 5 Steps to Make Their Job Much Harder
Beyond the Checklist: Why Attackers Love Your Misconfigurations- And How to Stop Them
Exposure Management in Retail: The Security Approach That Never Goes Out of Style
Bridging Theory and Practice: How Continuous Security Controls Optimization Complements Proactive Defense and Posture Management
Forrester’s Unified Vulnerability Management (UVM) – What it Means and Why it Matters
From Blocker to Enabler: Translating Cyber Risk into Business Value
Ten Things You Need to Do Yesterday to Stay Compliant with NIS2
Request a demo