How to Accelerate Zero Trust with Exposure Management
Challenge Accepted!
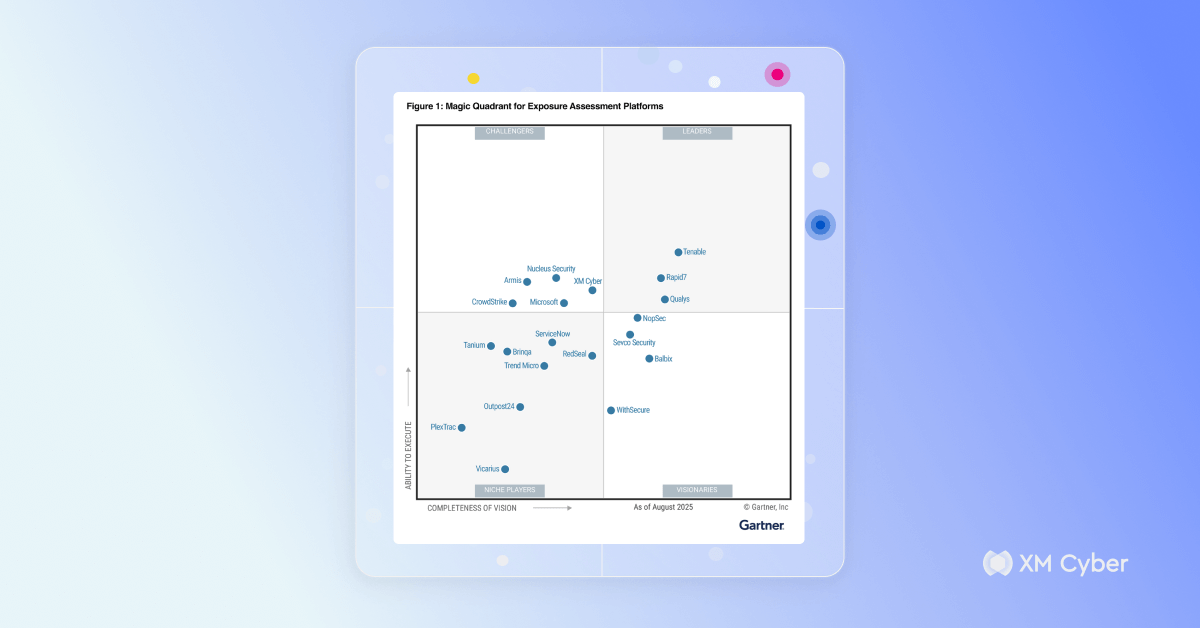
XM Cyber Named a Challenger in the 2025 Gartner® Magic Quadrant™ for Exposure Assessment Platforms
How to Build a Continuous Exposure Management Plan from Scratch
From Alerts to Action: Streamlining Remediation Operations with Continuous Exposure Management
Flipping the Script: Seeing Risk the Way Attackers Do
Windows Server Update Service (WSUS) Critical Vulnerability: CVE-2025-59287 Under Active Exploitation
Cracking the Boardroom Code: A New Path for CISOs
CRITICAL ALERT: Oracle E-Business Suite Zero-Day Vulnerability, CVE-2025-61882, Under Active Exploitation!
Can CTEM Address the Hidden Gaps in Your PAM Program?
Your Supply Chain Is an Attack Surface – Here’s How to Secure It
Shadow AI is Everywhere: XM Cyber Finds 80% of Companies Show Signs of Unapproved AI Activity
XM Cyber and Google SecOps: Turning Context into Action
Request a demo