|
Getting your Trinity Audio player ready...
|
New research from XM Cyber offers some eye-opening findings about actual risk versus perceived risk.
Cybersecurity is a bit akin to the art of hitting a moving target. Just when you think you’ve got the threat in your sights…things shift and now that threat isn’t where or what it seemed to be. That’s why the report we just released, Navigating the Paths of Risk: The State of Exposure Management in 2024 is so important. Because by analyzing data gathered from over 40 million exposures that represent high-impact risks to millions of critical business entities – you can glean some pretty incredible insights.
And you may be surprised to learn that what you thought were immediate threats…may be far less severe. Here’s a taste of what we learned (and you can get the full report here for free):
- Exposures Go Way Beyond CVEs
Organizations traditionally focus on managing software vulnerabilities tracked by CVE identifiers. However, our research found that this approach only addresses a small fraction of overall security risk. How small? Amazingly, less than 1% of exposures are Remote Code Executable CVEs. This is a massive blind spot in security programs that rely heavily on vulnerability patching.
- Cyber Hygiene – More Important than Ever
On the other side, some threats that tend to slip by under cybersecurity radars remain seriously high-impact. Cyber hygiene, for example. We found that 79% of organizations have issues with cached domain credentials or local credentials scattered across multiple machines on their network – creating a broad attack surface for malicious actors to exploit.
- AD: A Gaping Security Hole
Dramatically, our research found that identity and credential issues remain a gaping hole in organizational security posture. Active Directory, the cornerstone of organizational identity management, is a prime target. In fact, 80% of all security exposures identified stem from Active Directory misconfigurations or weaknesses. Even more concerning, one-third of all critical asset vulnerabilities can be traced back to identity and credential problems within Active Directory.

- The Cloud is Massively Exposed
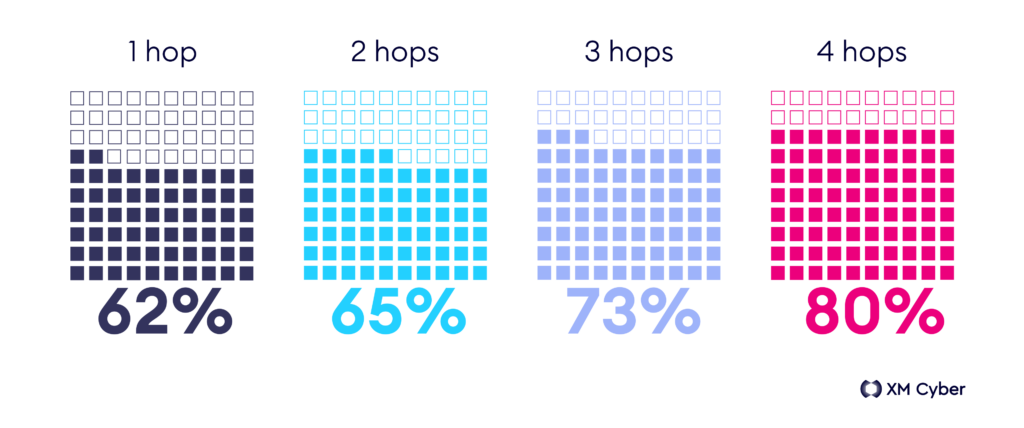
Our report proves what security stakeholders already know: cloud environments are not immune to security risks. The numbers paint a concerning picture. With over half (56%) of exposures found in the cloud, in a troubling 70% of organizations, attackers can infiltrate on-premises systems and then hop to the cloud environment. Even more alarming, once inside the cloud, they can potentially compromise a staggering 93% of critical assets in just two hops.
- The Need for a Nuanced Approach
The approach to managing security exposures needs to be tailored to the industry. For example, our study found that while financial firms typically hold 5 times more digital assets compared to the energy sector, the energy sector faces a staggering 21 times higher number of exposures that directly threaten their critical assets. Clearly, there is a need for a nuanced approach to cybersecurity – one that considers not just the volume of digital assets, but also the industry-specific vulnerabilities and potential consequences of a breach.
- The Attack Path is Key
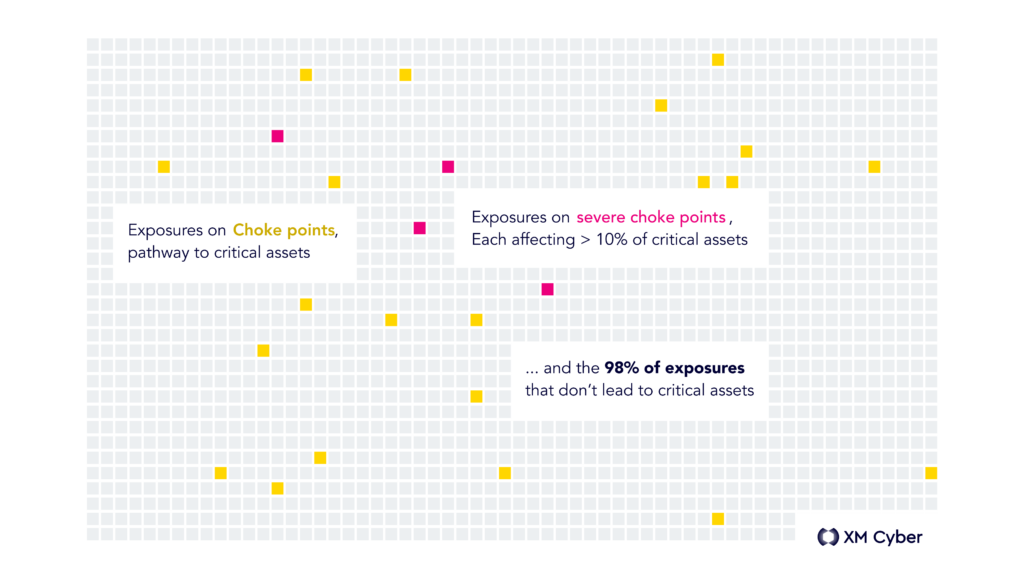
Integrating attack path modeling is crucial for prioritizing threats. We found that only 2% of exposures actually lie on critical “choke points” – the junctions where multiple attack paths converge, allowing attackers to reach critical assets. The difference in choke point exposure between organizations is dramatic: 20 times higher in those with poorer security posture.
This year’s State of Exposure Management report uncovers a fundamental disconnect between traditional cybersecurity focus and the real-world threatscape. This demands a paradigm shift in security strategies. The future of cybersecurity lies not just in chasing the next CVE, but in proactively addressing the often-overlooked vulnerabilities that expose our most critical assets.
The State of Exposure Management report’s findings are based on data from the XM Cyber Continuous Exposure Management Platform that was analyzed independently by the Cyentia Institute. Download your free copy of the report here.


