Focus on fixing your most critical exposures. With XM Cyber, you can identify all vulnerabilities, misconfigurations, and credential issues to see how they chain into attack paths across your hybrid environment.
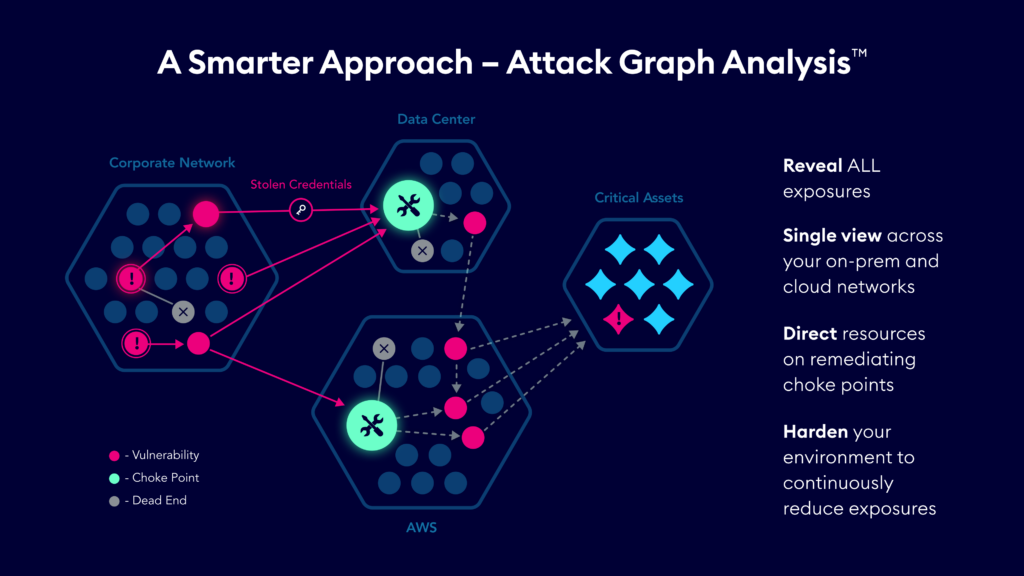
Context is everything when it comes to reducing risk, and not all exposures impact your security posture in the same way. XM Cyber helps you move from endless, siloed lists in need of remediation to an attack graph that pinpoints the exact exposures that are most critical to protect your on-prem and cloud environments.
With XM Cyber as part of your Continuous Threat and Exposure Management (CTEM) program, you can mobilize teams to block attackers at Choke Points for accurate and cost-effective remediation that rapidly improves security posture.
75% of security exposures aren’t on attack paths to critical assets, yet teams still waste time fixing them.
- Choke Point and Dead End Identification
Map out all attack paths and identify exposures that don’t help attackers move towards critical assets – the Dead Ends that can be ignored. Also identify exposures that when remediated block many attack paths – the Choke Points that enable optimized risk reduction.
- Context-based Remediation Guidance
With XM Cyber, you get context-based guidance on all the different remediation options available, to accelerate the remediation process and improve process consistency.
- Security Posture Scoring & Trends
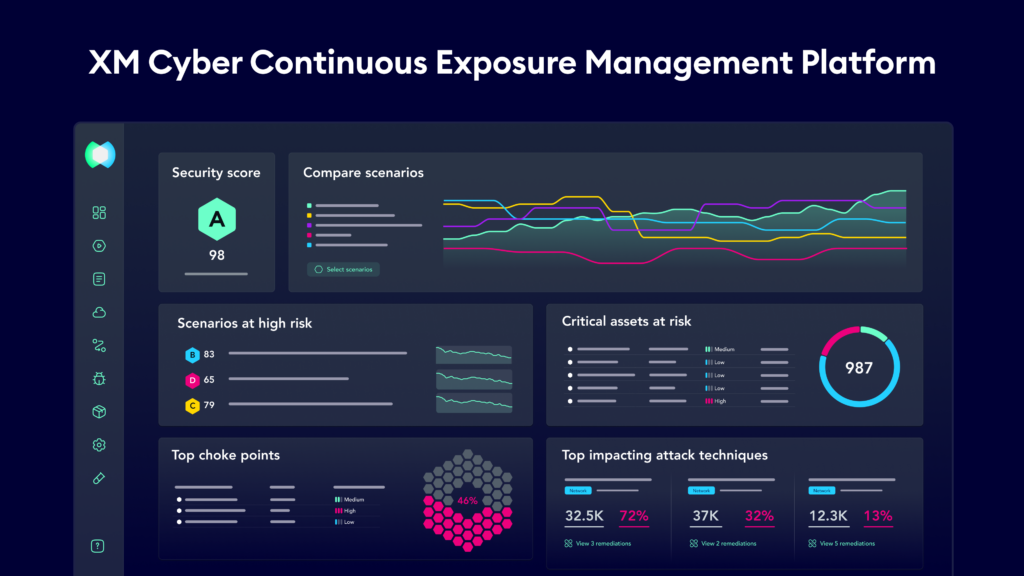
Demonstrating improvement in your security posture over time is essential. XM Cyber helps you share continuously updated metrics of security posture and trending that shows the impact of remediation efforts.
- Management of CVEs, Misconfigs, & Identity Issues
XM Cyber helps you discover, prioritize, remediate, and validate all exposure types with a single view, providing a holistic contextual view into risk.
- Active Directory & Identity Security
Attackers leverage identities in attacks, and the complexity and pervasive nature of Active Directory makes it a prime target. XM Cyber zeros-in on identity issues and cached credentials.
- Hybrid Cloud Posture Management
With a holistic, attacker-oriented perspective, XM Cyber grants insights you need, regardless of the environment – cloud, on-prem or hybrid.