|
Getting your Trinity Audio player ready...
|
As cyber threats evolve, security leaders must protect legacy and operational technology (OT) systems, in addition to the traditional IT infrastructure. Industries such as manufacturing, energy, and healthcare rely heavily on these systems for daily operations, but their outdated architecture and limited security measures make them vulnerable to attacks that can put enterprise and people at risk. In fact, according to the SANS “State of ICS/OT Cybersecurity 2024,” the number one initial attack vector into OT/IT network(s) is compromised IT assets, with nearly 50% citing this path.
Replacing or updating these systems is disruptive and costly – and to this end, Gartner even created a specific Market Guide to help – Market Guide for Mainframe and Legacy Systems Migration and Modernization Tools. It’s clear that organizations need a way to strengthen defenses and incorporate modern IT cybersecurity approaches into their legacy and OT systems.
CTEM for OT and Legacy Systems
XM Cyber is now extending its Continuous Threat Exposure Management platform (CTEM) to protect legacy and OT systems. This new approach offers a non-intrusive, proactive way to identify and mitigate attack paths that expose these crucial systems to threats.
The Cybersecurity Challenge of Legacy and OT Systems
Legacy and OT systems play a vital role in keeping critical industries running, but their age and limited security support leave them at risk. Cyber attackers target these assets, knowing they’re harder to protect and can provide valuable entry points into larger IT environments. Additionally, attacks on OT systems can result in physical damage to plants and machinery or put people at risk. Since replacing these systems is both costly and disruptive, organizations struggle to adapt current security approaches to these systems.
XM Cyber augments your existing legacy and OT security without impacting uptime or system availability. By aligning security, IT, and OT teams,critical assets are protected without interrupting business operations.
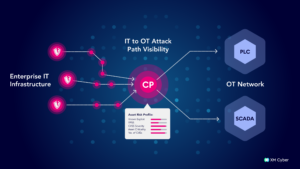
How XM Cyber Extends Attack Path Analysis to Legacy and OT Systems
XM Cyber’s Continuous Exposure Management platform maps attack paths across hybrid environments, providing visibility into how attackers might exploit weaknesses both on-prem and in the cloud, to reach critical legacy and OT systems.
The platform’s XM Attack Graph Analysis™ highlights:
- Validated vulnerabilities that, if left unaddressed, could lead to these high-value systems.
- Attack paths through IT environments that could expose OT and legacy assets.
- Choke points, which are key exposures in the hybrid environment that, when resolved, break multiple attack paths simultaneously, for maximum impact.
By prioritizing vulnerabilities based on risk, XM Cyber enables teams to focus on the most impactful attack paths and efficiently allocate resources to address them. The XM Cyber Digital Twin approach supports operational continuity by securing OT systems without requiring invasive scans that can knock systems offline.
Key Benefits of XM Cyber’s Solution for Legacy and OT Systems
- Proactive Risk Mitigation: By identifying exposures before attackers can leverage them, XM Cyber enables organizations to stay ahead of threats.
- Operational Continuity: This non-intrusive approach complements your existing OT security tools, ensuring that OT systems remain operational while security is enhanced.
- Efficient Resource Allocation: With prioritized exposure insights, security teams can address the highest-risk issues, ensuring efforts are focused where they will have the most impact on reducing risk.
- Comprehensive Coverage: XM Cyber provides a full view of attack paths across on-premises, cloud, and hybrid environments, ensuring complete protection for legacy and OT systems.
The XM Cyber Advantage
With XM Cyber’s new capability, organizations can secure legacy and OT systems against threats originating in the IT infrastructure, ensuring resilience and reliability throughout the enterprise. If your organization relies on legacy or OT infrastructure, XM Cyber delivers a modern approach to cybersecurity.
Want to see how we can integrate OT and legacy system security into your business? Book a meeting with us now.
Not ready to talk yet? Read our eBook, “Breaking Attack Paths to Legacy and OT Systems” for stories about identifying and breaking the paths to business critical IT, OT, and legacy systems.