|
Getting your Trinity Audio player ready...
|
Applying Exposure Management to Secure Legacy Systems
Legacy systems like AIX or COBOL are essential for daily operations in industries like finance and insurance, but their outdated architecture and lack of built-in security make them highly vulnerable to cyberattacks. XM Cyber’s Continuous Exposure Management platform provides a proactive approach to safeguarding these critical assets, integrating them seamlessly into your enterprise cybersecurity strategy. Security teams can identify the exposures and attack paths that lead to these vulnerable systems, allowing organizations to mitigate risks before they are exploited.
How XM Cyber Protects Legacy and OT Systems:
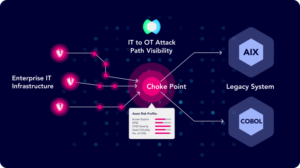
XM Cyber’s Continuous Exposure Management (CEM) platform leverages Attack Graph Analysis™ to provide end-to-end visibility into the threats targeting an organization’s most critical assets including legacy systems. Here’s how it works:
- Comprehensive Attack Mapping: Map out attack paths, showing how vulnerabilities in the IT network can lead to these high-value targets.
- Prioritized Risk Management: Identify and validate exposures that attackers could exploit to reach critical legacy systems.
- Modernize Legacy Cybersecurity: Break the attack path before it reaches the vulnerable systems that lack current defenses or the latest patches.
- Choke Point Identification: XM Attack Graph Analysis™ prioritizes choke points or exposures that, when fixed, can break multiple attack paths.
Benefits of XM Cyber’s Solution:
- Proactive Defense: Organizations stay ahead of threats by providing real-time, actionable insights into potential attack paths targeting legacy systems.
- Efficient Resource Allocation: By focusing on critical exposures and choke points, security teams can concentrate their efforts where they are most needed, optimizing both time and resources.
- Operational Continuity: Ensures that modern and legacy systems are protected without the risk of disrupting essential operations.
XM Cyber delivers the insights security and IT teams need to safeguard their legacy systems without costly replacements or operational disruptions. By visualizing, validating, prioritizing, and remediating attack paths, your legacy assets are fully integrated into a current cybersecurity strategy, supporting operational resilience and regulatory compliance.