|
Getting your Trinity Audio player ready...
|
What Are Active Directory Security Best Practices?
Since 1999, Active Directory has been the default identity and access management service in Windows networks. Active Directory is the software responsible for authenticating and authorizing users and computers across both cloud-based and on-prem apps. Basically, it assigns and enforces security policies for all network endpoints.
Active Directory is highly central to the functioning of on-prem, cloud-based and hybrid ecosystems. It is critical for productivity – arguably a key to business continuity itself. And that’s why it’s important for security stakeholders to understand the best practices associated with Active Directory.
What Are Some Common Threats to Active Directory Security?
While Active Directory’s longevity has instilled trust and familiarity, it has also attracted the attention of malicious actors. These attackers are constantly on the prowl, seeking to exploit vulnerabilities and gain unauthorized access to sensitive data.
Think of AD as a fortified castle. Its walls are built with complex protocols and encryption, but like any castle, it has its weak points. Attackers, like cunning siege engineers, employ diverse tactics to breach these defenses. There are numerous threats facing Active Directory, including:
- System Vulnerabilities – These are flaws inherent in AD’s architecture or protocols. Think of them as cracks in the castle walls. Some common examples include:
- Kerberos Authentication – Despite its strengths, Kerberos has vulnerabilities like Pass-the-Hash, Pass-the-Ticket, Golden Ticket, and Silver Ticket attacks, allowing attackers to forge authentication credentials and gain unauthorized access.
- NTLM Encryption – A legacy protocol lurking within AD’s depths, NTLM offers weak encryption that attackers can exploit.
- Brute Force Attacks – These relentless assaults attempt to crack passwords by systematically trying every possible combination.
- Insider Threats – These exploit human error or malicious intent to gain access. Common examples include:
- Phishing and Social Engineering – Deceptive tactics like fake emails or phone calls can trick users into revealing their credentials, handing the keys to the attackers.
- Spear-Phishing – Personalized attacks targeting specific individuals with tailored messages are even more effective.
- Excessive Permissions – Granting users more access than necessary creates opportunities for misuse, intentional or accidental.
Top 20 Active Directory Security Best Practices
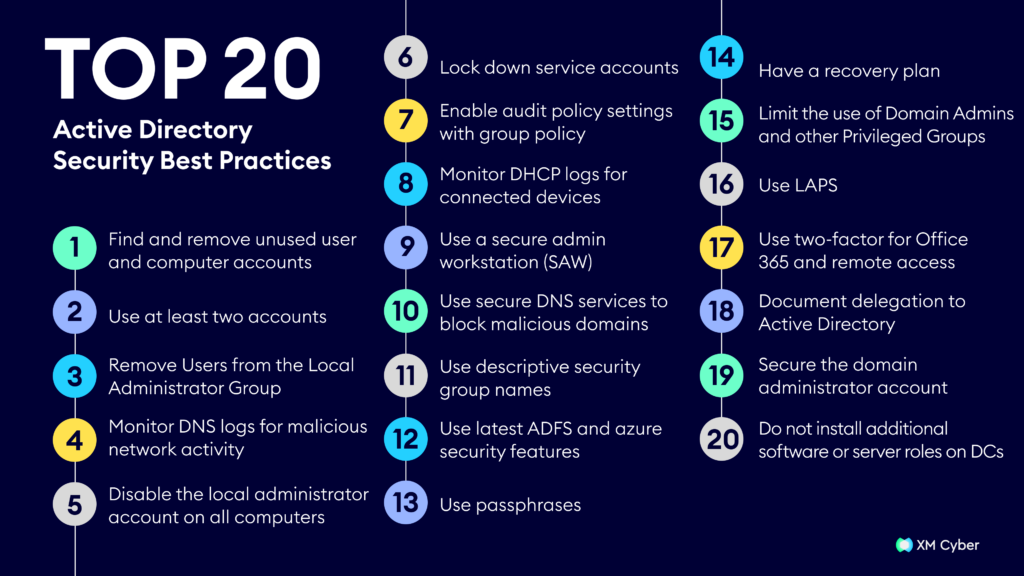
Active Directory policy best practices are crucial for optimal system functioning. They enhance security, prevent data loss, and ensure efficient operations. Following is a comprehensive list of Active Directory security best practices:
- Find and remove unused user and computer accounts
Implement a procedure to identify and manage inactive users and computer accounts in Active Directory. Unused accounts pose security risks and impact system functionality. The CIS Critical Security Controls advise prompt deletion or disabling of dormant accounts in order to mitigate potential threats from weak passwords and unauthorized access.
- Use at least two accounts
To enhance security, avoid daily logins with accounts having local admin or Domain Admin privileges. Adopt a dual-account system: a standard account for routine tasks and a privileged account exclusively for administrative duties. Implement the least privileged administrative model, limiting user permissions. Discourage placing secondary accounts permanently in Domain Admins group – include temporarily only when necessary. Microsoft advises against long-term Domain Admin rights due to security risks.
- Remove Users from the Local Administrator Group
Avoid having regular users in the local administrator group on computers to mitigate potential security threats. Users with local admin rights can compromise the entire operating system, leading to security issues like malware installation and data theft. Microsoft’s vulnerabilities report suggests that removing admin rights could have mitigated 85% of critical vulnerabilities discovered in 2018. Control the local administrator group through group policy to prevent unauthorized additions.
- Monitor DNS logs for malicious network activity
Ensure all domain-joined systems use the local Windows DNS server to log both internal and external DNS queries. This allows tracking of every DNS lookup, helping identify connections to potentially malicious sites. Enable DNS debug logs on Windows Servers by accessing the DNS Management Console, selecting properties, navigating to the Debug Logging Tab, and checking “Log packets for debugging.” Analyzing these logs aids in swiftly detecting and addressing suspicious activities.
- Disable the local administrator account on all computers
The local administrator account in Domain environments is unnecessary and poses security risks due to its well-known nature and common password configurations across computers. Attackers exploiting one system could gain local admin rights on all domain-joined computers, escalating privileges and potentially accessing domain admin credentials. Admin tasks should be performed with individual accounts. If you can’t disable the local admin account, securing it with recommended restrictions is advised.
- Lock down service accounts
Service accounts, which are used for executing tasks or services, are often set with passwords that never expire, leading to security risks. These accounts may accumulate excessive permissions and are sometimes even added to the domain admins group. It’s crucial to secure service accounts by using Managed Service Accounts, employing strong passwords, limiting access, avoiding local administrator rights, and refusing domain admin inclusion.
- Enable audit policy settings with group policy
Configure essential Audit Policy settings in group policy for all computers and servers, covering various categories like Account Logon, Account Management, Detailed Tracking, Logon/Logoff, Object Access, Policy Change, Privilege Use, and System. Ensure specific events within each category are set to ‘Success’ or ‘Success and Failure’ for comprehensive monitoring. This helps detect potential malicious activities, particularly on workstations where attacks may originate.
- Monitor DHCP logs for connected devices
Managing network connections across multiple locations with numerous users and devices can be challenging. While costly, implementing methods to allow only authorized devices is effective. Alternatively, monitor DHCP logs for connected devices, leveraging existing resources. Ensure end user devices use DHCP, and establish a naming convention for easy identification of authorized and potentially unauthorized devices.
- Use a secure admin workstation (SAW)
A Secure Admin Workstation (SAW) is a dedicated system solely for administrative tasks using a privileged account, enhancing security by minimizing vulnerabilities. It should avoid internet access and tasks like checking email. SAW is crucial for tasks like Active Directory security reports administration, Group Policy, and server management, providing protection against internal and external threats. Implement a clean OS, security baselines, full disk encryption, USB port restrictions, firewall, and two-factor authentication for heightened security.
- Use secure DNS services to block malicious domains
Prevent malicious traffic by blocking harmful DNS lookups. Services like Quad9, OpenDNS, and Comodo Secure DNS check DNS queries against threat lists, blocking access to flagged malicious domains. This proactive approach stops potential threats before they enter the network, enhancing overall security. Many Intrusion Prevention Systems also support this feature.
- Use descriptive security group names
Ensure efficient resource management by applying permissions through security groups rather than individual accounts. Avoid generic names for security groups, as they lead to loss of control over security and make tracking usage challenging. Use descriptive group names to enhance clarity and prevent inadvertent granting of permissions.
- Use latest ADFS and azure security features
Leverage ADFS, Azure, and Office 365 security features to enhance protection against password spraying, account compromise, and phishing. While premium subscriptions offer the best features, Microsoft continuously updates security measures across all levels. Notable features include Smart Lockout, IP Lockout, Attack Simulations, MFA Authentication, Banned Passwords, Azure AD Connect Health, and Custom Bad Passwords.
- Use passphrases
Using passwords is increasingly clumsy as a minimum of 12 characters is now imperative for security. Passphrases, comprised of random words, are more resilient against hacking attempts than complex passwords. Discourage predictable patterns seen in passwords like “S@mmer2018” and advocate for truly random passphrases, like “Bucketguitartire22,” to thwart cracking attempts effectively. Align with NIST guidelines and update organizational policies accordingly.
- Have a recovery plan
Craft a robust incident response plan to counter network compromises or ransomware. Prioritize staff training, establish system state backups for Active Directory security vulnerabilities mitigation, and define clear communication procedures. Recognize the need for a well-structured response plan to mitigate the impact of compromise and promptly restore services. Refer to resources like NIST’s incident handling guide for guidance.
- Limit the use of Domain Admins and other Privileged Groups
Avoid day-to-day user accounts in Domain Admins groups, which wield extensive domain-wide access. Only the default Domain Administrator account should be a constant member. Microsoft suggests temporarily placing accounts in Domain Admins, Enterprise Admins, Backup Admins, or Schema Admins when needed, removing them once tasks are complete. This prevents attackers, especially through methods like pass the hash, from exploiting compromised credentials and escalating privileges within a network.
- Use LAPS
Local Administrator Password Solution (LAPS) is a Microsoft tool for managing local admin passwords on domain-joined computers. LAPS sets unique passwords for each local admin account, which are stored in Active Directory for easy access. Deployed through group policy, it mitigates the risk of a compromised local admin account across all systems without requiring additional servers.
- Use two-factor for Office 365 and remote access
Compromised accounts pose a significant threat, offering attackers remote access via VPN, Citrix, or other systems. Check logs for unexpected login attempts, especially from regions like China and Russia. Implementing two-factor authentication is a robust defense, thwarting compromised credentials and password spraying attacks. Utilize Office 365’s built-in MFA or consider popular solutions like DUO and RSA for enhanced security.
- Document delegation to Active Directory
Effectively control access to Active Directory and associated resources by using Security Groups. Delegating rights to individuals can result in loss of control, so create custom groups with specific names, document rights holders, and establish a controlled process for adding new users. Maintain oversight to prevent unchecked additions to custom groups, ensuring permissions remain well-managed and documented.
- Secure the domain administrator account
The built-in Administrator account, inherent in every domain, should solely be used for initial setup and disaster recovery. Individual accounts are recommended for daily administrative access. Secure the Administrator account by implementing Microsoft’s recommendations through group policy and implement measures like requiring smart card logon and denying various types of access to enhance security.
- Do not install additional software or server roles on DCs
To enhance security, domain controllers (DCs) should have minimal software and roles installed. Windows Server Core is recommended for DCs, running without a GUI to reduce the attack surface. This is also suitable for roles like DHCP, DNS, print servers, and file servers, requiring fewer security patches. Note that compatibility issues with certain third-party software may arise.
The Bottom Line
Following best practices is crucial for Active Directory security – helping mitigate potential threats, safeguard against unauthorized access, and ensure efficient operations. By implementing these practices, organizations enhance their defense against evolving cyber threats, protect sensitive data, and maintain the integrity and reliability of their network infrastructure.


