What is Cyber Risk Score?
Having a strong security posture is a core objective for modern organizations. Yet measuring the strength of these postures is…
Glossary
What is Hybrid Cloud Security?
Hybrid cloud security aims to protect applications, data, infrastructure and other elements across an IT infrastructure that includes multiple environments,…
Glossary
What is Cloud Security Posture Management?
Cloud Security Posture Management is defined by Gartner as “a continuous process of cloud security improvement and adaptation to reduce…
Glossary
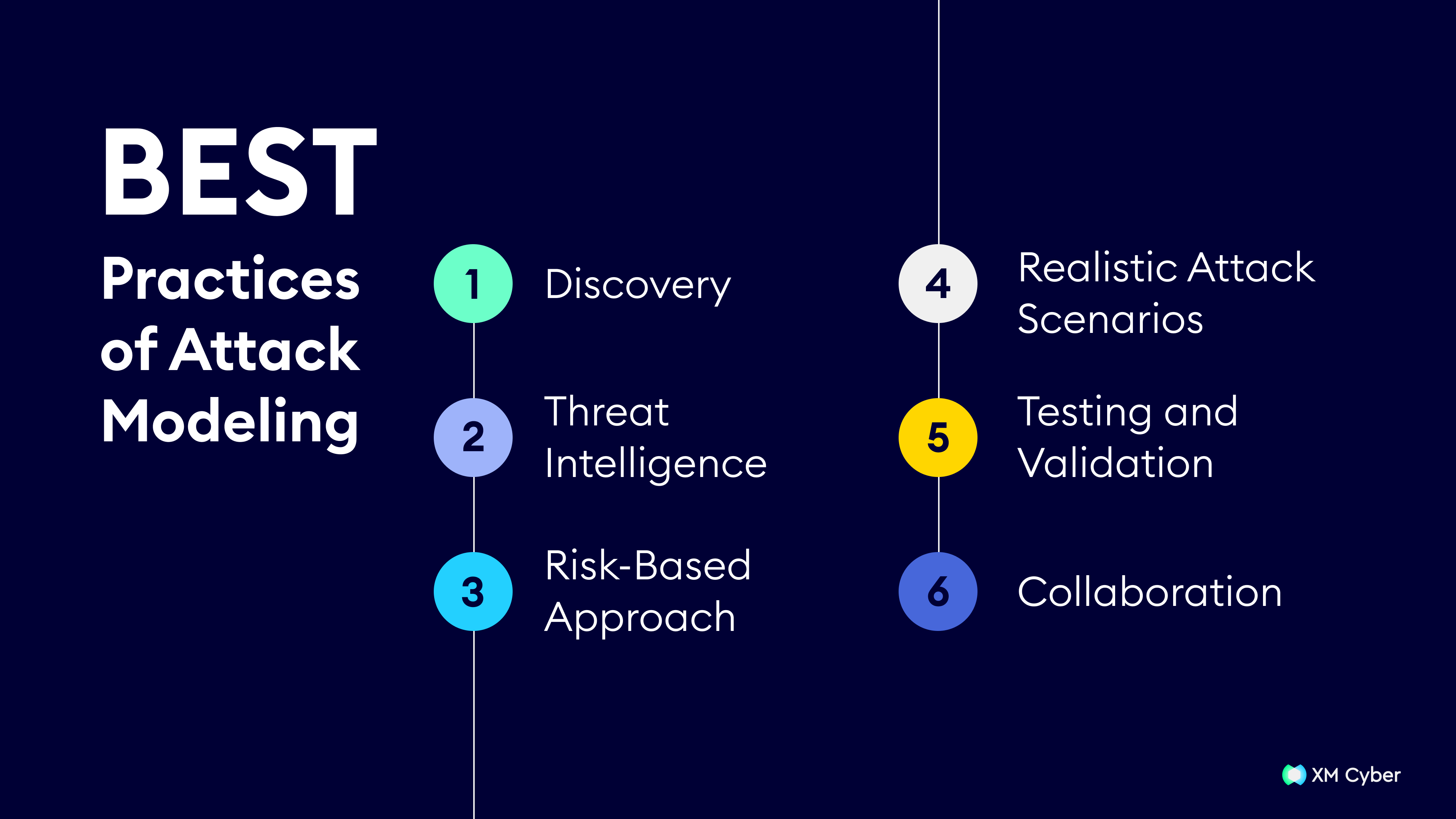
What is Cyber Attack Modeling?
Cyber attack modeling is an approximation of adversarial threats against a computer system. Cyber attack models are created to…
Glossary
What is MITRE ATT&CK Framework?
Created by MITRE Cyber Security in 2013, the MITRE ATT&CK Framework is a detailed knowledge base that documents the tactics…
Glossary
What is a Penetration Test?
Penetration testing is a technique used to identify security vulnerabilities within a system, network or application that could be exploited…
Glossary
What is a Security Control Validation?
Most of today’s enterprises layer dozens of security tools together to maintain a robust security posture. Yet “more is better”…
Glossary
What is Vulnerability Management?
Organizations rely on a process called “vulnerability management” to help identify, analyze, treat and report on security vulnerabilities within their…
Glossary
What are Breach and Attack Simulations?
These exercises are led by seasoned security professionals and staged under controlled environments. Ultimately, both sides work together to provide…
Glossary
What is a Red Team?
Red teams are “ethical hackers” who help test an organization’s defenses by identifying vulnerabilities and launching attacks in a controlled…
Glossary
What is a Blue Team?
During cyber security testing engagements, blue teams evaluate organizational security environments and defend these environments from red teams. These red…
Glossary
What is a Purple Team?
In the context of cybersecurity testing, red teams play the role of attackers, and blue teams act as defenders.…
Glossary
Request a demo