XM Cyber and STIHL
Securing a Global Legacy Through Digital Sovereignty
STIHL, a global producer of power tools for forestry and agriculture as well as for gardening and landscaping, uses XM Cyber, running on STACKIT’s…
XM Cyber and VfB Stuttgart
Building a Secure Digital Future Together
VfB Stuttgart is one of Germany’s leading football clubs – a brand with a deep sense of tradition. Under CEO Alexander Wehrle, the club…
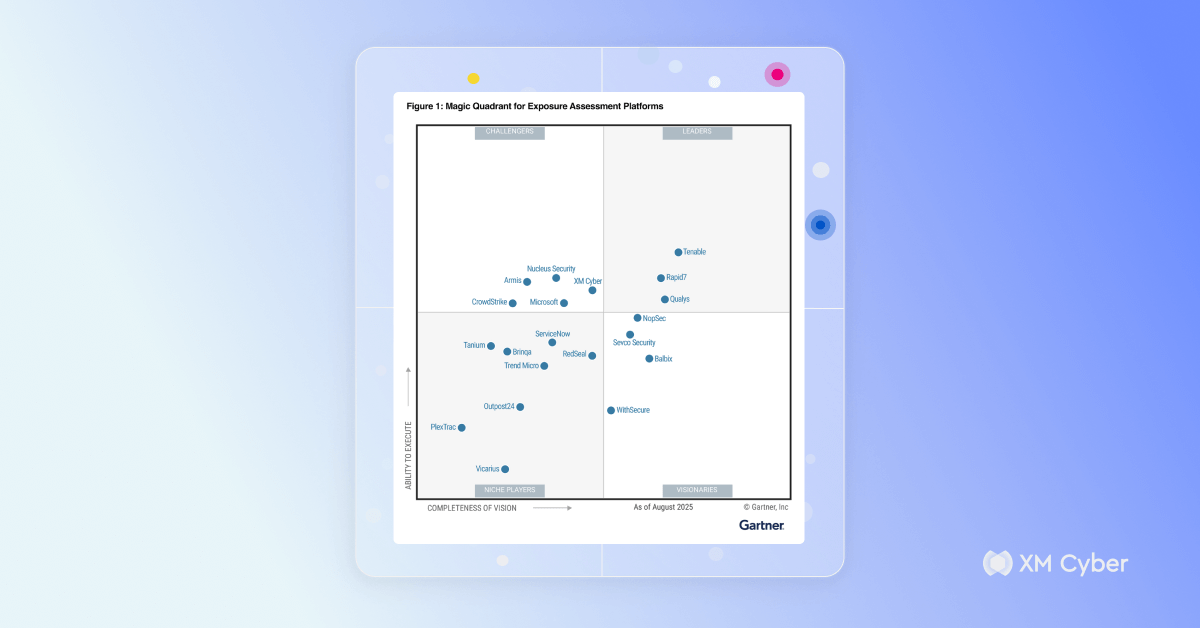
XM Cyber Named a Challenger in 2025 Gartner® Magic Quadrant™ for Exposure Assessment Platforms
We’re proud to be named a Challenger in the first-ever Gartner Magic Quadrant for Exposure Assessment Platforms. We believe our enterprise-grade, integrated Continuous Exposure…
Challenge Accepted!
XM Cyber Named a Challenger in the 2025 Gartner® Magic Quadrant™ for Exposure Assessment Platforms
The word is out! We are thrilled to announce that XM Cyber has been named a Challenger in the 2025 Gartner® Magic Quadrant™ for…
XM Cyber Helps Clal Insurance Gain Visibility and Save Time in Security Operations
Clal Insurance is one of Israel’s largest insurance companies, managing a broad digital footprint across dozens of sites. For David, the Operational Security Lead,…
How to Build a Continuous Exposure Management Plan from Scratch
Most security leaders I’ve worked with completely get the theory of exposure management. The challenge lies in turning that theory into practice. Many EM…
XM Cyber Helps an Italian Public Sector Organization Quantify Risk and Strengthen Security Posture
Securing a large Italian Public Sector Organization is a challenging task. “Our main challenges were visibility gaps in attack paths and difficulty prioritizing weaknesses…
Case Study: Jerome Monot, IT Security Manager for Rothschild & Co.
Hear from Jérôme Monot, IT Security Manager at Rothschild & Co, as he shares why their team chose the XM Cyber platform. He explains…
From Alerts to Action: Streamlining Remediation Operations with Continuous Exposure Management
Security teams face an unprecedented challenge; Attackers are moving faster than ever before, and the proliferation of openly-available AI-powered attack tools have democratized advanced…
What are Exposure Assessment Platforms?
What are Exposure Assessment Platforms (EAP)? Exposure Assessment Platforms (EAPs) are a new, consolidated category of security solutions coined by Gartner that serve as…
Flipping the Script: Seeing Risk the Way Attackers Do
As someone coming from an application security background, stepping into the world of Exposure Management has been both exciting and a bit overwhelming. Since…
Windows Server Update Service (WSUS) Critical Vulnerability: CVE-2025-59287 Under Active Exploitation
Overview Microsoft has disclosed a critical remote code execution (RCE) vulnerability in Windows Server Update Service (WSUS), tracked as CVE-2025-59287. Initial warnings indicated a…