From Risk to Resilience: XM Cyber’s 2024 Wrapup
As we step into 2025, now is a great time to reflect on the significant strides we made in the previous year. 2024 was…
Outsmarting Cyber Threats with Attack Graphs
Join us for this insightful webinar to learn all about attack graphs and how to apply them to outsmart security threats efficiently.
OT vs. IT Cybersecurity – Differences, Similarities and Everything in Between
As organizations become more globally interconnected and digitally reliant, cybersecurity threats expand beyond the IT infrastructure. Operational Technology (OT) systems are increasingly targets of…
10 Cybersecurity Trends to Watch in 2025 and How to Prepare
Introduction 2025 is finally here! And while not too many things in life are all that predictable, one thing that can be assumed with…
Understanding the NIS 2 Directive with XM Cyber
Are you trying to understand what the new NIS 2 Directive means for your organization? The EU’s new NIS 2 will help organizations strengthen…
How to Build a Hybrid Cloud Data Security Strategy
Today, the hybrid cloud model is the most common cloud mode used across organizations. The reason for this is pretty straightforward – it gets…
The 5 Stages of CTEM – Your Guide to Making Them a Reality
Wondering how to make CTEM a reality in your organization in 2025? The Continuous Threat Exposure Management framework has proven itself a gamechanger for…
Closing the Gaps: NIST NVD’s 2024 Efforts to Address the CVSS Backlog
Over the past year, the American National Institute of Standards and Technology (NIST) has undertaken significant initiatives to address the growing backlog of Common…
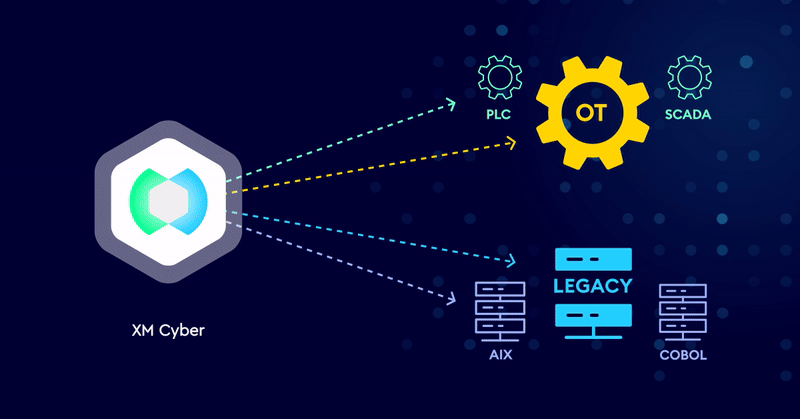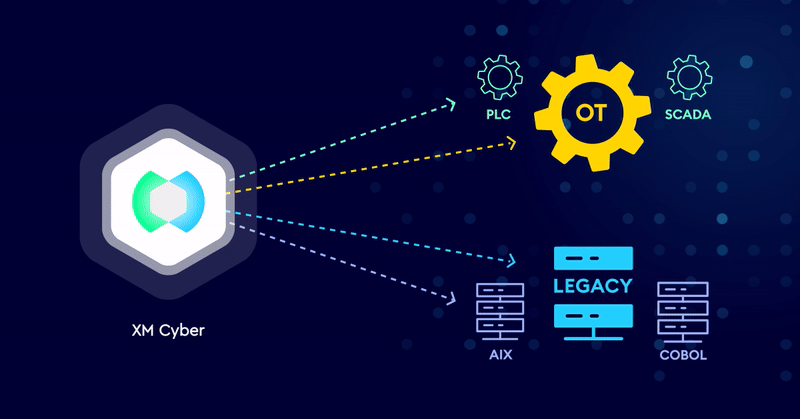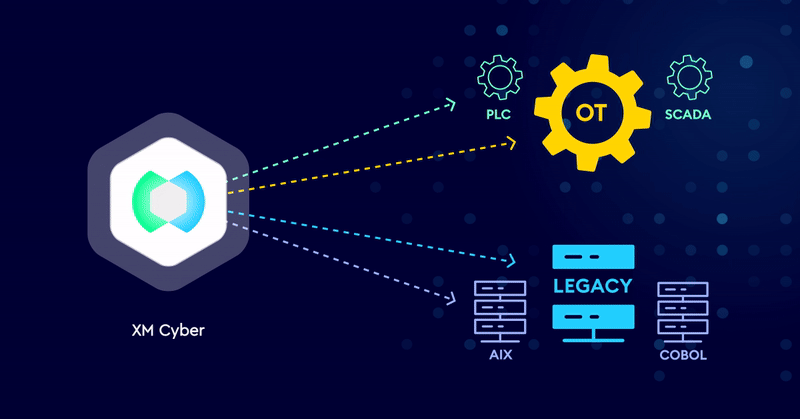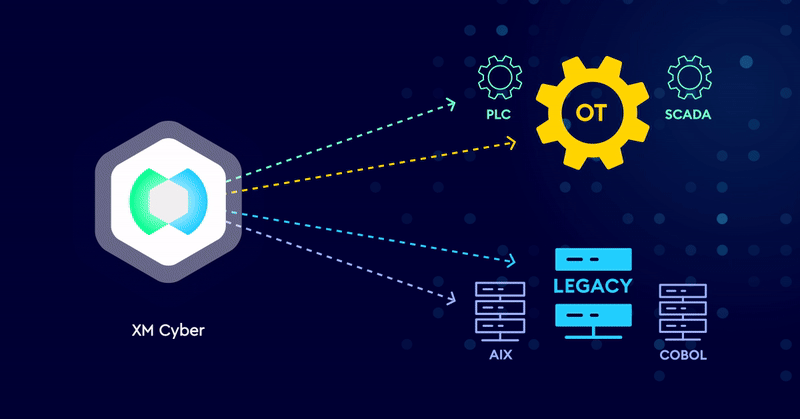
Breaking Attack Paths to Legacy and OT Systems
Securing Legacy and OT systems require a different approach. Outdated architecture, lack of software updates and patches, and systems that don’t use agents means…
Extend Exposure Management to Protect Legacy and OT Systems
As cyber threats evolve, security leaders must protect legacy and operational technology (OT) systems, in addition to the traditional IT infrastructure. Industries such as…
XM Cyber Exposure Management for Legacy Systems
Applying Exposure Management to Secure Legacy Systems Legacy systems like AIX or COBOL are essential for daily operations in industries like finance and insurance,…
XM Cyber Exposure Management for Operational Technology
Applying Modern Exposure Management to Secure OT Systems Operational Technology (OT) environments are a critical element of enterprises including manufacturing, petrochemical processing, and healthcare,…