FOCUS EFFORTS. RESOLVE VULNERABILITIES.
Vulnerability Risk Management
XM Cyber provides a unique approach to vulnerability management, with dynamic and continuous CVE mapping that allows you to seamlessly pivot security context from a traditional approach to a transformative risk-based vulnerability management construct. Prioritize your viewpoint of vulnerabilities from exploit likelihood to business impact risk and streamline the mobilization of remediation efforts, with rich contextual guidance, to justify action and proactively accelerate security operations.
The Problem with Traditional Vulnerability Management
Despite many advancements in vulnerability management, it has proven to be increasingly ineffective as attack surfaces evolve. Traditional methods generate a high volume of unnecessary noise and false positives due to inaccurate scanning methods. This makes it challenging for security teams to prioritize efforts and justify the time and resources to address them promptly.
Diverse assets types, spread across a distributed attack surface, leads to gaps in coverage of VA scans
Viewing risk posture by individual asset context, limits effective analysis and remediation
Unclear ownership and the lack of justification make it difficult to coordinate remediation efforts
NAVIGATING THE PATHS OF RISK
Are You Focused on the Right Vulnerabilities?
Remote code executable CVEs equate to less than 11% of critical security exposures identified each month for an average organization. To find out more, download The State of Exposure Management Research Report 2024.
CHANGE THE WAY YOU WORK
The Next Generation of Risk-Based Vulnerability Management
Move from Traditional to Transformative RBVM
Get flexible contextual views of vulnerabilities by device, software or products, with a unique prioritization logic combining CVE Severity, EPSS, and their impact risk to business-critical assets.
Seamlessly pivot your security viewpoint from a traditional RBVM approach, to a Transformative attack centric view using the XM Attack Graph Analysis™, to prioritize the vulnerabilities that present the great risk to the business.
Continuous Dynamic CVE Mapping
Move away from scheduled scanning, to the next generation of vulnerability assessment, which provides continuous discovery and reassessment of vulnerabilities, powered by a dynamic dictionary and comprehensive database of Common Vulnerabilities and Exposures (CVEs)
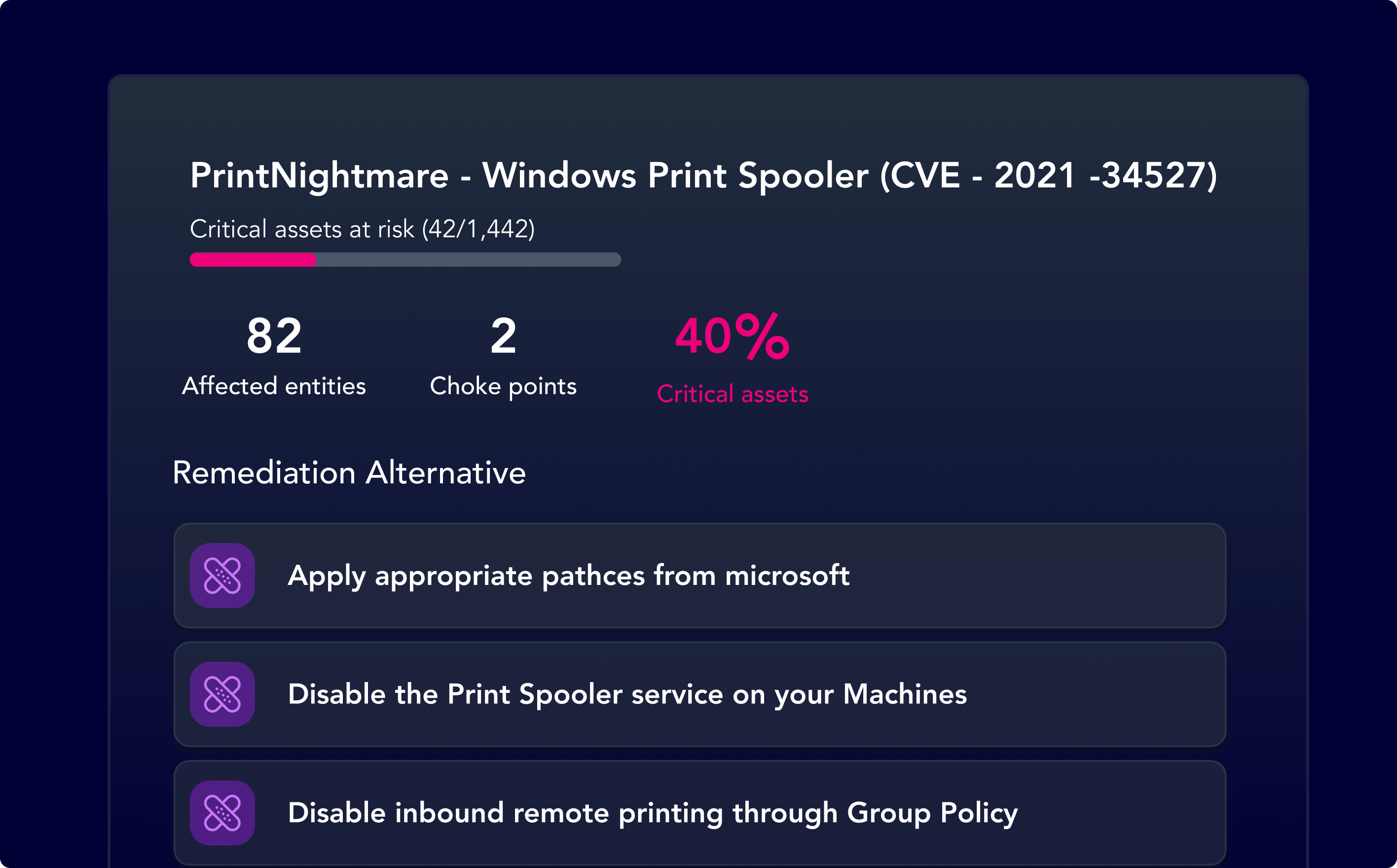
Closed-loop CVE Remediations
Zero-in on high-risk vulnerabilities and their impact to critical assets across the enterprise and leverage remediation guidance to combat risk more effectively
Ensure your teams have the justification, prioritization and knowledge to accelerate closed-loop vulnerability management.
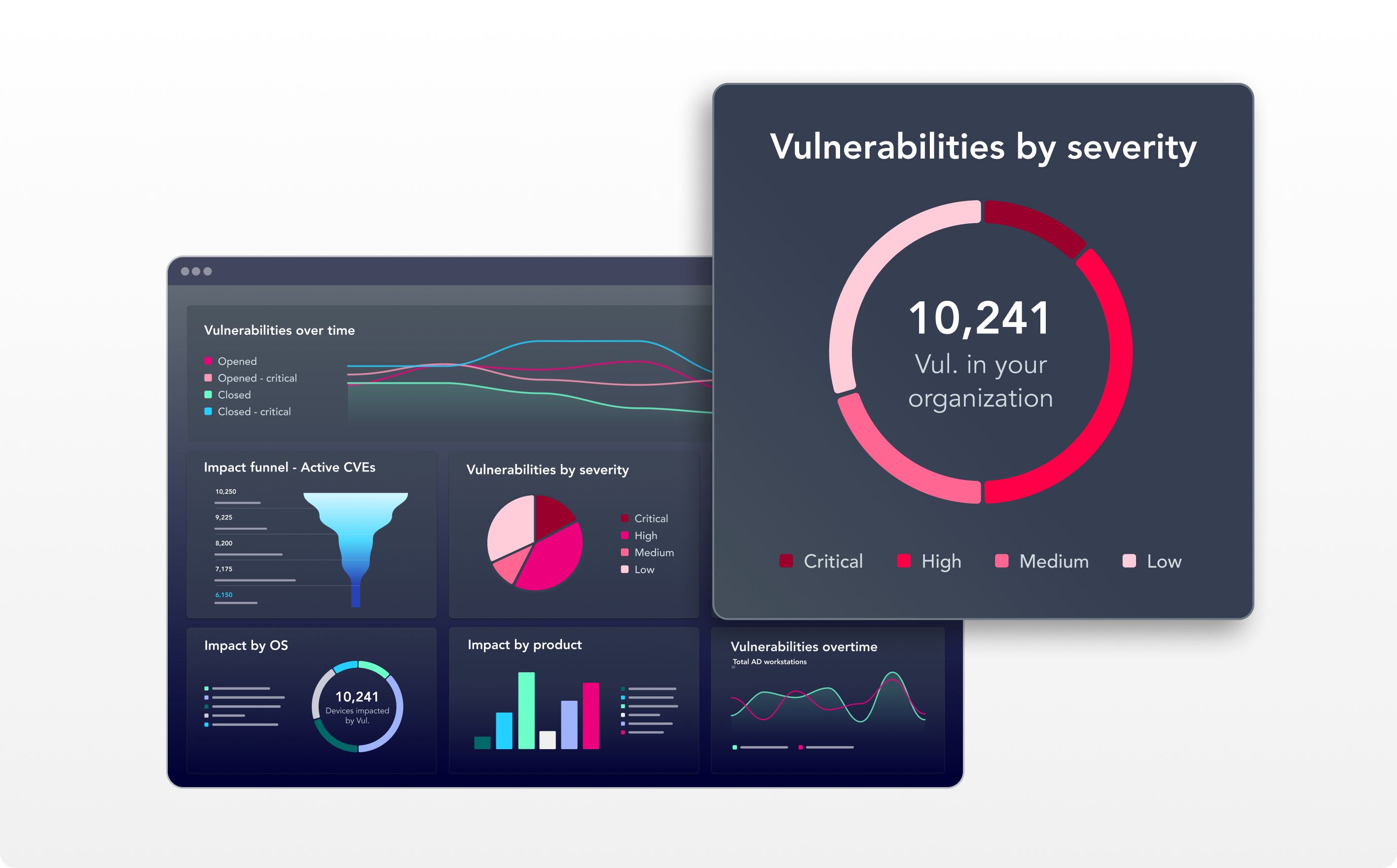
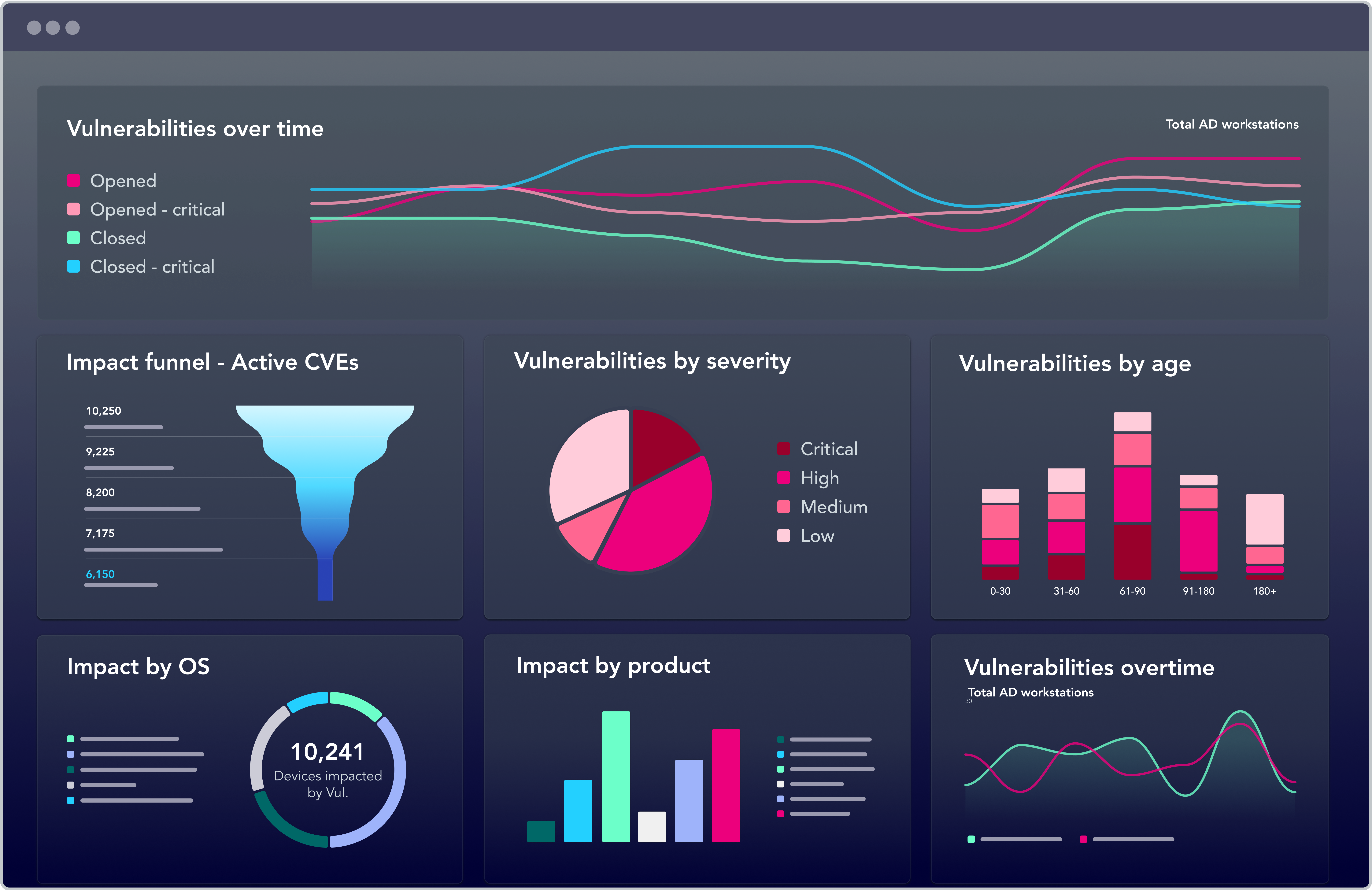
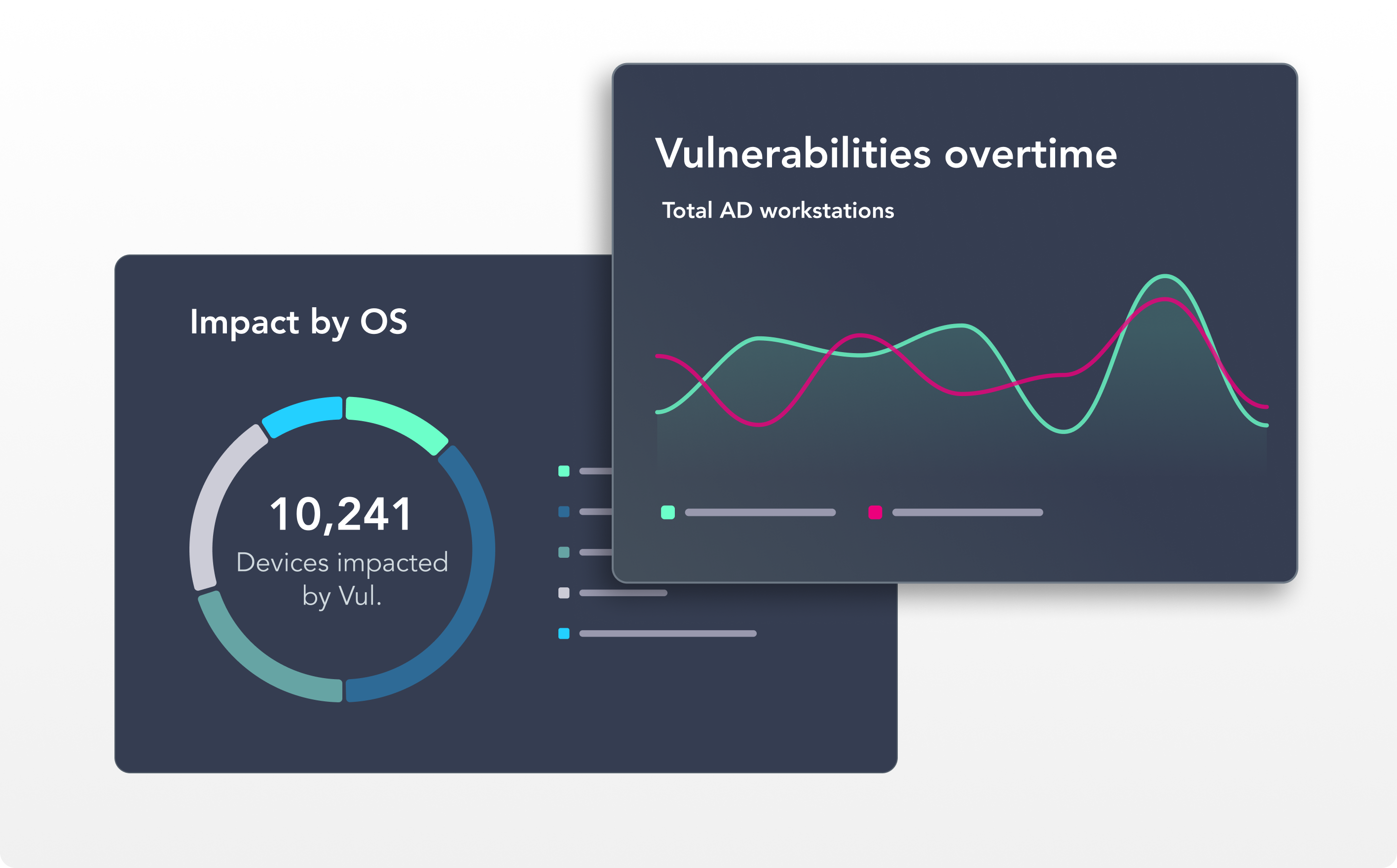
Vulnerability Risk Reporting & Reduction
Accelerate the time-to-value for reporting vulnerability risk with easy to use vulnerability Centrix Dashboards and reporting.
Zero-in on high-risk vulnerabilities and their impact to critical assets across the enterprise and leverage remediation guidance to combat risk more effectively.

Prioritization of CVEs Based on Exploitability Validation
Continuous and accurate validation of the exploitability of high-risk remote code executable CVEs, that integrates attack path logic into vulnerability prioritization to ensure you can focus remediation efforts on the vulnerabilities that present a true risk to the business.
MANAGE VULNERABILITIES THE XM CYBER WAY!
Vulnerability Management Optimization

Collaborative Security Optimization

Transformative Vulnerability Remediation
Seamlessly Pivot Security Context of CVE-based Risk
RBVM Remediation Efficiency

Impact-based CVE Risk Reporting