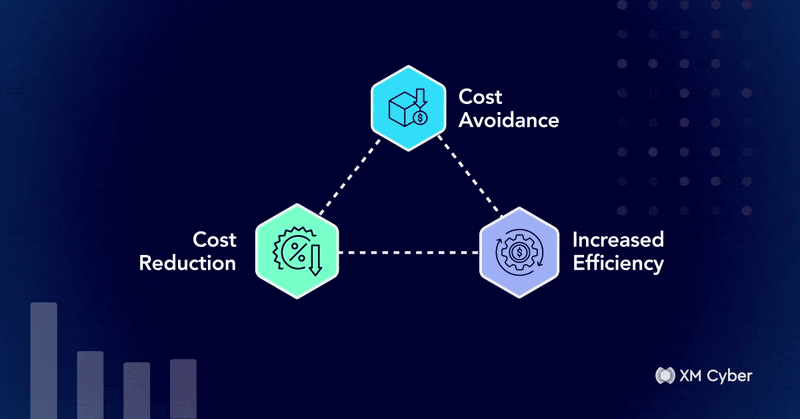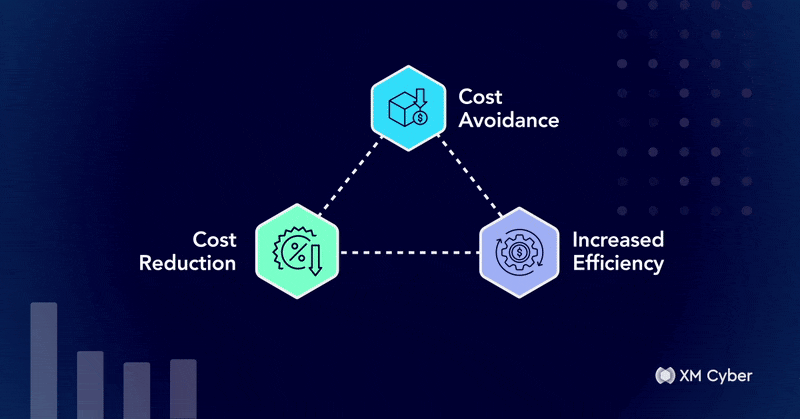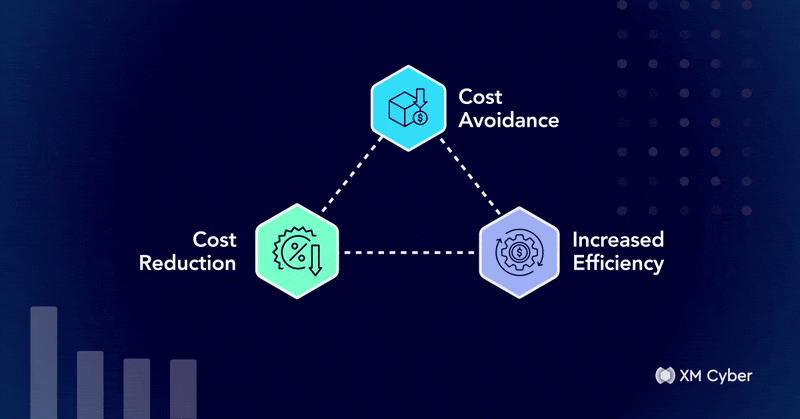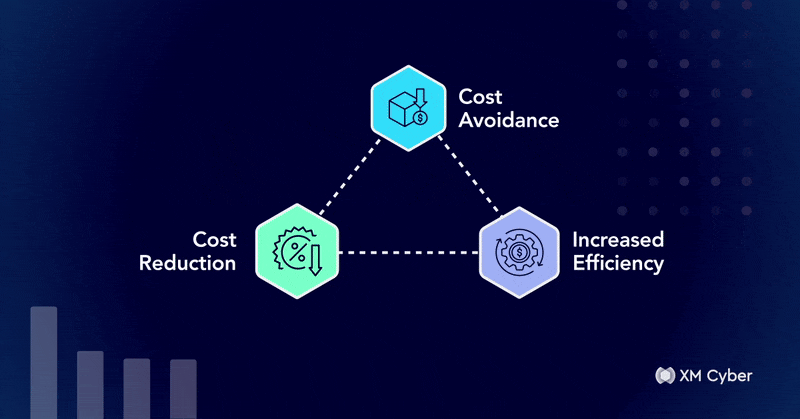
From Blocker to Enabler: Translating Cyber Risk into Business Value
When it comes to justifying security investments to the CFO, technical arguments aren’t enough. Any CFO worth their paycheck will prioritize financial impact, operational…
XM Cyber for Retail and Hospitality – Secure Customer Data and Operations, From Partner to Purchase
Reducing the Risk to Retail Operations Business Processes from On-Prem to Cloud Retailers and hospitality businesses are prime targets for cyber threats that exploit…
XM Cyber External Attack Surface Management
Connect the Dots. Eliminate Risk From External Exposures. Bridge the gap between your external attack surface and your internal environment. Move beyond simple discovery…
Continuous Exposure Management Platform
Protect your business-critical assets and demonstrate meaningful security posture improvements. The average organization has over 15,000 exposures in need of addressing each month. XM…
XM Cyber for Healthcare- Your Proactive Cybersecurity Care Plan to Cure Exposures
Patient Care and Cybersecurity for Hybrid Environments Patient care creates sensitive data, including Personally Identifiable Information (PII), Payment Card Industry (PCI), and Protected Health…
Cloud Transformation webinar – Don’t Get Caught CNAPPing!
Join our cloud security experts as we tackle these challenges head-on and uncover what true cloud transformation really looks like.
Ten Things You Need to Do Yesterday to Stay Compliant with NIS2
When it comes to the EU’s NIS2 Directive, meeting the basic requirements (according to the legislation in your company’s location) is only the first…
Seeing What Attackers See: How Attack Graphs Help You Stay Ahead of Cyber Threats
Cybersecurity can seem like a game of cat and mouse. Defenders try to anticipate attackers’ moves; attackers try to sneak through gaps in security…
CVE-2025-24813: Critical Apache Tomcat Vulnerability Already Being Exploited – Patch Now!
Overview Apache Tomcat, the free and open-source implementation of the Java Servlet, recently disclosed a critical vulnerability which is being tracked as CVE-2025-24813. This…
Four Real-Life Financial Service Attacks Paths and How we Blocked Them
Back in the wild west, there was this guy, Willie Sutton. Willie’s chosen profession wasn’t the town dentist-barber or saloon owner. Nope, he was…
XM Cyber for Financial Services – Proactively Reduce Risk and Protect Critical Financial Business Processes
Cybersecurity for High Value Assets Financial services firms face cyber threats targeting the transaction systems, databases, and apps that house high-value assets and sensitive…
Case Study: How ONNERA Group Gained Visibility and Reduced Cyber Risk with XM Cyber
Onnera Group head of IT infrastructure Iñaki Bizarro tells the story of why he selected XM Cyber and how continuously monitoring for the highest…